WS-Security constraints - WAS v5.x
The WS-Security model used by WAS is the declarative model. A version 5.x application must be secured with WS-Security by defining the security constraints in the IBM extension deployment descriptors and in IBM extension bindings.
There is an important distinction between V 5.x and V6 and later applications. The information in this article supports V5.x applications only that are used with WAS V6.0.x and later. The information does not apply to V6 and later applications.
No APIs exist in WAS for programmatically interacting with WS-Security. However, Service Provider Programming Interfaces (SPIs) are available for extending some security runtime behaviors. We can secure an application with WS-Security by defining security constraints in the IBM extension deployment descriptors and in IBM extension bindings.
The development life cycle of a WS-Security-enabled application is similar to the Java EE model.
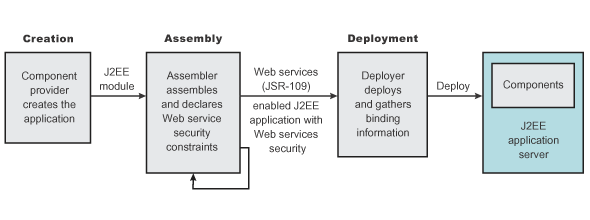
The WS-Security constraints are defined by the assembler during the application assembly phase if the Java EE application is Web services-enabled. Create, define, and edit the WS-Security constraints with an assembly tool.
WS-Security constraints
The security constraints for WS-Security are specified in the IBM deployment descriptor extension for Web services. The assembler defines these constraints during the application assembly phase, if the Java EE application is Web services enabled. Define the WS-Security constraints using an assembly tool. See more information about assembling applications.
The WS-Security run time acts on the constraints to enforce WS-Security for the SOAP message. The scope of the IBM deployment descriptor extension is at the EJB module or Web module level. There also are bindings associated with each of the following IBM deployment descriptor extensions:
Client (might be either a Java EE client (application client container) or Web services acting as a client)
- ibm-webservicesclient-ext.xmi
- ibm-webservicesclient-bnd.xmi
Server
- ibm-webservices-ext.xmi
- ibm-webservices-bnd.xmi
The IBM extension deployment descriptor and bindings are associated with each EJB module or Web module. See Figure 2 for more information. If Web services is acting as a client, then it contains the client IBM extension deployment descriptors and bindings in the EJB module or Web module.

The Web services security handler acts on the security constraints defined in the IBM extension deployment descriptor and enforces the security constraints accordingly. There are outbound and inbound configurations in both the client and server security constraints. In a SOAP request, the following message points exist:
- Sender outbound
- Receiver inbound
- Receiver outbound
- Sender inbound
These message points correspond to the following four security constraints:
- Request sender (sender outbound)
- Request receiver (receiver inbound)
- Response sender (receiver outbound)
- Response receiver (sender inbound)
The security constraints of request sender and request receiver must match. Also, the security constraints of the response sender and response receiver must match. For example, if we specify integrity as a constraint in the request receiver, then configure the request sender to have integrity applied to the SOAP message. Otherwise, the request is denied because the SOAP message does not include the integrity specified in the request constraint.
The four security constraints are shown in the following figure of WS-Security constraints.

Subtopics
Example: Sample configuration for WS-Security for a version 5.x application
Related concepts
WS-Security model in WASRequest sender
Request receiver
Response sender
Response receiver
Assembly tools
Related tasks
Assembling applications
Secure Web services for V5.x applications based on WS-Security