Plan for IBM Business Process Manager
Use the Interactive Installation and Configuration Guide to generate a set of installation and configuration topics customized your requirements.
The tool generates a single topic containing installation instructions pertaining to your scenario.
Installing into an existing WebSphere Application Server instance is not a path generated by the interactive guide tool. You'll have to use the information center for that.
Decide which configuration to install
IBM Business Process Manager (BPM) is available in four configurations: Advanced, Advanced: Process Server, Standard, and Express.
| Path | Capabilities | Install |
|---|---|---|
| First BPM project |
| BPM Express |
| Multiple projects | All the above, plus...
| BPM Standard |
| High-volume process automation. | All the above, plus...
| BPM Advanced |
| Using an earlier version of Process Server. |
Does not include Process Designer or Process Center. | BPM Advanced: Process Server |
Choose an operating system
You can install BPM Express server components on Windows or Linux on Intel systems, or, if you are an IBM Master Data Management customer, AIX. For BPM Standard and BPM Advanced, Windows, Linux on Intel and on System z, AIX, Solaris, and z/OS are supported.
Choose the type of installation
For BPM Express, using the product launchpad, the typical installation installs the software and configures a stand-alone profile. You do not need to create a profile later using PMT or manageprofiles.sh.
For all other BPM editions, using the product launchpad, the typical installation installs the software, configures the deployment manager and managed-node profiles, and configures a cluster with a single node and single server.
 The typical installation also installs Process Designer on the machine.
The typical installation also installs Process Designer on the machine.
With a custom installation using a graphical interface, you can customize all installation settings.
With a custom installation using a command line, you can run a command that specifies installation settings.
With a custom installation using a response file, you create a file that specifies installation settings, and run an installation command that calls it.
If you are migrating business data and applications from a previous version of BPM, use one of the custom installation types.
Environments
Process Center provides a repository for process assets, a runtime environment for testing performance, and a console for administering assets and deploying processes.
Process Server is a runtime environment for process applications, and a data warehouse for collecting performance. The Process Server administrative console is used for for managing the runtime environments and data warehouses.
Configuring environments for Process Server and Process Center is two separate activities: Configure an environment for one, and then another environment for the other.
When you deploy an application snapshot to a process server, the assets of that snapshot are moved from the Process Center repository to the selected process server, which can be connected to a Process Center or offline. Use the Process Center console or wsadmin to install the snapshot.
If the offline server option is chosen installation, Process Center is not installed. For examp,e you can choose to install an offline Process Server if you already have a Process Center installed. Once Process Server is installed, you can add the offline server to a Process Center.
If you are installing BPM Advanced: Process Server, the Process Center option is not available.
DB2 Express
For test or proof-of-concept environments, the installation process can automatically install an instance of IBM DB2 Express.
If you are installing onto Linux on System z, AIX, Solaris, or z/OS, the installation process does not offer to install DB2 Express; use a database server product that you have already installed or will install.
You cannot install DB2 Express on any system that already has DB2 installed on it.
Installation tools
For BPM Express , use BPMConfig to create new stand-alone profiles.
For BPM Standard, BPM Advanced, and BPM Advanced: Process Server, you can choose to configure the profiles and deployment environment all at the same time using BPMConfig, or separately using PMT and the Deployment Environment wizard. To set up nodes and customize security settings use PMT to create the profiles, and the Deployment Environment wizard to configure the deployment environment.
PMT is not supported on Solaris. Create the profiles using BPMConfig.
The interactive guide does not provide information for the path to take if you are augmenting existing profiles because your are installing into an existing WebSphere Application Server. Use manageprofiles.sh.
When creating profiles, use parameter values that match the values specified in the properties file that BPMConfig uses for the deployment environment setup. For example, if you set the value of cellName to Cell1, the properties file that BPMConfig uses must also use the Cell1 value. If you omit optional parameter values, PMT creates default values that must also match the required parameter values that are used by BPMConfig.
If the database is already created, you can choose to create the database tables during the creation of the deployment environment, using either BPMConfig or the Deployment Environment wizard.
Environment types
When you create a deployment environment by using the Deployment Environment Wizard, you can choose the type of deployment environment to create.
The deployment environment types enable different sets of function in the deployment environments:
| Standard Process Center | Administer process applications and toolkits authored in Process Designer. |
| Standard Process Server | Run process applications deployed from the Standard Process Center. |
| Advanced Process Center | Administer process applications and toolkits authored in Process Designer and IBM Integration Designer. |
| Advanced Process Server | Run processes, services, and SCA modules deployed from the Advanced Process Center. |
| Advanced-only Process Server | Run SCA modules only. Deployed from command line or WAS admin console. BPM equivalent to WebSphere Process Server. |
Requirements
- BPM Advanced system requirements
- BPM Standard system requirements
- BPM Express system requirements
- BPM Tools and Add-Ons requirements
Application considerations
Factors:
- Consider how process applications interact with existing services and back-end systems.
- Consider how process applications handle data and how data flows through the system.
Consider:
- Process application invocation patterns
How does the runtime environment handle asynchronous invocations. How does the SCA runtime environment leverage the message system.
Needs are determined by factors such as export types, component types, interactions between components, import types, resources needed such as databases or JMS resources, the need for business events, and the transmission mechanism.
- Types of business processes to implement (transactional business processes, interruptible business processes, non-interruptible business processes)
Non-interruptible business processes, or microflows, are short-running business processes that run in one transaction or without a transaction. Activities within one process are processed in a single thread.
Interruptible business processes, or macroflows, are long-running business processes that contain a set of activities, each of which is performed in its own transaction, and can include activities that require human intervention or calls to remote systems or both. Asynchronous activities cause a business process to be interruptible because these activities might take minutes, hours, or even days to complete.
Resource considerations
- Prepare a list of available hardware and software assets.
- Amount of installed memory
- Number and type of installed microprocessors
- External media
- Whether a particular unit can be upgraded
- Ensure all servers involved, both for the product and the databases, use the same network time protocol and are set to the same time.
- Itemize currently installed software and database applications.
- Function
- Breadth of use across the company
- Security requirements
- Configure user IDs with required authorizations to install.
Development and deployment version levels
Generally, applications deployed in a previous version of BPM can run on the next available version of BPM.
| Task | Supported | Notes |
|---|---|---|
| Deploy from WebSphere Integration Developer version 6.2.0 or 7.0.0, Integration Designer 7.5 or 8.0 to BPM V8.5. | Yes. | For WebSphere Adapters V6.2.0, install the interim fix titled Mandatory adapter fix for running 6.1 and 6.2 Adapters on WPS v7.0. If you do not plan to update the WebSphere Adapter to a V7.0 level, and you plan to continue to use the application with WebSphere Adapter V6.2.0, apply this interim fix on the source environment.
Websphere Adapter for SAP V6.0.2, V6.1.0, V6.1.2 and V6.2.0 are not supported on BPM V8.5. You must update Websphere Adapter for SAP to V7.0 before deploying. |
| Run BPM V8.5 artifacts on WebSphere Process Server 6.2.0 or 7.0, or BPM 7.5. | No. | Applications authored with IBM Integration Designer V8.5 cannot be published to or installed on WebSphere Process Server 6.2.0, 7.0 or BPM 7.5 (any prior release) servers.
Applications authored with WebSphere Integration Developer 6.2.0, 7.0, or IBM Integration Designer 7.5 or 8.0 and then generated in IBM Integration Designer V8.5 cannot be published to or installed on WebSphere Process Server 6.2.0, 7.0, or BPM 7.5 servers. Applications generated using serviceDeploy from BPM V8.5 servers cannot be installed on WebSphere Process Server 6.2.0, 7.0, or BPM 7.5 servers. |
The Process Designer and Process Center versions must match at all times. Version mismatches between the two components are not supported.
Process applications deployed to an earlier version of Process Center with only a fourth digit mismatch can be deployed to Process Server by using an offline deployment mechanism. An online deployment is not supported in the case of a version mismatch.
A later version of Process Center cannot deploy applications to an earlier version of Process Server.
Naming considerations
Profile naming considerations
Do not use any of the following characters when naming your profile:
- Spaces
- Special characters not allowed within the name of a directory, such as *, &, or ?.
- Slashes (/) or back slashes (\)
Double-byte characters are allowed.
For Windows, the installation directory path must be less than or equal to 60 characters. The number of characters in the profiles_directory_path\profile_name directory must be less than or equal to 80 characters.
Use a short path naming convention when you create a profile in a Windows environment to avoid the Windows 255 character path length limitation.
Naming guidelines
The following words are reserved, and should not be used:
- cells
- nodes
- servers
- clusters
- applications
- deployments
Naming guidelines for stand-alone server profiles
| Field name | Default value | Constraints | Description |
|---|---|---|---|
| Node name | shortHostNamenodeNumber where:
| Select any name you want. | |
| Server name | server1 | Use a unique name for the server. | The logical name for the server. |
| Host name | The long form of the DNS name. | Use a fully qualified host name addressable through the network. | Use the actual DNS name or IP address of your workstation to enable communication with it. |
| SSL certificate subject common name (CN) | Generated certificates use the host name as the subject common name (CN). | The common name on the certificate must match the host name for SSL verification. |
| Field name | Default value | Constraints | Description |
|---|---|---|---|
| Node name | shortHostNameCellManager NodeNumber where:
| Use a unique name for the deployment manager. | Used for administration within the deployment manager cell. |
| Host name | The long form of the DNS name. | Use a fully qualified host name addressable through the network. | Use the actual DNS name or IP address of your workstation to enable communication with it. |
| Cell name | shortHostNameCellCellNumber where:
| Use a unique name for the deployment manager cell. | All federated nodes become members of the deployment manager cell , which you name in the Node, Host, and Cell Names page of PMT. |
| SSL certificate subject common name (CN) | Generated certificates use the host name as the subject common name (CN). | The common name on the certificate must match the host name for SSL verification. |
Managed-node profiles...
| Field name | Default value | Constraints | Description |
|---|---|---|---|
| Node name | shortHostNamenodeNumber where:
| Use a unique name within the deployment manager cell. | Used for administration within the deployment manager cell to which the managed-node profile is added. Use a unique name within the deployment manager cell. |
| Host name | The long form of the DNS name. | Use a fully qualified host name addressable through the network. | Use the actual DNS name or IP address of your workstation to enable communication with it. |
| SSL certificate subject common name (CN) | Generated certificates use the host name as the subject common name (CN). | The common name on the certificate must match the host name for SSL verification. |
Host name considerations
The host name must resolve to a physical network node on the server. When multiple network cards exist in the server, the host name or IP address must resolve to one of the network cards. Do not use the generic identifier, localhost.
BPM is compliant with IPv4 and IPv6.
Do not use a server with a host name containing double-byte character set (DBCS).
Avoid using the underscore ( _ ) character in server names. If you have installed BPM on a server with an underscore character in the server name, access the server with its IP address until you rename it.
For SSL, the host name the server connects to must match the common name (CN) in the SSL certificate.
For coexisting nodes on the same computer with unique IP addresses, define each IP address in a DNS look-up table. Configuration files for servers do not provide domain name resolution for multiple IP addresses on a workstation with a single network address.
The value specified for host name is used as the value of the hostName property in configuration documents. Specify using one of the following formats:
- Fully qualified DNS host name string, such as xmachine.manhattan.ibm.com
- The default short DNS host name string, such as xmachine
- Numeric IP address, such as 127.1.255.3
Define the short name to 127.0.0.1 (local loopback) in the hosts file to run disconnected.
Prepare security authorizations
User IDs and passwords that have authority to install software on the systems.
User IDs, passwords, and roles needed for daily operations of the system:
- Administrative console user IDs.
- User IDs for each system bus.
- User IDS for Business Process Choreographer containers for authentication with Business Flow Manager and Human Task Manager.
- User IDs or groups for synchronous calls to authenticate with Business Flow Manager and Human Task Manager.
User IDs and passwords to access database tables.
User IDs and passwords to create database tables during installation.
Variables used in the documentation
You can install BPM and other components, and create profiles, in any directory for which you have write access. Multiple installations of BPM products or components require multiple locations.
Variables:
- install_root
- Installation location of BPM. BPM is always installed in the same location as the WAS Network Deployment installation with which it is associated.
- profile_root
- Location of an BPM profile.
Limitations of nonroot installers
Root and Administrator users can register shared products, and install into system-owned directories where globally shared resources are available to all users. Nonroot users cannot can install only into directories they own.
Default directories
install_root...
| Root | Nonroot |
|---|---|
| /opt/IBM/BPM/v8.5 | user_home/IBM/BPM/v8.5 |
profile_root...
| Root | Nonroot |
|---|---|
| /opt/IBM/BPM/v8.5/profiles/profile_name | user_home/IBM/BPM/v8.5/profiles/profile_name |
DB2 Express...
| Binary location | Instance location |
|---|---|
| /opt/ibm/BPM/v8.5/DB2 | Database instance is created under the bpminst user. For example: user_home/bpminst |
BPM and WAS...
| Root | Nonroot |
|---|---|
| /usr/IBM/WebSphere/AppServer | user_home/IBM/WebSphere/AppServer |
profile_name...
| Root | Nonroot |
|---|---|
| /usr/IBM/WebSphere/AppServer/profiles/profile_name | user_home/IBM/WebSphere/AppServer/profiles/profile_name |
Process Designer...
| Root | Nonroot |
|---|---|
| C:\IBM\ProcessDesigner\v8.5 | C:\IBM\ProcessDesigner\v8.5 |
Installation Manager...
| Root | Nonroot |
|---|---|
| /opt/IBM/InstallationManager | /user_home/IBM/InstallationManager |
Installation Manager agent data...
| Root | Nonroot |
|---|---|
| /var/ibm/InstallationManager | /user_home/var/ibm/InstallationManager |
Type of installation
Choose the typical installation option to install BPM interactively. Choose the custom installation option to install silently or if you will be installing on an existing WebSphere Application Server
For BPM Express, using the product launchpad, the typical installation installs the software and configures a stand-alone profile. You do not need to create a profile later using PMT or manageprofiles command.
For all other BPM editions, using the product launchpad, the typical installation installs the software, and configures the deployment manager and managed-node profiles, and configures a cluster with a single node and single server.
The custom installation can be performed interactively, or by choosing a silent installation.
After using the custom installation, you can use BPMConfig to generate database scripts, configure a deployment manager and one or more managed-node profiles, and create a pattern-based network deployment environment.
Instead of using BPMConfig, you can use PMT or manageprofiles.sh to configure one or more dmgr and managed node profiles. After profile creation, you can use the deployment environment wizard to generate a network deployment configuration.
Typical installation
Use to get full Business Process Manager features and functionality (for Express, Standard, or Advanced configurations) on a single machine.
You can specify the installation path and database type.
- Creates a single-cluster deployment environment that consists of a single node and single server.
- Can install DB2 Express if an existing database is not specified. DB2 Express is available only for Windows and Linux 32 and 64 bit systems, and the user must have administrative privileges (Administrator or root) and must not have another DB2 product installed.
- Automatically populates the database.
-
 A Process Center installation automatically installs Process Designer.
A Process Center installation automatically installs Process Designer.
- Creates shortcuts for the Process Center Administrative Console, Playback Server Administrative Console, Process Designer (on Windows), and WebSphere administrative console.
Custom installation
Choose custom installation...
- To install on an existing installation of WebSphere Application Server.
- If you require multiple cluster nodes.
- If you require complex deployment environment and database topologies.
- To perform a silent installation.
Plan the network deployment environment
Set up a network deployment environment involves many decisions, such as the number of physical workstations and the type of pattern you choose. Each decision affects how you set up the deployment environment.
Before you plan the deployment environment complete the following tasks:
- Choose a database type
- Identify available resources
- Identify necessary security authorizations
When you plan the layout of interconnected servers, you must make some decisions. These decisions influence trade-offs made between the available hardware and physical connections, the complexity of the management and configuration and requirements such as performance, availability, scalability, isolation, security, and stability.
- Identify the functional requirements of the deployment environment.
- Identify the features or runtime capabilities of the deployment environment.
Consider the components the deployment environment will support, such as the various process applications, toolkits, processes, or modules.
- Identify the component types that you will deploy.
Consider the component types and the interactions between components as part of the requirements.
- Identify the import and export implementation types and transports.
Consider the resources needed for the databases or Java™ Message Service (JMS) resources and the need for business events and the transmission mechanism.
- Identify any functional requirements that are not related to applications.
Consider security servers, routers, and any other hardware or software requirements to handle business events.
- Identify the features or runtime capabilities of the deployment environment.
- Identify the capacity and performance requirements for the environment.
- Decide on the number of physical servers that you need for each function.
- Identify the redundancy requirements for the environment.
- Identify the number of servers that you need for failover.
- Identify the number of routers that you need.
Your choice of router is influenced by exports of deployed modules, the types of queues you define on the service integration bus, Service Component Architecture (SCA) exports, and the type of load balancing that you want among your clusters. IBM provides an embedded router used for web services exports with SOAP/JMS transports, or JMS exports. However, if you choose not to use this embedded router provided by IBM, determine how to balance the load among your clusters, based on the technology that you are using.
- Design the deployment environment.
Decide on the pattern. For BPM, you can select one of two established topology patterns:
- Single Cluster
- Application, Remote Messaging, and Remote Support clusters
If your configuration supports multiple BPM and non-BPM products in addition to, and compatible with, BPM, the patterns of those products would be available to you when you create the deployment environment.
- Understand the methods available to you for configuring the deployment environment.
You can configure a standardized network deployment environment based on a topology pattern template included with the software, and you can implement it using BPMConfig or the Deployment Environment wizard.
You can use the Deployment Environment wizard to create clusters with the Single Cluster and (if applicable) Application, Remote Messaging, and Remote Support topology patterns.
Topologies
BPM topologies...
- Single Cluster
- Application, Remote Messaging, and Remote Support clusters
Databases
- Common database (CMNDB)
- Process database (BPMDB)
- Performance Data Warehouse database (PDWDB)
You might need to create and configure databases outside the installer.
Clusters
The following be deployed to a single cluster, or to different clusters.
| Application deployment target | Cluster to which you install applications (human tasks, business processes, and mediations). Can also provide messaging infrastructure and supporting infrastructure functions. If the applications contain human task or business process artifacts, install an Advanced Process Server or Advanced Process Center. |
| Supporting infrastructure | Cluster that includes business rules, selectors, human tasks, and business processes. The business rules are not tied to the Supporting infrastructure cluster, and can exist and work everywhere in the cell. The Business Rules Manager can be deployed on the supporting infrastructure cluster (in a three cluster configuration). The same principle applies to the human tasks and business processes. The human tasks and business processes run on the application deployment target cluster, because that is where the human task, and business process containers are configured. However, you administer processes and tasks from the Business Process Choreographer Explorer, which can reside on the supporting infrastructure cluster (in a three cluster configuration). |
| Messaging engine infrastructure | Cluster containing messaging engines. Provides asynchronous messaging support for applications and for the internal messaging needs of the BPM components. Enables communication among the nodes in the deployment environment. |
Single Cluster topology
All the functions of the deployment environment are combined into a single cluster.
One or more members of the cluster must also run the messaging engines required for asynchronous interactions. SCA internal asynchronous invocations, JMS, and MQ messaging bindings do not support multiple messaging engines in the same cluster.
Includes...
- Business Process Choreographer (BPC) container
- Process Server
- Business Rules manager
- Business Space
- Process Portal
- REST API Services
- Performance Data Warehouse
- Business Process Choreographer Explorer
Application, Remote Messaging, and Remote Support clusters topology
Deployment environment functions are divided among three separate clusters.
Application deployment target cluster...
- Business Process Choreographer (BPC) container
- Process Server
- Business Rules manager
- Business Space
- Process Portal
- REST API Services
Messaging infrastructure cluster...
- Service integration bus
- Messaging engine
Support infrastructure cluster...
- Performance Data Warehouse
- Business Process Choreographer Explorer
In a Application, Remote Messaging, and Remote Support topology pattern, the deployment environment functions are divided among three separate clusters. One cluster is used for applications, one cluster is used for messaging functionality, and one cluster for support functionality.
To ensure requests intended for Process Portal are directed to the correct cluster, we configure a routing server such as...
- IBM HTTP Server
- WebSphere Application Server proxy server
- reverse proxy server
BPM components for each configuration
| Component | Advanced | Standard | Express |
|---|---|---|---|
| Process Server | X | X | X |
| Performance Data Warehouse | X | X | X |
| Common database | X | ||
| Service Component Architecture (SCA) | X | ||
| Business Space | X | X | X |
| Process Portal | X | X | X |
| Business Process Choreographer | X | ||
| Business Process Choreographer Explorer | X | ||
| BPM messaging engine (service integration bus) | X | X | X |
Expand the topology
There are three ways to expand the topology...
- Add cluster members
You can add cluster members to each cluster independently or in combination. In a single-cluster topology, you can expand the cluster. In a three-cluster topology you can add new cluster members for any one, any two, or all three clusters.
- Add cells
If expanding existing clusters is not an appropriate solution, consider creating another deployment environment in another cell.
To add another cell, duplicate common cell-level configurations, such as global security settings. You use multiple consoles to manage applications, such as separate administrative consoles and failed event managers.
- Add deployment environments
Create two independent deployment environments for applications in the same cell.
Consider adding a second deployment environment when one of the following situations occurs:
- You must expand the capacity of the environment, but adding cluster members does not satisfy your requirements.
- You want to isolate process applications into separate JVMs, associating each application group with a specific set of JVMs.
- You want to set up multiple test environments quickly without having to configure security or nodes each time.
The second deployment environment is for Process Server only, not for IBM Process Center. You need one Process Center per cell, or the single repository experience is lost.
Run two deployment environments in the same cell is an advanced topology that requires research and planning.
If there is an issue with one application in the cell, it is not possible to apply an interim fix only to the affected deployment environment. Interim fixes affect all servers, deployment environments, and clusters in the cell. Fixes for one application might have an unanticipated effect on the other applications running in the cell.
Testing an interim fix from IBM is more difficult when several deployment environments are in the same cell. Separate cells help ensure that fixes do not break other applications.
You might have to bring down all your servers to apply interim fixes for one set of clusters, resulting in downtime across all the sets of clusters using the cell. Although the exact arrangement of servers varies, a common arrangement of servers is to have one member of each cluster on each node. In such an arrangement, all servers and cluster members that share the node are affected by the steps to apply the interim fix.
Application considerations with two different deployment environments in the same cell.
You cannot install two instances of the same Service Component Architecture (SCA) application in the cell. You can install many SCA applications, but they must have different module names. You can use the serviceDeploy utility to rename them.
As an example of this problem, if you create an environment with two deployment environments in the same cell and then try to import into both of them an BPM export (.twx) file that contains BPEL processes, the second import fails because the SCA module names are the same and an SCA module name must be unique within a cell.
There are several ways to manage this problem.
- You can use module naming conventions that incorporate the name of the target deployment environment.
- If you are deploying the modules as part of a process application in Process Center, you can use process app naming conventions that incorporate the name of the target deployment environment.
- If you are deploying directly as an EAR file, you can use module versioning where the version name uses a naming convention that incorporates the name of the target deployment environment.
For late binding to work, new versions of a BPEL business process or human task (template) must be deployed to the same deployment environment as the earlier version. The correct target to bind to must be found in the same deployment environment. Make sure that parent-child relationships between processes or between human tasks are scoped to the deployment environment. There are some relationships, like parent-child flows, that should not cross JVMs.
Each Process Portal has one view to each deployment environment and requires unique context roots. Consider whether to use a different web server for each deployment environment. If not, you must provide different virtual hosts to ensure unique context roots for applications.
Administration considerations with more than one deployment environment in the same cell
Each application cluster must have a corresponding support cluster and messaging engine cluster. Selecting the correct failed event manager to retry events might be difficult when you have more than one deployment environment. Ensure unique names for all applications that contain SCA modules such as BPEL processes, calendars, rules, selectors, and relationships. Ensure unique names for BPM applications as well as for customer applications. Add database, and schemas for each set of clusters. Each set of clusters requires database, and schemas for...
- Process database
- Performance Data Warehouse database
- Common database at the deployment environment level
You do not need separate database instances in DB2. If you use one database, you must provide separate user IDs for each Process Server and Performance Data Warehouse. These user IDs are used as the schema and keep the tables separate.
On-demand routing and dynamic cluster support
Migrating the WebSphere Virtual Enterprise technology to a WAS V8.5 Intelligent Management cell in IBM WAS V8.5 provides support for on-demand routing and dynamic clustering. WAS Network Deployment V8.5 provides virtualization capabilities that include intelligent load balancing and clustering techniques. It introduces the concepts of on-demand routing and dynamic clustering, which provide an on-demand flexible infrastructure for enterprise-scalable applications.
- On-demand routing
- The on-demand router (ODR) is an intelligent load balancer that receives, prioritizes, and distributes all the incoming requests across multiple servers. Unlike a regular load balancer that can route requests to an overloaded or hung server, the ODR has knowledge of the available processing capacity and health of the application servers and, based on this information, determines where the requests should be run.
- Dynamic clusters
- Route user requests from overloaded systems to systems that can handle the workload. Application servers can be started or stopped in the cluster to meet the current demand for applications deployed to the cluster.
Configure BPM for on-demand routing and dynamic clustering
To enable BPM to adjust workloads during peak times, you can augment its existing cluster topology with the dynamic cluster functionality provided with IBM WAS Network Deployment V8.5 or later.
See: BPM Advanced detailed system requirements.
Complete the following steps:
- Install the required BPM and IBM WAS interim fixes:
- Configure the ODR as a proxy server for BPM:
- Set up the BPM with the IBM HTTP Server:
- Install BPM V8.5 on three systems, for example, HOST130, HOST131, HOST132.
- Create one deployment manager node on HOST130, and two custom nodes on each of the HOST131 and HOST132 systems.
- Generate a three-cluster BPM deployment environment on these nodes using IBM DB2 V10.1.
- Create the ODR:
- Create another custom node on HOST130, which is the system that has the deployment manager, and then federate this node to the deployment manager.
- Log on to console...
-
http://<dmgr_host>:<dmgr_port>/ibm/console
- Click...
-
Servers | Server Types | On Demand Routers | New
...select the node corresponding to the ODR and complete the steps in the wizard to create and save the new ODR server.
- On the On-Demand Routers page, click Start to start the ODR server.
You can now log in to the Process Admin/portal/bpc using the host name and the port number of the ODR server.
- Configure the ODR server to work with IHS:
Ignore this step if you chose not to configure the IBM HTTP Server for BPM.
- In the administrative console, add the IHS server host name...
-
Servers | Server Types | On Demand Routers | On Demand Router Settings | On Demand Router Properties | On Demand Router Settings | Trusted security proxies
- Set the plug-in scope to Cell.
-
Servers | Server Types | On Demand Routers | On Demand Router Settings | On Demand Router Properties | On Demand Router Settings | Proxy Plugin Configuration Policy
- Click OK and then click Save.
- Restart the ODR server.
- Copy
- WAS_HOME/profiles/ODR_profiles_name/etc/Plugin-cfg.xml
...to...
- IHS_Plugin_Location/Plugins/config/webserver1
...on the IHS server.
- Restart the IHS server.
You can now log in to the Process Admin/portal/bpc using the host name and the port number of the IHS server.
- In the administrative console, add the IHS server host name...
- Set up the BPM with the IBM HTTP Server:
- Configure the BPM topology with dynamic clusters.
When configuring the dynamic clusters, to ensure that you can exploit all of the dynamic cluster features, IBM recommends converting each static cluster to a dynamic cluster and set the Minimum number of cluster instances to keep one instance started at all times for each dynamic cluster.
- Monitor the environment
Plan the database configuration
For BPM, three separate databases are required for the Process Server, the Performance Data Warehouse, and the common database components.
In BPM V8.5, the common (shared) database is split into two pieces. One is cell-scoped, used for the entire cell. The other is deployment-environment-scoped, and must be configured for each deployment environment.
The Process Server and Performance Data Warehouse components do not support case-sensitive databases. These databases must not be case-sensitive.
For Microsoft SQL Server and Oracle databases, the following restrictions apply:
- For SQL Server databases, components other than Process Server or Performance Data Warehouse require their databases be case-sensitive.
- For Oracle databases, the Process Server, Performance Data Warehouse, and Common database components must use a separate schema/user. They can use the same instance.
When configuring databases, the system default tablespaces are used. To use scripts that create custom tablespaces for the Business Process Choreographer and the Business Space components with DB2 and Oracle, see the usetablespaces property as described in the Database and cell properties section of Configuration properties for BPMConfig.
You can run one of the following commands:
- BPMConfig -create -sqlfiles properties_file_name -outputDir output_directory
- BPMConfig -create -de properties_file_name (when bpm.de.deferSchemaCreation is set to true)
The generated SQL files can be found in the output directory that you specified or in profile_root/dbscripts. The files include additional createTablespace*.sql files that you run before the createSchema*.sql files to create the tablespaces for Business Process Choreographer or Business Space. The generated createSchema*.sql files include the appropriate references to the tablespaces that you specified.
The following database types and providers are supported with BPM V8.5:
| Database type | JDBC provider |
|---|---|
| DB2 | DB2 Data Server JDBC Provider (XA) |
| Oracle | Oracle JDBC Provider |
| SQLServer | Microsoft SQL Server JDBC Provider |
JDBC drivers and locations
The JDBC driver used by BPM might not be the latest JDBC driver level delivered with the database product. Compare the latest version of the JDBC driver that is available from the database vendor with the JDBC driver that is delivered with BPM. If a later version is available, update to that driver.
| Server | Driver description | Driver location |
|---|---|---|
| DB2 | IBM DB2 Universal JDBC Driver 3.61.65 | install_root/jdbcdrivers/DB2 |
| IBM Data Server Driver for JDBC and SQLJ 4.11.69 | ||
| Oracle | Oracle JDBC Driver 11g 11.2.0.1.0 | install_root/jdbcdrivers/Oracle |
| SQL Server | Microsoft SQL Server JDBC Driver 4.0 | install_root/jdbcdrivers/SQLServer |
| Server | Driver description |
|---|---|
| Oracle | Oracle JDBC Driver 11g 11.1.0.6 |
Plan the number of databases
Databases are different from database schemas. Database schemas can share the same database. BPM components such as Messaging, BusinessSpace, and ProcessServer are assigned to database schemas. When no name conflicts occur between database objects, components can share the same database. Components such as Process Server and Performance Data Warehouse (PDW) do not have database schema support; therefore, they cannot share the same database.
The default database configuration always uses as few databases as possible.
BPM Standard
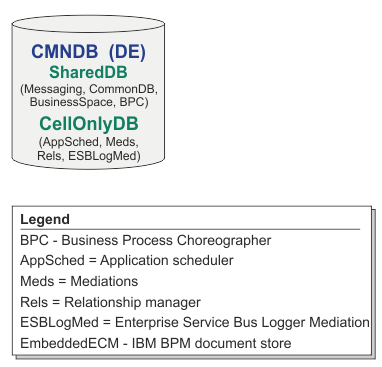
The default configuration for BPM Standard uses three databases, with the corresponding database schemas and assigned components.
- SharedDB schema - Database objects for the Messaging and BusinessSpace components.
- ProcessServerDB schema - Database objects for the ProcessServer and EmbeddedECM (BPM document store) components.
- PerformanceDB schema - Database objects for the Performance Data Warehouse (PDW) component.
In the following image, the database names are shown in blue, and the database schema names are shown in green.

For example, the configuration properties file for a Standard DE configuration can have the following configuration properties:
-
bpm.de.db.2.name=ProcessServerDb
bpm.de.db.2.dbCapabilities=ProcessServer,EmbeddedECM
bpm.de.db.2.databaseName=BPMDB
BPM Advanced
The default configuration for BPM Advanced uses three databases, with the corresponding database schemas and assigned components.
- The CellOnlyDB schema exists only in the Advanced and AdvancedOnly deployment environments, and is part of the CMNDB database by default. The CellOnlyDB schema Database objects for the Application scheduler (AppSched), Mediations (Meds), Relationship manager (Rels), and Enterprise Service Bus Logger Mediation (ESBLogMed) components.
- The SharedDB schema, which is also a part of the CMNDB database, Database objects for the Messaging (MEDB), CommonDB, BusinessSpace (BSpace), and Business Process Choreographer (BPC) components.
In the following image, the database names are shown in blue, and the database schema names are shown in green.

If you configure the optional Business Process Archive Manager, which allows you to move completed BPEL process instances and human tasks from the Business Process Choreographer database to a separate archive database, then you also require the BPARCDB database.
If you configured an Advanced-only Process Server deployment environment, the default configuration uses one database, CMNDB, with the corresponding database schemas (CellOnlyDB and SharedDB) and assigned components.
Database time zone and character set considerations
You should not change the time zone of the database server that you use for BPM. The national character set required for BPM is different from the Oracle default value.
Time zone considerations
Timestamps that are stored in the database are based on the time zone that is configured for the database server. Because of this dependency on the database time zone, you should not change the time zone configuration for the database server of an existing setup if timers are already scheduled. If you change the time zone configuration of the database server, the existing timers can trigger at an unexpected time.
If you have a second database server for failover or disaster recovery reasons, both database servers should be configured for the same time zone, regardless of where they are physically located.
Character set considerations for Oracle databases
BPM requires the Oracle database be Unicode enabled. In Oracle, there are two character set parameters that influence how CHAR and NCHAR types are stored in the database:
- For database character set (CHAR types), BPM requires AL32UTF8.
- For national character set (NCHAR types), BPM requires UTF8.
Note the national character set required for BPM is different from the Oracle default value.
Database privileges
Set database privileges to determine the authority that you must have to create or access your data store tables for each supported database management system.
DB2 database privileges
Set database privileges to determine the authority that you must have to create or access your data store tables for DB2 databases.
When you create database schemas using the typical installation or database scripts that are generated using BPMConfig, the user ID must have the authority to create tables. When the tables are created, you must have the authority to select, insert, update, and delete information in the tables.
| Privileges required to create objects | Privileges required to access objects |
|---|---|
| The user ID needs CREATETAB authority on the database, and CREATETS to create the table space. The user ID also needs CREATEIN and DROPIN privilege on the schema. The user ID needs system privileges CREATEDBA and CREATEDBC. The user ID also needs ALTER, DELETE, INDEX, INSERT, REFERENCES, SELECT, and UPDATE privileges on the created tables. | The user ID needs SELECT, INSERT, UPDATE, and DELETE privileges on the tables. The user ID also needs EXECUTE
ON PROCEDURE on stored procedures.
|
The installation privileges are the privileges required to install and configure the product. The runtime privileges are the database privileges required to run the product.
| Component | Installation privileges | Runtime privileges |
|---|---|---|
| Common DB | CREATE TABLE, CREATE INDEXTYPE, ALTER TABLE, INSERT, CREATE SEQUENCE, CREATE USER, ALTER USER, CREATE TABLESPACE | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE, USAGE ON SEQUENCE |
| Business Space | CREATE TABLE, CREATE INDEXTYPE, ALTER TABLE, INSERT, CREATE SEQUENCE, CREATE USER, ALTER USER, CREATE TABLESPACE | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE |
| Business Process Choreographer | CREATE TABLE, ALTER TABLE, CREATE VIEW, CREATE TABLESPACE, CREATE USER, CREATE PROCEDURE | SELECT, UPDATE, DELETE, INSERT |
| Messaging Engines | CREATE TABLE, CREATE INDEXTYPE | SELECT, UPDATE, DELETE, INSERT, DROP ANY TABLE
Messaging Engines use the TRUNCATE TABLE SQL statement, which might require the DROP ANY TABLE privilege. |
| Process Server or Performance Data Warehouse | Required to create the database:
Required to populate the database with our schemas and stored procedures:
Additional required privileges on the created tables:
| Required privileges on the tables in the Process Server and Performance Data Warehouse databases:
The runtime user must have EXECUTE ON PROCEDURE privileges on the six stored procedures in the createProcedure_ProcessServer.sql script. The runtime user requires all of the listed privileges on the Performance Tracking Server database as well. In addition, the user also must be able to create new tables in the Performance Tracking database, requiring the CREATETAB privilege. To read the system metadata tables, the SELECT permission is required on syscat.tables, syscat.views, syscat.columns, syscat.tabconst, and sysibm.sysdummy1. |
Syntax for creating a database, and assigning rights to a DB2 user:
-
create database @DB_NAME@ automatic storage yes using codeset UTF-8 territory US pagesize 32768;
connect to @DB_NAME@;
grant dbadm on database to user @DB_USER@;
UPDATE DB CFG FOR @DB_NAME@ USING LOGFILSIZ 4096 DEFERRED;
UPDATE DB CFG FOR @DB_NAME@ USING LOGSECOND 64 DEFERRED;
connect reset;
In the above example, replace @DB_NAME@ with the name to use for the created database, and @DB_USER@ with the user name to use for the database.
Oracle database privileges
Set database privileges to determine the authority that you must have to create or access your data store tables for Oracle databases.
When you create database schemas using the typical installation or database scripts that are generated using BPMConfig, the user ID must have the authority to create tables. When the tables are created, you must have the authority to select, insert, update, and delete information in the tables.
| Privileges required to create objects | Privileges required to access objects |
|---|---|
| The user ID needs sufficient privilege to create relational tables and indexes in the data store schema. The database also needs a space quota in the default table space of the owner of that schema. | The user ID needs the SESSION privilege to connect to the database. If the same user ID owns both the data store schema, and the component that is connecting to the database, the user ID has sufficient privilege to manipulate the tables. Otherwise, the user ID needs SELECT, INSERT, UPDATE, ALTER, and DELETE object privileges on the tables that make up the data store, and the DROP ANY TABLE system privilege to enable the use of the TRUNCATE TABLE statement. The user ID also requires the CREATE INDEX privilege. |
The installation privileges are the privileges required to install and configure the product. The runtime privileges are the database privileges required to run the product.
If you configure all the following components for a single Oracle database, you can create a superset of all the privileges specified for each component. If you configure the four components for numerous databases, you can set different privileges for each.
| Component | Installation privileges | Runtime privileges |
|---|---|---|
| Common DB | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges: CREATE USER, ALTER USER, CREATE ANY TABLE, ALTER ANY TABLE, DROP ANY TABLE, SELECT ANY TABLE, UPDATE ANY TABLE, INSERT ANY TABLE, DELETE ANY TABLE, CREATE ANY INDEX, DROP ANY INDEX, CREATE ANY VIEW, DROP ANY VIEW, CREATE ANY PROCEDURE, DROP ANY PROCEDURE, CREATE ANY SEQUENCE
The following privileges are for the situation when a DBA has created a Common DB user and that user creates the database objects, owns them, and uses them at runtime: CREATE TABLE, CREATE VIEW, CREATE PROCEDURE, CREATE SEQUENCE | The following privileges are for the situation when a DBA has created a Common DB user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
|
| Business Space | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges: CREATE USER, ALTER USER, CREATE ANY TABLE, ALTER ANY TABLE, DROP ANY TABLE, SELECT ANY TABLE, UPDATE ANY TABLE, INSERT ANY TABLE, DELETE ANY TABLE, CREATE ANY INDEX, DROP ANY INDEX, CREATE ANY VIEW, DROP ANY VIEW, CREATE ANY PROCEDURE, DROP ANY PROCEDURE
The following privileges are for the situation when a DBA has created a Business Space user and that user creates the database objects, owns them, and uses them at runtime: CREATE TABLE, CREATE VIEW, CREATE PROCEDURE | The following privileges are for the situation when a DBA has created a Business Space user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
|
| Business Process Choreographer | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges: CREATE USER, ALTER USER, CREATE TABLESPACE, CREATE ANY TABLE, ALTER ANY TABLE, DROP ANY TABLE, SELECT ANY TABLE, UPDATE ANY TABLE, INSERT ANY TABLE, DELETE ANY TABLE, CREATE ANY INDEX, DROP ANY INDEX, CREATE ANY VIEW, DROP ANY VIEW, CREATE ANY PROCEDURE, DROP ANY PROCEDURE
The following privileges are for the situation when a DBA has created a Business Process Choreographer user and that user creates the database objects, owns them, and uses them at runtime: CREATE TABLE, CREATE VIEW, CREATE PROCEDURE. | The following privileges are for the situation when a DBA has created a Business Process Choreographer user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
|
| Common Event Infrastructure (CEI) | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges: CREATE USER, ALTER USER, CREATE INDEXTYPE, ALTER ANY TABLE, ALTER SESSION, CREATE TABLESPACE, CREATE PROFILE, CREATE ROLE, CREATE TEMPORARY TABLESPACE
The following privileges are for the situation when a DBA has created a Common Event Infrastructure user and that user creates the database objects, owns them, and uses them at runtime: CREATE TABLE, CREATE VIEW, CREATE PROCEDURE. | The following privileges are for the situation when a DBA has created a Common Event Infrastructure user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
|
| Messaging Engines | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges: CREATE USER, ALTER USER, CREATE ANY TABLE, ALTER ANY TABLE, DROP ANY TABLE, SELECT ANY TABLE, UPDATE ANY TABLE, INSERT ANY TABLE, DELETE ANY TABLE, CREATE ANY INDEX, DROP ANY INDEX
The following privileges are for the situation when a DBA has created a Messaging Engines user and that user creates the database objects, owns them, and uses them at runtime: CREATE TABLE | The following privileges are for the situation when a DBA has created a Messaging Engines user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
Messaging Engines use the TRUNCATE TABLE SQL statement, which might require the DROP ANY TABLE privilege. If you prefer not to give the user this privilege, you can avoid it, at a performance cost, by using tuning. |
| Process Server | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges:
The following privileges are for the situation when a DBA has created a Process Server user and that user creates the database objects, owns them, and uses them at runtime.
| The following privileges are for the situation when a DBA created a Process Server user and that user creates the database objects, owns them, and uses them at runtime.
|
| Performance Data Warehouse | The following privileges are for the situation when a DBA creates users and all the database objects for those users. The DBA requires the following privileges:
The following privileges are for the situation when a DBA has created a Performance Data Warehouse user and that user creates the database objects, owns them, and uses them at runtime. explicit privileges:
implicit privileges (included in the ownership of the database objects):
| The following privileges are for the situation when a DBA created a Performance Data Warehouse user and that user creates the database objects, owns them, and uses them at runtime.
explicit privileges:
implicit privileges (included in the ownership of the database objects):
All schemas or users that are creating or migrating BPM profiles must have access to the DBMS_LOCK package. Set the Execute permission on the DBMS_LOCK package for the Oracle user or schema that is using the performance database as shown in the following example:
In this example, schema_name is the user ID used for the performance database. |
Syntax for assigning rights to an Oracle user:
-
CREATE USER @DB_USER@ IDENTIFIED BY @DB_PASSWD@;
grant connect, resource, unlimited tablespace to @DB_USER@;
grant view to @DB_USER@;
grant javauserpriv to @DB_USER@;
grant execute on dbms_lock to @DB_USER@;
SQL Server database privileges
Set database privileges to determine the authority that you must have to create or access your data store tables for SQL Server databases.
Permissions in SQL Server are assigned to roles which can be assigned to users, similar to windows user groups. There are two types of roles:
- Server roles provision database server related permissions such as backup, shutdown, creating new databases, managing logins, and linking to other servers.
- Database roles provision more traditional database permissions such as table access and those listed below.
You can be a member of multiple roles such that you can combine the permissions of different fixed roles to find just the right combination for your requirements.
Assign the BPM database user to the following three roles:
The database must be created by the database administrator who can then assign these roles to the database user for BPM.
- db_ddladmin
- db_datawriter
- db_datareader
For information about the permissions provided by these roles, see documentation from Microsoft.
When you create database schemas using the typical installation or database scripts that are generated using BPMConfig, the user ID must have the authority to create tables. When the tables are created, you must have the authority to select, insert, update, and delete information in the tables.
The above three fixed database roles cover 80% of the requirements, the remaining permissions are:
- •CREATE INDEXTYPE: No INDEXTYPE. but db_ddladmin can create indexes and specify the type
- •CREATE TABLESPACE: No TABLESPACE but similar concepts are WORKLOAD GROUP, RESOURCE POOL, and PARTITION SCHEME
- •ALTER LOCK TABLE: This functionality is available through Lock hinting using the read or write commands (eg SELECT * FROM tbl name WHERE TABLOCKX
- •CREATE SEQUENCE: This command is in the SQL Server 2012 documentation but not 2008 R2
| Privileges required to create objects | Privileges required to access objects |
|---|---|
| The user ID ideally requires DB OWNER privileges on the data stores used for BPM. | Configure the SQL Server for SQL Server and Windows authentication so that authentication to be based on an SQL server login ID and password.
The user ID must be the owner of the tables, or a member of a group that has sufficient authority to issue TRUNCATE TABLE statements.
|
The installation privileges are the privileges required to install and configure the product. The runtime privileges are the database privileges required to run the product.
| Component | Installation privileges | Runtime privileges |
|---|---|---|
| Common DB | CREATE TABLE, ALTER TABLE, INSERT, CREATE USER, ALTER USER | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE |
| Business Space | CREATE TABLE, ALTER TABLE, INSERT, CREATE USER, ALTER USER | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE |
| Business Process Choreographer | CREATE TABLE, ALTER TABLE, CREATE VIEW, CREATE USER, CREATE PROCEDURE | SELECT, UPDATE, DELETE, INSERT |
| Messaging Engines | CREATE TABLE | SELECT, UPDATE, DELETE, INSERT, DROP ANY TABLE
Messaging Engines use the TRUNCATE TABLE SQL statement, which might require the DROP ANY TABLE privilege. |
| Process Server | CREATE TABLE, SELECT, INSERT, UPDATE, DELETE TABLE, DROP TABLE, CREATE INDEX, CREATE VIEW, DROP VIEW, CREATE PROCEDURE, CREATE USER, ALTER USER | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE, DROP TABLE, DROP VIEW |
| Performance Data Warehouse | CREATE TABLE, SELECT, INSERT, UPDATE, DELETE TABLE, DROP TABLE, CREATE INDEX, CREATE VIEW, DROP VIEW, CREATE PROCEDURE, CREATE USER, ALTER USER | SELECT, UPDATE, DELETE, INSERT, CREATE VIEW, CREATE PROCEDURE, DROP TABLE, DROP VIEW |
Syntax for creating BPMDB and PDWDB databases in SQL Server is CREATE DATABASE @DB_NAME@ COLLATE SQL_Latin1_General_CP1_CI_AS;
Syntax for creating the CommonDB database in SQL Server is CREATE DATABASE @DB_NAME@ COLLATE SQL_Latin1_General_CP1_CS_AS;
- The BPMDB and PDWDB databases must be created as case-insensitive. Use the command COLLATE SQL_Latin1_General_CP1_CI_AS, where CI is the COLLATE attribute value that is applicable for the case-insensitive databases.
- The CommonDB database must be created as case-sensitive. Use the command COLLATE SQL_Latin1_General_CP1_CS_AS, where CS is the COLLATE attribute value that is applicable for the case-sensitive databases.
Syntax for creating the users and schemas for the SQL Server databases is as follows:
-
USE master GO
CREATE LOGIN @DB_USER@ WITH PASSWORD='@DB_PASSWD@'
GO
USE @DB_NAME@
GO
CREATE USER @DB_USER@ FOR LOGIN @DB_USER@ WITH DEFAULT_SCHEMA=@DB_USER@
GO
CREATE SCHEMA @DB_USER@ AUTHORIZATION @DB_USER@
GO
EXEC sp_addrolemember 'db_ddladmin', @DB_USER@;
EXEC sp_addrolemember 'db_datareader', @DB_USER@;
EXEC sp_addrolemember 'db_datawriter', @DB_USER@;
For Performance Data Warehouse users, note the following restrictions:
- The user cannot be assigned to the system administrator (SYSADMIN) role.
- The user must be mapped to the master database with the SqlJDBCXA user role.
See the WebSphere Application Server page in the related reference.
User ID or schema name privileges
During the installation of BPM, you can use the default schema name and user ID privileges to install the databases. However, the database design might require separate user ID or schema name privileges.
Scenario for a single user ID or schema name privileges
BPM requires a minimum of one user ID or schema name that can create tables and to select, insert, update, and delete rows in those tables. You can use PMT or the installer to create the databases.
| Database tables | Default database name with DB2 | User ID or schema name |
|---|---|---|
| Common database tables | CMNDB | BPM provides a user ID during installation. |
| Business Process Choreographer | BPEDB | BPM provides a user ID during installation. |
| Messaging tables | MEDB | BPM provides a schema name during installation. |
If the database design has different properties, you might need multiple user ID and schema name privileges.
Scenario 1 for multiple user ID or schema name privileges
In this scenario, you use a schema name that is the same as the user ID privileges, but you do not use the default schema name or a user ID specified during installation. This single user ID can access all of the database, and also create all needed tables.
| Schema name | dog |
| Schema name for SCA.SYSTEM ME | dogSYS |
| Schema name for SCA.APP ME | dogAPP |
| Schema name for Event ME | dogEvent |
| Schema name for BPC ME | dogBPC |
| User ID to create schemas | dog |
| User ID to select, insert, update, and delete schemas | dog |
Scenario 1: Multiple user ID or schema
| Database tables | Database name with DB2 | Schema name | User ID to create tables | User ID to select, insert, update, and delete rows |
|---|---|---|---|---|
| Common database tables | Supply this value in...
| Schema name is the same as the user ID used to select, insert, update, and delete rows. | This value is the same as the user ID used to select, insert, update, and delete rows. | Supply this value in...
|
| Business Process Choreographer tables | Supply this value twice:
| Schema name is the same as the user ID used to select, insert, update, and delete rows. | This value is the same as the user ID used to select, insert, update, and delete rows. | Supply this value twice:
|
Scenario 2 for multiple user ID or schema name privileges
In this scenario, use the same schema name and user ID to select, insert, update, and delete schemas. Use a different user ID to create the schemas.
| Schema name | snow |
| Schema name for SCA.SYSTEM ME | snowSYS |
| Schema name for SCA.APP ME | snowAPP |
| Schema name for Event ME | snowEvent |
| Schema name for BPC ME | snowBPC |
| User ID to create the schemas | rock |
| User ID to select, insert, update, and delete schemas | snow |
The following table contains information about how to set up the schema name and user ID privileges with DB2 as the database.
| Database tables | Database name with DB2 | Schema name | User ID to create tables | User ID to select, insert, update, and delete rows |
|---|---|---|---|---|
| Common database tables | Supply this value twice:
If you run the installer first, supply the value once because the generated scripts already contain the correct schema name and user ID values. | Modify table creation scripts with the schema name that allows reading and writing rows. | Modify the table creation script to contain the user ID. | Supply the user ID during profile creation using:
|
| Business Process Choreographer tables | Supply this value twice:
| Modify table creation scripts with the schema name that allows reading and writing rows. | Modify the table creation script to contain the user ID. | Supply the user ID during profile creation using:
|
Scenario 3 for multiple user ID or schema name privileges
In this scenario, use the same user ID to create all schemas. However, each schema has a different user ID to select, insert, update, and delete rows. The following list shows examples of privileges for Scenario 3:
| Schema name | waterCom |
| Schema name for common tables | waterCom |
| Schema name for SCA.SYSTEM ME | waterSYSME |
| Schema name for SCA.APP ME | waterAPPME |
| Schema name for Event ME | waterEventME |
| Schema name for BPC ME | waterBPCME |
| Schema name for BPC and HTM tables | waterBPC |
| Schema name for ESBMessaging tables | waterESB |
| User ID to create schemas | milk |
User ID to select, insert, update, and delete schemas
| Schema name | User ID |
|---|---|
| waterCom | waterCom |
| waterSYSME | waterSYSME |
| waterAPPME | waterAPPME |
| waterEventME | waterEventME |
| waterBPCME | waterBPCME |
| waterBPC | waterBPC |
| waterESB | waterESB |
Multiple user ID or schema
| Database tables | Database name with DB2 | Schema name | User ID to create tables | User ID to select, insert, update, and delete rows |
|---|---|---|---|---|
| Common database tables | Supply this value in...
| Schema name is the same as the user ID used to select, insert, update, and delete rows. | This value is the same as the user ID used to select, insert, update, and delete rows. | Supply the user ID during profile creation using:
|
| Business Process Choreographer tables | Supply this value twice:
| The table creation scripts need to be modified with a schema name used to select, insert, update, and delete rows. | This value is the same as the user ID used to select, insert, update, and delete rows. | Supply this value twice:
|
| Messaging tables | Supply this value with the definition of each messaging engine. | The table creation scripts must include the schema name used to select, insert, update, and delete rows. | This value is the same as the user ID used to select, insert, update, and delete rows. | Supply this value during the creation of the messaging engine. Select the Create Table option during the messaging engine configuration. |
Plan to configure Business Process Choreographer
In BPM Advanced, Business Process Choreographer is automatically configured when you create the deployment environment.
- Decide which configuration tool to use to create the deployment environment:
- For a default Business Process Choreographer configuration that uses the common database or a separate database, use either the administrative console deployment environment wizard or BPMConfig.
- For a fully customized Business Process Choreographer configuration, edit requirements into a configuration properties file, and then run BPMConfig.
- For a default Business Process Choreographer configuration that uses the common database or a separate database, use either the administrative console deployment environment wizard or BPMConfig.
- For deployment environment wizard, select a deployment environment pattern...
- Application, Remote Messaging, Remote Support
- Single Cluster
Steps...
- If you use BPMConfig to create the deployment environment, use a properties file...
- product_configuration-topology-environment_type-database_type
- To only run BPEL processes, you can use one of the AdvancedOnly product configuration properties files in directory...
- INSTALL_ROOT/BPM/samples/config/advancedonly
These configurations do not include support for BPMN processes, which results in a smaller footprint.
- To support both BPMN processes and BPEL processes, use one of the Advanced product configuration properties files in directory...
- INSTALL_ROOT/BPM/samples/config/advanced
In this case, decide whether you are creating a Process Server (PS) or Process Center (PC) configuration.
- Depending on your need for production performance, decide between a single cluster (SingleCluster) or three cluster (ThreeClusters) topology environment.
- Identify which database system to use. For example, SQLServer, SQLServer-WinAuth, Oracle, DB2, or DB2zOS.
- Your choices identify which properties file to copy and, if necessary, customize. For example...
- INSTALL_ROOT/BPM/samples/config/advancedonly/AdvancedOnly-ThreeClusters-DB2.properties
...or...
- INSTALL_ROOT/BPM/samples/config/advanced/Advanced-PS-SingleCluster-Oracle.properties
- All the Advanced and AdvancedOnly configuration files include a Business Process Choreographer configuration that you can customize as necessary.
To have Human Task Manager to send email notifications of escalation events, identify the host name or IP address where the SMTP email server is located. If the email service requires authentication, know the user ID and password to use to connect to the service.
To use the Business Process Choreographer Explorer, Process Portal, or a client that uses the REST API or the JAX web services API, decide on the context roots for the REST API and the JAX web services API.
The defaults for the Business Flow Manager are...
-
/rest/bpm/bfm
/BFMJAXWSAPI
The defaults for the Human Task Manager are...
-
/rest/bpm/htm
/HTMJAXWSAPI
When configured on a single cluster, or on multiple clusters mapped to different web servers, you can use the default values.
When configured in a network deployment environment on multiple deployment targets mapped to the same web server, do not use the default values. The context root for each Business Process Choreographer configuration must be unique for each combination of host name and port. Set these values manually using the administrative console after configuring an environment that includes Business Process Choreographer.
Optional: Create use people assignment
Plan for the people directory provider
- To use human tasks, decide which people directory providers use:
- Virtual member manager (VMM) people directory provider
- Pre-configured federated repositories. To use a different user repository with federated repositories, reconfigure federated repositories. The VMM people directory provider supports all Business Process Choreographer people assignment features including substitution. It relies on the features provided by federated repositories, such as support for different repository types, such as LDAP, database, file based, and property extension repository.
To use the VMM people directory provider configure federated repositories for WebSphere Application Server security. You can associate federated repositories with one or more user repositories, based on a file, LDAP, or a database.
- LDAP people directory provider
- Perform the planning in step 2.
- System people directory provider
- Requires no configuration. Do not use for a production system.
- User registry people directory provider
- Requires no configuration. Depending on the WebSphere security realm definition, the user registry can use one of the following repositories:
- Federated repository - which can use the following repositories:
- File registry
- One or more LDAPs
- One or more databases
- Stand-alone LDAP
- Stand-alone custom
- Local operating system
- Federated repository - which can use the following repositories:
- To use the LDAP, plan the following items.
- You might need to customize your own version of the LDAPTransformation.xsl file.
- Plan the following LDAP custom properties:
LDAP plug-in property Required or optional Description AuthenticationAlias Optional The authentication alias used to connect to LDAP, for example, mycomputer/My LDAP Alias. Define this alias in the administrative console by clicking... -
Security | Secure administration, applications, and infrastructure | Java Authentication and Authorization Service | J2C Authentication Data
If this alias is not set or if AuthenticationType is not set to simple then an anonymous logon to the LDAP server is used.
AuthenticationType Optional If set to simple, for simple authentication, then the AuthenticationAlias parameter is required. If not set, anonymous authentication is used. BaseDN Required The base distinguished name (DN) for all LDAP search operations, for example... -
o=mycompany, c=us
To specify the directory root, specify an empty string using two single quotation marks, ''.
CasesentivenessForObjectclasses Optional Determines whether the names of LDAP object classes are case-sensitive. ContextFactory Required Sets the JNDI context factory, for example... -
com.sun.jndi.ldap.LdapCtxFactory
ProviderURL Required Web address pointing to the LDAP JNDI directory server and port. The format must be in normal JNDI syntax, for example... -
ldap://localhost:389
For SSL connections, use the LDAP's URL. For a high availability configuration, with two or more LDAP servers that maintain mirrored data, plan to specify a URL for each LDAP server and use the space character to separate them.
SearchScope Required The default search scope for all search operations. Determines how deep to search beneath the baseDN property. Specify one of the following values: objectScope, onelevelScope, or subtreeScope additionalParameterName1-5 and additionalParameterValue1-5 Optional Use these name-value pairs to set up to five arbitrary JNDI properties for the connection to the LDAP server.
- To use the virtual member manager, plan the following items.
You might need to customize your own version of the VMMTransformation.xsl file.
- To use people substitution, consider the following guidelines:
- You must use the VMM people directory provider. The LDAP, system, and user registry people directory providers do not support people substitution.
- To use people substitution in a production environment, plan to use the VMM Property Extension Repository to store the substitution information. The Property Extension Repository and, implicitly, the selected database must be unique and accessible from within the whole cell. As the BPEDB database is not necessarily unique within a cell, BPEDB cannot be used. You can use the common database, WPSRCDB, to host the Property Extension Repository, however, for a production environment, it is recommended to use a database that is independent of other Process Server databases.
- To use people substitution in a single-server test environment, you can store people substitution information in the internal file registry that is configured for federated repositories.
- If using people assignment for human tasks, and use a LDAP
people directory provider that uses simple authentication, plan a Java Authentication and Authorization Service (JAAS) alias and an associated user ID that will be used to connect to the LDAP server.
If the LDAP server uses anonymous authentication this alias and user ID are not required.
Planning the alias and user ID for the LDAP server
User ID or role When the user ID is used What the alias and user ID are used for Which rights the user ID must have LDAP plug-in property: AuthenticationAlias Run time The alias is used to retrieve the user ID used to connect to the LDAP server. You specify this alias ID when customizing the properties for the LDAP plug-in, for example mycomputer/My LDAP Alias. The JAAS alias must be associated with the LDAP user ID. LDAP user ID Run time This user ID is used to connect to the LDAP server. If the LDAP server uses simple authentication, this user ID must be able to connect to the LDAP server. This user ID is either a short name or a distinguished name (DN). If the LDAP server requires a DN you cannot use the short name.
Business Process Choreographer overview
Business Process Choreographer is an enterprise workflow engine that supports both BPEL processes and human tasks in a WebSphere Application Server environment. These constructs can be used to orchestrate services as well as integrate activities that involve people in business processes. Business Process Choreographer manages the lifecycle of BPEL processes and human tasks, navigates through the associated model, and invokes the appropriate services.
Business Process Choreographer provides the following facilities:
- Support for BPEL processes and human tasks. Allows you to model your business process using the Web Services Business Process Execution Language (WS-BPEL, abbreviated to BPEL). With human tasks, you can use the Task Execution Language (TEL) to model activities that involve people. Both BPEL processes and human tasks are exposed as services in a service-oriented architecture (SOA) or Service Component Architecture (SCA); they also support simple data objects and business objects.
- Application programming interfaces for developing customized applications for interacting with BPEL processes and human tasks.
- Human workflow widgets as part of Business Space. These widgets allow you to manage work, create tasks for other people, and initiate services and processes.
- Business Process Choreographer Explorer. This web application allows you to administer BPEL processes and human tasks.
- Business Process Archive Manager. When configured, this provides a separate database, to which completed process instances and human tasks can be moved by running an administrative script. This can help to maintain the performance of your Business Process Choreographer database. An API is also available so that you can create your own client that can work with archived instances.
The Business Process Archive Explorer is a web application that allows users to browse or delete instances that have been moved to the archive database.
- By default, new Business Process Choreographer configurations benefit from the performance improvements resulting from using shared work items.
- To monitor and report on BPEL processes, use IBM Business Monitor.
Shared work items
Use shared work items is an optimization to improve the performance of database queries and reduce the database input/output. If you create a new Business Process Choreographer configuration, it automatically uses shared work items. If you migrated your Business Process Choreographer configuration using shared work items is optional.
What are shared work items?
Work items are created in the Business Process Choreographer database for each combination of human task instance and all people who are permitted to perform actions on that instance. If the number of human task instances and the number of users increases significantly, the number of work items in the database can grow so large the database performance is affected.
The idea behind shared work items is an optimized implementation of work items, such that redundant information about work items is not stored in the database. This can improve the performance of many BPEL process and human task queries. Whether shared work items are being used, or not, is transparent to the users of Business Process Choreographer APIs.
How to decide whether to add support for shared work items
It is only if you migrate your Business Process Choreographer configuration from Version 7.0.0.2 or earlier, the support for shared work items is not activated. Although activating is optional, certain factors indicate that using shared work items will improve performance.
- If you only have hundreds or a few thousands of human task instances in your system, there is probably little or no performance advantage in migrating to using shared work items.
- If you have hundreds of thousands of human task instances in your system, and your task list and process list queries are taking too long, migrating to using shared work items should improve the performance.
- Use shared work items can improve the performance of the following queries:
- query()
- queryAll()
- queryEntities()
- queryEntityCount()
- queryRows()
- queryRowCount()
Restrictions
Some queries can only be resolved using the non-shared work items. This means that enabling support for shared work items will not improve the performance of the following types of queries:
- Queries that run against the WORK_ITEM view exclusively.
- Queries that reference one or more of the following columns in the WORK_ITEM view:
- ASSOC_OBJECT_TYPE
- ASSOC_OID
- OBJECT_ID
- CREATION_TIME
- OBJECT_TYPE
- Queries referencing a custom table that is directly joined with the WORK_ITEM view.
- Queries that were created as materialized views.
- Queries that use authorization with inherited work items.
BPEL process archive overview
The Business Process Archive Manager is an optional component that allows you to use a script to move completed BPEL process instances and human tasks from the Business Process Choreographer database to an archive database. By regularly performing archiving, you can prevent the runtime database from filling up with old objects, which over time, can degrade the database performance. You can use a Business Process Archive Explorer or the Business Process Archive Manager API to access processes and tasks that were moved to the archive database. Because it is not possible to move data from an archive database back to a runtime database, using this archiving facility does not provide any backup protection.
Architecture
The BPEL process archive facility consists of the following elements:
- Business Process Archive Manager
- Business Process Archive Explorer
- Business Process Archive database
- The archive.py script
- Business Process Archive Manager EJB API
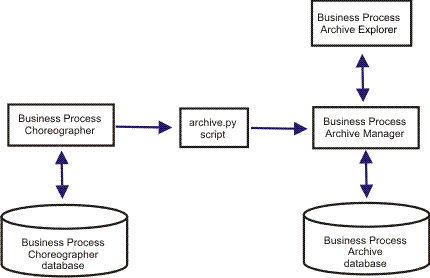
- Business Process Archive Manager
-
To create a Business Process Archive Manager, add entries to the properties file before creating the deployment environment.
The following conditions apply:
- You can create a Business Process Archive Manager only on the support cluster in a three-cluster setup.
- A Business Process Choreographer configuration can only use a Business Process Archive Manager configurations that is in the same cell.
- A Business Process Archive Manager configuration can be used to archive data from only one Business Process Choreographer configuration.
- Each Business Process Archive Manager configuration must have its own Business Process Archive database.
- Business Process Archive database
- Each Business Process Archive Manager requires its own database. The database must be of the same type and structure as is used for the Business Process Choreographer database. The default name for the archive database is BPARCDB.
- The archive.py administrative script
- A WebSphere system administrator can run this script to archive data from the runtime database of one Business Process Choreographer configuration to the archive database of a Business Process Archive Manager configuration. You can specify various parameters to control which instances are archived, how many to archive in total, and how many to archive in each database transaction. The source and destination are specified by their deployment servers or clusters.
Restriction: The following restrictions apply:
- You cannot transfer objects from an archive database back to a Business Process Choreographer database, nor to another archive.
- The first time that you archive instances to a new archive database, the identity of the Business Process Choreographer configuration is written to the database, and in future, only instances from that configuration can be archived to that archive database.
- When instances are successfully moved to the archive, they are deleted from the Business Process Choreographer database, which generates a deletion event for the common event infrastructure (CEI) and the audit log. But it is not possible to identify the deletion event was caused by an archiving action rather than by some other delete action, for example, cleanup service, user initiated delete action, delete script, or automatic deletion after successful completion.
- You cannot archive to different archives at the same time. Parallel invocations of the archive.py script are serialized.
- You cannot archive a process instance that has the same process name as any other process instance in the archiving database.
- You cannot archive a process instance that has the same values for its correlation set as another process instance in the archiving database.
- If you archive instances of a process template, then undeploy and redeploy the identical process template with the valid from date unchanged, you cannot archive any new instances of that process template to the same archive database. This is not an issue for normal process template versioning, where a different valid from date is used.
However, even if one of the restriction prevents you from archiving certain process instances to one archive database, you can archive those process instances to a different archive database, for which the restriction conditions are not true.
- Business Process Archive Manager EJB API support
- Only a subset of the actions that are available using the Business Flow Manager and Human Task Manager EJB APIs can also be used against a Business Process Archive Manager configuration to read and delete process instances and human tasks that are in the archive database.
The other APIs are not supported by the Business Process Archive Manager.
A new method, OperationMode getOperationMode() is provided, which indicates whether the client is connected to a Business Process Choreographer configuration or a Business Process Archive Manager configuration. This can be used to write custom clients that can connect to and operate appropriately on runtime configurations and archive configurations.

For more information about the Business Process Archive Manager API, see the Javadoc for the packages com.ibm.bpe.api and com.ibm.task.api.
- Business Process Archive Explorer
- The Business Process Archive Explorer is similar to the Business Process Choreographer Explorer except that it connects to an archive database associated with a Business Process Archive Manager configuration. The Business Process Archive Explorer is configured when you configure the Business Process Archive Manager.
Depending on your authorization, you can use the Business Process Archive Explorer to browse instances and possibly delete instances too. You cannot update instances or create new instances.
- Authorization
- The actions that you can perform with the Business Process Archive Manager EJB API or the Business Process Archive Explorer depends on the following Java™ Platform, Enterprise Edition (Java EE)
roles:
- Users who are in the Business Process Archive Manager system monitor role can read and view all process instances and all task instances in the archive database.
- Users who are in the Business Process Archive Manager system administrator role can also delete any top-level process instances and top-level
task instances in the archive database.
- Users who are not in the system monitor or system administrator roles can see only the instances they created or started themselves, but they cannot view any details about the instances.
- No one (not even users in the system administrator roles) can modify any of the data that is associated with any instances in the archive database.
- Instance-based authorization information, such as the potential owner or reader information, is not archived. Therefore, this data is not available in the archive. The only exception to this rule is the information about the starter and creator of processes and tasks.
- Users must be in the WebClientUser role to use the Business Process Archive Explorer.
- Users who are in the Business Process Archive Manager system monitor role can read and view all process instances and all task instances in the archive database.
Which data is archived
Only top-level process instances and top-level stand-alone human task instances that have reached one of the end states (Finished, Terminated, Failed, or Expired) can be moved to the archive database. When a top-level instance is archived, certain data is also moved with it to the archive, and other data is deleted.
- For completed top-level process instances, including business state machine instances:
-
- Instance data such as activities, variables, inline human tasks, input messages, and output messages are moved.
- Child processes and related data are moved recursively.
- If any related metadata such as process templates and task templates are not already in the archive database, a copy of them is created.
- Query tables and stored queries are not moved nor copied to the archive database.
- Work items that are associated with an archived instance are deleted without being archived.
- For completed top-level stand-alone human tasks:
-
- Instance data such as input messages and output messages are moved.
- Escalation instances are moved.
- Child tasks, including follow-on tasks, are moved.
- If related metadata such as task templates are not already in the archive database, a copy of them is created.
- Work items that are associated with an archived instance are deleted without being archived.
- Metadata
- Extra metadata, such as process and task template information, is copied to the archive when necessary to allow the archived data to be interpreted and displayed correctly. The metadata in the archive database is deleted when it is no longer required, that is, when the last process instance or human task that references the metadata is deleted.
- What is not archived
- Other Business Process Choreographer data, such as configuration data, XSD and WSDL artifacts, SCA modules, applications, work baskets, business categories, business rules, messages, and audit trail data, cannot be moved to the archive.
Configure Business Process Archive Manager
The Business Process Archive Manager is an optional component that allows reduce the size of the Business Process Choreographer database, by moving completed BPEL process instances and human tasks to a separate archive database. To configure a Business Process Archive Manager, add entries to the properties file before creating the deployment environment.
You can configure the Business Process Archive Manager only on the support cluster of three cluster setup that is based on the Advanced or AdvancedOnly template properties file. When you configure the Business Process Archive Manager, a Business Process Archive Explorer is also configured.
- Open the deployment environment properties file in an editor.
For more information about possible keys and values for the BPCArchive component, see the appropriate properties file.
-

 install_root/BPM/samples/config/advanced/Advanced-PC-ThreeClusters-DB2.properties
install_root/BPM/samples/config/advanced/Advanced-PC-ThreeClusters-DB2.properties
-
 install_root\BPM\samples\config\advanced\Advanced-PC-ThreeClusters-DB2.properties
install_root\BPM\samples\config\advanced\Advanced-PC-ThreeClusters-DB2.properties
-
- Set the BPCArchive component on the support cluster. For example, if cluster 3 is the support cluster, and the next free component index is 1, add an entry that is similar to the following example:
- bpm.de.cluster.3.capability.1.component.1.name=BPCArchive
- Add the archive database to the support cluster. For example, add an entry that is similar to the following example:
- bpm.de.cluster.3.db=PerformanceDb,ArchiveDb
- Add the definition of the archive database. For example, for a DB2 database named BPARCDB, if the next free database index is 5, add entries that are similar to the following example.
- bpm.de.db.5.name=ArchiveDb
bpm.de.db.5.dbCapabilities=BPCArchive
bpm.de.db.5.databaseName=BPARCDB
bpm.de.db.5.type=DB2
bpm.de.db.5.hostname=localhost
bpm.de.db.5.portNumber=50000
bpm.de.db.5.roleMapping.1.name=DbUser
bpm.de.db.5.roleMapping.1.alias=BPM_DB_ALIAS
bpm.de.db.5.roleMapping.2.name=DbUserXAR
bpm.de.db.5.roleMapping.2.alias=BPM_DB_ALIAS
bpm.de.db.5.schema=db2adminBecause the purpose of the Business Process Archive Manager is to reduce the size of the runtime database, make sure that BPARCDB is a separate database from the database that Business Process Choreographer uses.
Business Process Choreographer Explorer overview
Business Process Choreographer Explorer is a web application that implements a generic web user interface for interacting with BPEL processes and human tasks. It is automatically configured with Business Process Choreographer.
When you start Business Process Choreographer Explorer, the objects that you see in the user interface and the actions that you can take depend on the user group that you belong to and the authorization granted to that group. For example, if you are a business process administrator, you are responsible for the smooth operation of deployed BPEL processes. You can view information about process and task templates, process instances, task instances, and their associated objects. You can also act on these objects; for example, you can start new process instances, create and start tasks, repair and restart failed activities, manage work items, and delete completed process instances and task instances. However, if you are a user, you can view and act on only those tasks that have been assigned to you.