Set up LDAP
Contents
- Overview
- Procedure
- LDAP Planning
- Install LDAP
- Required groups and users
- Portal administrator users
- Example of a customized directory structure
Overview
WebSphere Portal and WAS require some form of user registry. There are several possible ways to provide WAS and WebSphere Portal with access to a user registry:
- LDAP user registry
- Database user registry (for WebSphere Portal/Member Manager)
- Custom User Registry
Procedure
- Review planning considerations for LDAP
- Use existing LDAP software
- Use local or remote LDAP software
- Use SSL with the LDAP software
- Install the LDAP server
- Set up the LDAP server to work with WebSphere Portal.
- If required, configure LDAP over SSL. Otherwise, go to the next step.
- Configure WebSphere Portal to use the LDAP server:
- Configure WebSphere Portal for LDAP searches. Optional.
- Verify the connection between WebSphere Portal and the LDAP server.
- Refer to Troubleshooting if you encountered any errors.
LDAP Planning
WebSphere Portal can be configured to use an LDAP user registry to store user information and to authenticate users.
- Will you install a new LDAP server or use an existing LDAP server?
- Where will the LDAP user registry be installed?
You can install the LDAP server on the same machine as WebSphere Portal or on a remote machine. Installing the LDAP server on a remote machine can improve performance.
- Do you want to secure the data flowing between the LDAP server, WebSphere Portal, and WAS?
If so, set up LDAP over SSL.
- Will you use WebSphere Portal collaboration features?
If so, you may want to use Domino Directory for your LDAP server.
Install LDAP
The installation of an LDAP server is not part of the default WebSphere Portal installation, so install the LDAP server separately. You may install the LDAP server on the same machine as WebSphere Portal, or you may install the LDAP server on another remote machine.
Required groups and users
Set up the following users in your LDAP registry.
- An administrative user that is a member of the wpsadmins group.
- A Security Server ID account name and password for WAS security.
- An LDAP access account for WAS. This identity is used by WAS to access the LDAP user registry. If you keep the default values for the Bind Distinguished Name of WAS in the wpconfig.properties file, wpsbind will be used. The required privileges for this account in the user registry are as follows:
- Write:
Allow users or portal administrators to create and modify directory attributes through self-registration and self-care screens or the Manage Users and Groups portlet, the Bind DN (LDAPBindID) user must have permission to write and search the LDAP user registry that WebSphere Portal uses or the subtree of that directory rooted at the LDAP suffix.
- Read:
If you will not use any WebSphere Portal facilities to write to the user registry, but your user registry security policies do not allow anonymous searches of the directory, the Bind DN (LDAPBindID) user must have permission to read and search the LDAP user registry that WebSphere Portal uses or the subtree of that directory rooted at the LDAP suffix.
- Write:
- (This ID is not required when using LDAP with realm support.): An LDAP access account that Member Manager uses to access the LDAP directory. This does not have to be the root admin id for the directory, simply an ID that has sufficient privileges to the directory to allow the operations that WebSphere Portal will perform.
If WebSphere Portal only reads from the directory and does not make updates, an ID with read privileges to the directory is sufficient. If WebSphere Portal updates the directory (creates users or makes user profile updates to the directory) then an ID with write privileges is required.
- The WmmSystemId user is used for the protection of the Member Manager Enterprise Java Bean (EJB).
- If content management functions are configured, it is recommended to also create the following groups in the LDAP:
wpsContentAdministrators wpsDocReviewer
These groups should be created in the LDAP with the same authority as granted to the wpsadmins group.
See Adding portal administrators to the Domino Directory for details on adding users with special permissions to your Domino Domain.
Portal administrator users
You can select an existing LDAP user to act as the portal administrator.
If you want to create a new user to administer your portal, create the user before continuing.
To create a new user as the portal administrator, use your directory administration tools. Refer to the section appropriate to the directory server you are using for documentation on creating a new portal administrative user.
LDAP Relative Distinguished Name (RDN) prefixes, such as cn=, uid=, or ou=, should be entered in lowercase. Uppercase or mixed case can cause problems with subsequent case-sensitive queries of the database user registry and WebSphere Portal databases.
Example of a customized directory structure
The following is an example of one possible custom LDAP structure. This varies from the defaults listed in the other LDAP setup topics in several ways. It is more complex than the other default example LDAP trees; that is, there are more layers of names between the root and the leaves. It is also wider, with users and groups scattered in different places throughout the tree. Also, users and groups are sibling objects under a common parent in the layout. However, WebSphere Portal can be configured to accept this LDAP user registry layout. The example below helps you determine the appropriate values when configuring WebSphere Portal to work with your specific directory layout.
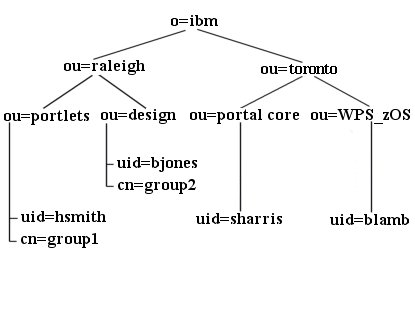
- LDAP suffix="o=ibm" or for a US-only portal, this value could be "ou=raleigh,o=ibm"
- user prefix="uid"
- user suffix="o=ibm" or for a US-only portal, this value could be "ou=raleigh,o=ibm"
- group prefix="cn"
- group suffix="o=ibm" or for a US-only portal,
"ou=raleigh,o=ibm"
- Portal administrator DN=
"uid=hsmith,ou=portlets,ou=raleigh,o=ibm"
- Portal administrator group=
"cn=group1,ou=portlets,ou=raleigh,o=ibm"
See Also:
- LDAP user registry
- Plan
- Install LDAP
- Set up LDAP over SSL
- Configure for LDAP without realm support
- Configure for LDAP with realm support
- Verifying
- IBM Tivoli Directory Server
- Domino Directory
- Active Directory
- Sun ONE
- Novell eDirectory
WebSphere is a trademark of the IBM Corporation in the United States, other countries, or both.
IBM is a trademark of the IBM Corporation in the United States, other countries, or both.
Tivoli is a trademark of the IBM Corporation in the United States, other countries, or both.