Network Deployment (Distributed operating systems), v8.0 > Secure applications and their environment > Authenticate users > Use Microsoft Active Directory for authentication
Authenticate users with LDAP registries in a Microsoft Active Directory forest
Overview
Authenticate a user across multiple repositories, or across a distributed LDAP repository, such as a Microsoft Active Directory forest will fail if there is more than one match at run time. The default unique ID in Microsoft AD is the sAMAccountName attribute of a user. User IDs are guaranteed to be unique within a single domain. However they are not guaranteed across a tree or a forest. For example, suppose the user ID, smith, is added in the forest and in each subdomain. The search for...
-
sAMAccountName=smith
...returns three matches. WAS does not authenticate this user when there is more than one possible match in the registry.
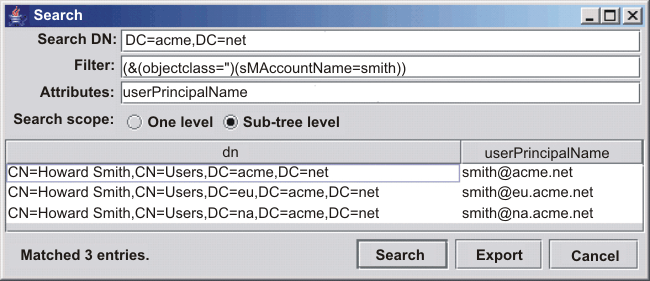
We can mitigate this condition by changing the user filter to be based on the userPrincipalName attribute of the user, which is unique across the forest, instead of being based on their sAMAccountName attribute. However, users must then know to log in using their userPrincipalName, which they might not know.
Establish a userPrincipalName user filter
- On a stand-alone LDAP registry, to search for userPrincipalName instead of sAMAccountName, go to...
-
Advanced Lightweight Access Protocol (LDAP) user registry settings
...and set something like...
- (&(objectClass=user)(userPrincipalName=%w))
On a federated repositories registry, Change the log-in property to: uid;cn.
- Click...
-
Security | Global security | Available realm definitions | Federated repositories | Configure
In a multiple security domain environment, click...
- Security domains | domain_name
Under Security Attributes, expand User Realm, and click Customize for this domain. Select the Realm type as Federated repositories and then click Configure.
- Under Related items, click Manage repositories.
- Under General Properties, add the following information:
Repository identifier forest Directory type Microsoft WIndows Server 2003 Active Directory Primary host name forest.acme.net Port 389 Failover server used when primary is not available None Bind distinguished name cn=wasbind, CN=Users, DC=ib Bind password ******** Login properties uid;cn
- Click...
- Click OK and Save to save the changes to the master configuration.
- On the LDAP repository configuration page, under Additional properties, click LDAP attributes.
- Click Add > Supported.
- Set...
Name userPrincipalName Property name cn Entity types PersonAccount - Click OK and Save to save the changes to the master configuration.
- On the dmgr, edit...
-
PROFILE_ROOT/conf/cells/<cell>/wim/config/wimconfig.xml
- Find the <config:attributeConfiguration> attribute
- Add the following lines:
<config:attributes name="userPrincipalName" propertyName="cn"> <config:entityTypes> PersonAccount </config:entityTypes> </config:attributes> - Save the wimconfig.xml file.
- On all of the nodes in the configuration, run...
-
cd PROFILE_ROOT/bin/
./syncNode.sh
Microsoft Active Directory Global Catalog
Options for finding group membership within a Microsoft Active Directory forest
Locate user group memberships in a LDAP registry
Authenticate users with LDAP registries in a Microsoft Active Directory forest
Use Microsoft Active Directory for authentication