SAML web single sign-on
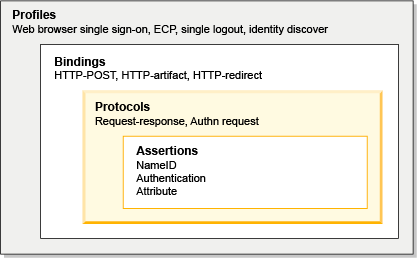
Security Assertion Markup Language (SAML) is used for representing user identity, authentication, and attribute information. A SAML assertion is an XML-formatted token used to transfer user identity and attribute information from the identity provider of a user to a trusted service provider as part of the completion of a single sign-on request. A SAML assertion provides a vendor-neutral means of transferring information between federation business partners. WAS supports SAML web single sign-on, and acts as a SAML service provider. A web user authenticates to a SAML identity provider, which produces an SAML assertion, and WebSphere SAML service provider consumes the SAML assertion to establish a security context for the web user. As a protocol, SAML has three versions: SAML 1.0, SAML 1.1, and SAML 2.0. SAML 2.0 is an enhancement to the previous SAML 1.x specifications, but is not backwards compatible.
SAML 2.0 has defined several binding options...
- HTTP redirect
- HTTP POST
- HTTP artifact
- SOAP
SAML 2.0 HTTP POST enables SAML protocol messages to be transmitted within an HTML form using base64-encoded content. SAML 2.0 HTTP POST enables the SAML provider and consumer to communicate using an HTTP user agent as an intermediary. HTTP POST is sometimes called Browser POST, particularly when used in single sign-on operations. SAML 2.0 Web Browser SSO Profile is defined to support web single sign-on. A web user either accesses a resource at a service provider, or accesses an identity provider such the service provider and desired resource are understood or implicit. The web user authenticates to the identity provider, which then produces an authentication assertion, and the service provider consumes the assertion to establish a security context for the web user.
Subtopics
- SAML single sign-on scenarios
- Enable the system to use the SAML web single sign-on feature
- Configure single sign-on partners
- SAML web single sign-on TAI custom properties
- Add SAML web single sign-on TAI using wsadmin
- Delete SAML web single sign-on identity provider (IdP) partner using wsadmin
- Delete SAML web single sign-on TAI using wsadmin
- Export SAML web service provider metadata using wsadmin
- Import SAML identity provider (IdP) partner metadata using wsadmin
- Display SAML identity provider (IdP) partner configuration using wsadmin
- Display SAML web single sign-on trust association interceptor (TAI) configuration using wsadmin
- Step by step guide to implement SAML 2.0 for Portal 8.5
Related information:
Profiles for the OASIS
Security Assertion Markup Language (SAML) V2.0
Bindings for the OASIS
Security Assertion Markup Language (SAML) V2.0
Assertions and Protocols
for the OASIS Security Assertion Markup Language (SAML) V2.0