Set LDAP user registries
Overview
To access an LDAP user registry requires...
- User name (ID) and password
- Server host and port
- Base distinguished name (DN)
- Bind DN and bind password
We can choose any user in the registry that is searchable. Use any user ID that has the admin role to log in. The user is referred to as a security server ID, server ID, or server user ID. A server ID user has special privileges when calling some protected internal methods.
In some LDAP servers, admin users cannot be searched and thus cannot be used.
When security is enabled in WAS ND, the primary admin user name and password are authenticated with the registry during WAS startup. If authentication fails, the server does not start. Choose an ID and password that do not expire or change often.
If the server user ID or password need to change in the registry, make the changes when all WAS servers are up and running.
Review the article on Standalone LDAP registries before beginning.
Procedure
- In the admin console, click...
- Security | Global security
- Under User account repository, click the Available realm definitions drop-down list, and select...
- Standalone LDAP registry | Configure

- Enter a valid user name in the Primary administrativeistrative user name field. For example...
-
cn=wasadminqa,OU=Service
We can either enter the complete distinguished name (DN) of the user or the short name of the user, as defined by the user filter in the Advanced LDAP settings panel. This ID is the security server ID, which is only used for WAS security and is not associated with the system process that runs the server. The server calls the local operating system registry to authenticate and obtain privilege information about users by calling the native APIs in that particular registry.
- To enable the appserver to generate the server identity used for internal process communication, select...
-
Automatically generated server identity
To change this server identity, go to...
- Security | Global security | Authentication mechanisms and expiration
...and change the value of the Internal server ID field.
Alternatively, specify the user ID used to run the application server for security purposes in the field...
-
Server user ID or administrative user on a V6.0.x node
- Select the type of LDAP server to use from the Type list.
The type of LDAP server determines the default filters that are used by WAS. These default filters change the Type field to Custom, which indicates that custom filters are used. This action occurs after you click OK or Apply in the Advanced LDAP settings panel. Choose the Custom type from the list and modify the user and group filters to use other LDAP servers, if required.
IBM Tivoli Directory Server users can choose IBM Tivoli Directory Server as the directory type. Use the IBM Tivoli Directory Server directory type for better performance.
See the list of supported LDAP servers.
IBM SecureWay Directory Server has been renamed to IBM Tivoli Directory Server in WAS version 6.1.
- Enter the fully qualified host name of the LDAP server in the Host field.
We can enter either the IP address or DNS name.
- Enter the LDAP server port number in the Port field.
The host name and the port number represent the realm for this LDAP server in the WAS cell. So, if servers in different cells are communicating with each other using LTPA tokens, these realms must match exactly in all the cells.
The default value is 389. If multiple WASs are installed and configured to run in the same single sign-on domain, or if the WAS interoperates with a previous version of the WAS, then it is important that the port number match all configurations. For example, if the LDAP port is explicitly specified as 389 in a version 5.x configuration, and a WAS at version 6.0.x is going to interoperate with the version 5.x server, then verify that port 389 is specified explicitly for the version 6.0.x server.
- Enter the base distinguished name (DN) in the Base distinguished name field.
The base DN indicates the starting point for searches in the LDAP directory server.
For example, for a user with a DN of...
-
cn=John Doe, ou=Rochester, o=IBM, c=US
...specify the base DN as any of the following...
- ou=Rochester, o=IBM, c=us
- o=IBM c=us
- c=us
For authorization purposes, this field is case sensitive by default. Match the case in the directory server. If a token is received (for example, from another cell or Lotus Domino) the base DN in the server must match exactly the base DN from the other cell or Domino. If case sensitivity is not a consideration for authorization, enable the Ignore case for authorization option.
In WAS, the distinguished name is normalized according to the LDAP specification. Normalization consists of removing spaces in the base distinguished name before or after commas and equal symbols.
An example of a non-normalized base distinguished name is...
-
o = ibm, c = us or o=ibm, c=us
An example of a normalized base distinguished name is...
-
o=ibm,c=us
To interoperate between WAS V5 and later versions, enter a normalized base distinguished name in the Base Distinguished Name field. In WAS, V 5.0.1 or later, the normalization occurs automatically during runtime.
This field is required for all LDAP directories except the Lotus Domino Directory. The Base Distinguished Name field is optional for the Domino server.
- Enter the bind DN name in the Bind distinguished name field.
For example...
-
wasadminqa
The bind DN is required if anonymous binds are not possible on the LDAP server to obtain user and group information. If the LDAP server is set up to use anonymous binds, leave this field blank. If a name is not specified, the appserver binds anonymously.
- Enter the password corresponding to the bind DN in the Bind password field.
- Modify the Search time out value.
This timeout value is the maximum amount of time that the LDAP server waits to send a response to WAS client before stopping the request. The default is 120 seconds.
- To specify that the server should reuse the LDAP connection, select the option...
-
Reuse connection
Clear this option only in rare situations where a router is used to send requests to multiple LDAP servers and when the router does not support affinity. Leave this option selected for all other situations.
- Verify that the option...
-
Ignore case for authorization option is enabled
Normally, an authorization check involves checking the complete DN of a user, which is unique in the LDAP server and is case sensitive. However, when you use either the IBM Directory Server or the Sun ONE Directory Server LDAP servers, enable this option because the group information that is obtained from the LDAP servers is not consistent in case. This inconsistency affects the authorization check only. Otherwise, this field is optional and can be enabled when a case sensitive authorization check is required.
For example, we might select this option when you use certificates and the certificate contents do not match the case of the entry in the LDAP server.
We can also enable the option...
- Ignore case for authorization
...when we are using SSO between WAS and Lotus Domino. The default is enabled.
- Select the SSL enabled option to use SSL communications with the LDAP server.
If we select the SSL enabled option, we can select either the Centrally managed or the Use specific SSL alias option.
- Centrally managed
- Enables you to specify an SSL configuration for particular scope such as the cell, node, server, or cluster in one location. To use the Centrally managed option, specify the SSL configuration for the particular set of endpoints. The Manage endpoint security configurations and trust zones panel displays all of the inbound and outbound endpoints that use the SSL protocol. If we expand the Inbound or Outbound section of the panel and click the name of a node, we can specify an SSL configuration used for every endpoint on that node. For an LDAP registry, we can override the inherited SSL configuration by specifying an SSL configuration for LDAP. To specify an SSL configuration for LDAP...
- Click Security > SSL certificate and key management > Manage endpoint security configurations and trust zones.
- Expand Outbound > mycell > Nodes > mynode > Servers > myserver > LDAP.
- Use specific SSL alias
- Select the Use specific SSL alias option if we intend to select one of the SSL configurations in the menu below the option.This configuration is used only when SSL is enabled for LDAP. The default is DefaultSSLSettings. To modify or create a new SSL configuration...
- Click Security > SSL certificate and key management.
- Under Configuration settings, click Manage endpoint security configurations.
- Select an SSL configuration_name for selected scopes, such as a cell, node, server, or cluster.
- Under Related items, click SSL configurations.
- Click New.
- Click OK and either Apply or Save until you return to the Global security panel.
Results
This set of steps is required to set up the LDAP user registry. This step is required as part of enabling security in the WAS.
Next steps
- If enabling security, complete the remaining steps as specified in Enable security for the realm.
- Save, stop, and restart all WAS servers (dmgrs, nodes and Application Servers) for changes in this panel to take effect. If the server comes up without any problems the setup is correct.
Standalone LDAP registry settings
Standalone LDAP registry wizard settings
Advanced LDAP user registry settings
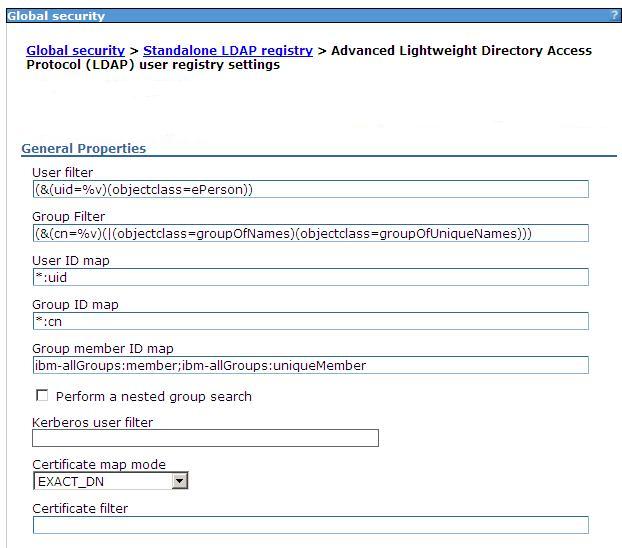
Set LDAP search filters
Use specific directory servers as the LDAP server
Locating a users group memberships in LDAP
Set multiple LDAP servers for user registry failover
Testing an LDAP server for user registry failover
Delete LDAP endpoints using wsadmin
Updating LDAP binding information
Related concepts
Local operating system registriesEnable security
Enable security for the realm
Select a registry or repository