Resource access from a user's perspective
To provide security of data for a user who works within a range of tasks on specific business resources, IBM Security Identity Manager might provide one or more roles, and membership in one or more groups.
For example, a user in a business unit often has a title, or role that has a responsibility, such as buyer. The user might also be a member of a group that provides a view of tasks that the user can do, such as regional purchasing. The relationships are illustrated
in Figure 1.
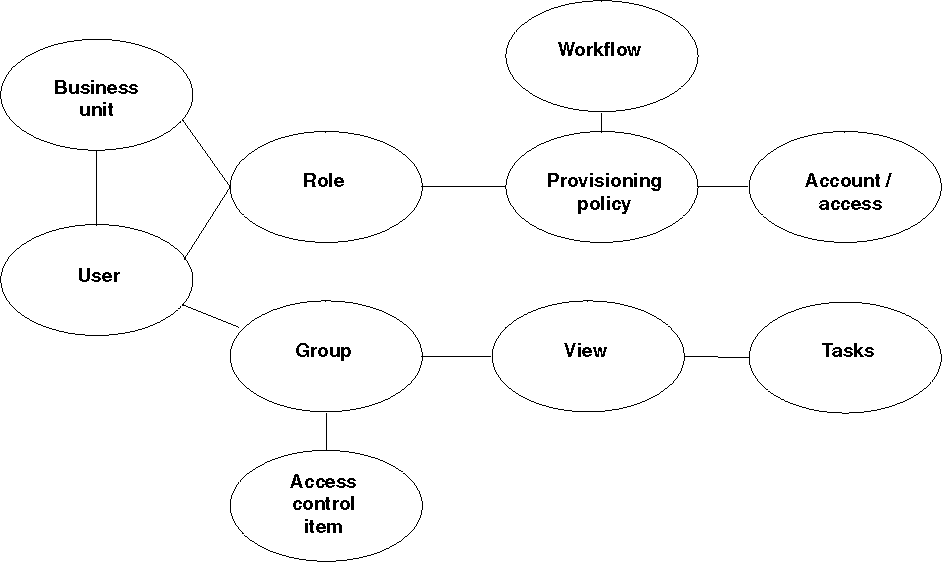
Each role has a related provisioning policy and workflow to grant the user to access one or more resources, such as accounts..
Each group has a view of specific tasks, and one or more access control items that grant specific operations and permissions to do the tasks. By using a form designer applet, we can also modify the user interface that a user sees. We might remove unnecessary fields for account, service, or user attributes.
- Groups
A group is used to control user access to functions and data in ISIM. - Predefined groups, views, and access control items
IBM Security Identity Manager provides predefined groups. The groups are associated with views and access control items. - Views
A view is a set of tasks that a particular type of user can see, but not necessarily do, on the graphical user interface. For example, it is a task portfolio of the everyday activities that a user needs to use ISIM. - Access control items
An access control item (ACI) is data that identifies the permissions users have for a specific type of resource. We create an access control item to specify a set of operations and permissions. We also identify which groups use the access control item. - Forms
A form is a user interface window used to collect and display values for account, service, or user attributes.
Parent topic: System security overview