FIPS 140-2 support
Federal Information Processing Standards (FIPS) are standards and guidelines that are issued by the United States National Institute of Standards and Technology (NIST) for federal government computer systems. FIPS Publication 140-2 is a security standard used to accredit cryptographic modules.
FIPS 140-2 on the MobileFirst Server, and SSL communications with the MobileFirst Server
The IBM MobileFirst Platform Foundation server runs in an application server, such as the WebSphere Application Server. The WebSphere Application Server can be configured to enforce the use of FIPS 140-2 validated cryptographic modules for inbound and outbound Secure Socket Layer (SSL) connections. The cryptographic modules are also used for the cryptographic operations that are performed by the applications using the Java Cryptography Extension (JCE). Since the MobileFirst Server is an application that runs on the application server, it uses the FIPS 140-2 validated cryptographic modules for the inbound and outbound SSL connections.
When an IBM MobileFirst Platform Foundation client transacts a Secure Socket Layer (SSL) connection to a MobileFirst Server, which is running on an application server that is using the FIPS 140-2 mode, the results are the successful use of the FIPS 140-2 approved cipher suite. If the client platform does not support one of the FIPS 140-2 approved cipher suites, the SSL transaction fails and the client is not able to establish an SSL connection to the server. If successful, the client uses a FIPS 140-2 approved cipher suite.
The cryptographic module instances used on the client are not necessarily FIPS 140-2 validated. For options to use FIPS 140-2 validated libraries on client devices, see FIPS 140-2 on the MobileFirst client device for protection of data at rest in JSONStore and data in motion when using HTTPS communications. Specifically, the client and server are using the same cipher suite (SSL_RSA_WITH_AES_128_CBC_SHA for example), but the client side cryptographic module perhaps did not go through the FIPS 140-2 validation process, whereas the server side is using FIPS 140-2 certified modules.
See References for links to documentation to enable FIPS 140-2 mode in WebSphere Application Server.
FIPS 140-2 on the MobileFirst client device for protection of data at rest in JSONStore and data in motion when using HTTPS communications
Protection of data at rest on the client device is provided by the JSONStore feature of MPF. Protection of data in motion is provided by the use of HTTPS communication between the MobileFirst client and the MobileFirst Server. By default, these features use non-FIPS 140-2 validated libraries. But for iOS and Android devices, there is an option to use FIPS 140-2 validated libraries for the protection (encryption and decryption) of the local data stored by JSONStore and for the HTTPS communication to the MobileFirst Server. This support is achieved using an OpenSSL library that achieved FIPS 140-2 validation (Certificate #1747). To enable this option in a MobileFirst client project, select the FIPS 140-2 optional feature in the MobileFirst Studio.
There are some restrictions to be aware of:
- This FIPS 140-2 validated mode applies only to the protection (encryption) of local data stored by the JSONStore feature and protection of HTTPS communications between the MobileFirst client and the MobileFirst Server.
- This feature is only supported on the iOS and Android platforms.
- On Android, this feature is only supported on devices or simulators
that use the x86 or armv7 architectures.
It is not supported on Android using armv5 or armv6 architectures.
The reason is because the OpenSSL library used did not obtain FIPS
140-2 validation for armv5 or armv6 on Android.
- On iOS, it is supported on i386, armv7, and armv7s architectures. FIPS is not yet supported on 64-bit architecture even though MobileFirst library does support 64-bit architecture. Therefore, FIPS must not be enabled on 64-bit target platform when XCode Build Setting (Architecture) is also set to 64 bit.
- On Android, this feature is only supported on devices or simulators
that use the x86 or armv7 architectures.
It is not supported on Android using armv5 or armv6 architectures.
The reason is because the OpenSSL library used did not obtain FIPS
140-2 validation for armv5 or armv6 on Android.
- It only works with hybrid applications (not native).
- For HTTPS communications, only the communications between the MobileFirst client and the MobileFirst Server use the FIPS 140-2 libraries on the client. Direct connections to other servers or services do not use the FIPS 140-2 libraries.
- The use of the User Certificate Authentication feature is not supported with the FIPS 140-2 feature.
- The MobileFirst Application Center client does not support the FIPS 140-2 feature.
- The use of the Direct Update feature occurs
over a non-FIPS 140-2 protected channel. To use only a FIPS 140-2 protected channel, we must disable the Direct Update feature.
To disable the Direct Update feature, we can override the mobile security test in authenticationConfig.xml.in the server/conf directory.
<mobileSecurityTest name="mobileTests"> <testDirectUpdate mode="disabled" /> </mobileSecurityTest>
Use this mobile security test for Android and iOS environments as follows:
- <android securityTest="mobileTests" version="1.0">
or
- <iphone bundleId="com.TestHybridApp" version="1.0" securityTest="mobileTests">
The FIPS 140-2 optional feature supersedes the changes that were described in tutorial JSONStore - Encrypting sensitive data with FIPS 140-2 that was available for MPF v6.0.0 and earlier, Advanced client side development. This tutorial is now available on the Get Started page.
If we previously made the changes described in the tutorial, we must first save any other environment-specific changes that you made, and then delete and re-create the Android or iOS environments.
Figure 1. Example
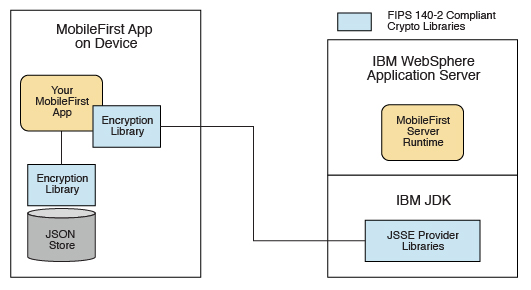
For more information about JSONStore, see JSONStore overview.
References
For information about how to enable FIPS 140-2 mode in WebSphere Application Server, see Federal Information Processing Standard support.
For the WAS Liberty profile, no option is available in the administrative console to enable FIPS 140-2 mode. But we can enable FIPS 140-2 by configuring the Java runtime environment to use the FIPS 140-2 validated modules. See Java Secure Socket Extension (JSSE) IBMJSSE2 Provider Reference Guide.
- Enable FIPS 140-2
To use the FIPS 140-2 feature in IBM Worklight v6.1.0, we must first enable the optional feature. - Configure FIPS 140-2 mode for HTTPS and JSONStore encryption
Learn about settings to configure FIPS 140-2 for encrypting data for HTTPS and JSONStore. - Configure FIPS 140-2 for existing applications
We must modify applications created in earlier versions of MPF to enable the FIPS 140-2 feature.
Parent topic: Federal standards support in IBM MobileFirst Platform Foundation