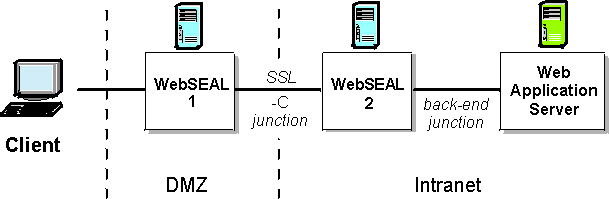
WebSEAL-to-WebSEAL junctions over SSL
ISAM supports SSL junctions between a front-end WebSEAL server and a back-end WebSEAL server. Use the -C option with the create command to junction the two WebSEAL servers over SSL and provide mutual authentication.
Example:
- pdadmin> server task web1-webseald-cruz create-t ssl -C -h serverA /jctA
Mutual authentication occurs in the following two stages:
- The SSL protocol allows the back-end WebSEAL server to authenticate to the front-end WebSEAL server through its server certificate.
- The -C option enables the front-end WebSEAL server to pass its identity information to the back-end WebSEAL server in a Basic Authentication (BA) header.
Additionally, the -C option enables single signon functionality provided by the -c option. The -c option allows us to place ISAM-specific client identity and group membership information into the HTTP header of the request destined for the back-end WebSEAL server. The header names include iv-user, iv-groups, and iv-creds. See Client identity in HTTP headers (-c).
The following conditions apply to WebSEAL-to-WebSEAL junctions:
- The junction is appropriate only with the -t ssl or -t sslproxy junction type.
- Both WebSEAL servers must share a common user registry. This configuration allows the back-end WebSEAL server to authenticate the front-end WebSEAL server identity information.
- If the WebSEAL-to-WebSEAL junction and the back-end application server junction both use the -j junction option (for junction cookies), a naming conflict can occur between the two junction cookies created by each of the two WebSEAL servers. (Refer to the diagram at the beginning of this section.) To prevent this conflict, configure the intermediary WebSEAL server (WebSEAL 2 in the diagram) to uniquely identify its junction cookie. On the intermediary WebSEAL server only, set the value of the hostname-junction-cookie stanza entry in the [script-filtering] stanza of the WebSEAL configuration file to "yes" (default is "no"):
Junction cookies allow WebSEAL to handle server-relative URLs generated on the client-side. These URLs lack knowledge of the junction point of the destination application. The junction cookie provides this information. For complete information on junction cookies, see Modification of server-relative URLs with junction cookies.
Parent topic: Advanced junction configuration
Related concepts
- Mutually authenticated SSL junctions
- TCP and SSL proxy junctions
- Stateful junctions
- Use of /pkmslogout with virtual host junctions
- Junction throttling
- Management of cookies
- Passing of session cookies to junctioned portal servers
- Support for URLs as not case-sensitive
- Junctions to Windows file systems
- Standard junctions to virtual hosts
- UTF-8 encoding for HTTP header data
- WebSockets
Related tasks