E-community overview
E-community single signon (sometimes referred to as ECSSO) is another implementation of cross-domain authentication in a ISAM environment. The goal of cross-domain authentication is to allow users to access resources across multiple servers in multiple domains without having to perform multiple logins.
An "e-community" is a group of distinct domains (Security Verify Access or DNS) that participate in a business relationship. These participating domains can be configured as part of one business (and perhaps using different DNS names for geographic reasons) or as disparate businesses with a shared relationship (for example, company headquarters, a life insurance company, and a financial management company).
In either scenario, there is always one domain that is designated the "home" or "owner" domain. In the case of participating businesses, the home domain owns the business agreements that govern the e-community.
In both scenarios, authentication information about the users who participate in the e-community (including the user names and passwords used for authentication) is maintained in the home domain. This arrangement allows a single point of reference for administration issues, such as help desk calls within the e-community that all refer to the home domain.
Alternatively, we can use the Web Portal Manager to delegate the management of this information that participating domains have responsibility for the administration of their own users.
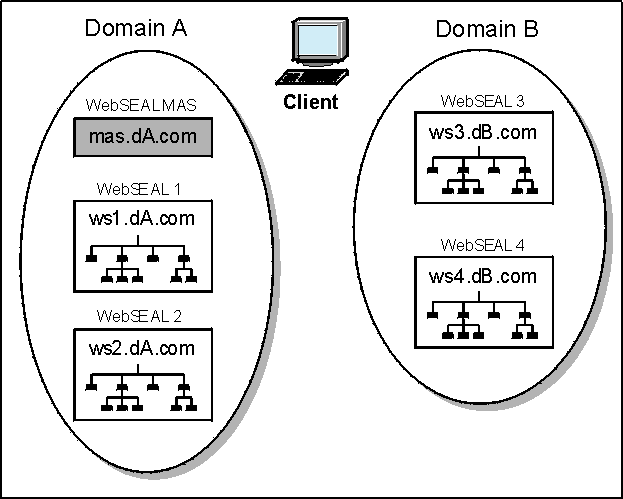
The diagram below illustrates a sample e-community with two participating
domains: domain A (dA.com) and domain B (dB.com). In this example,
domain A represents the home or owner domain. Domain B is a participating,
or "remote", domain.
 e-community model">
e-community model">
The home domain "owns" the users—that is, it controls the user's authentication information. Regardless of where a user makes a request for resources, the home domain is always where the user must authenticate.
Authentication occurs against a master authentication server (sometimes referred to as the MAS)—a server (or set of replica servers) located in the home domain and configured to authenticate all users. The diagram represents the MAS as mas.dA.com. The duty of the MAS should be restricted to providing authentication services. The MAS should not contain resources available to users.
After a user has successfully authenticated to the MAS, the MAS generates a "vouch-for" token. This token is passed back to the server where the user is making the request. The server treats this vouch-for token as proof the user has successfully authenticated to the MAS and can participate in the e-community.
The transfer of information between e-community domains is described in detail in the section E-community process flow.
Parent topic: E-community single signon concepts