Comparing link level security and application level security
This topic contains information about various aspects of link level security and application level security, and compares the two levels of security.
Link level and application level security are illustrated in Figure 1.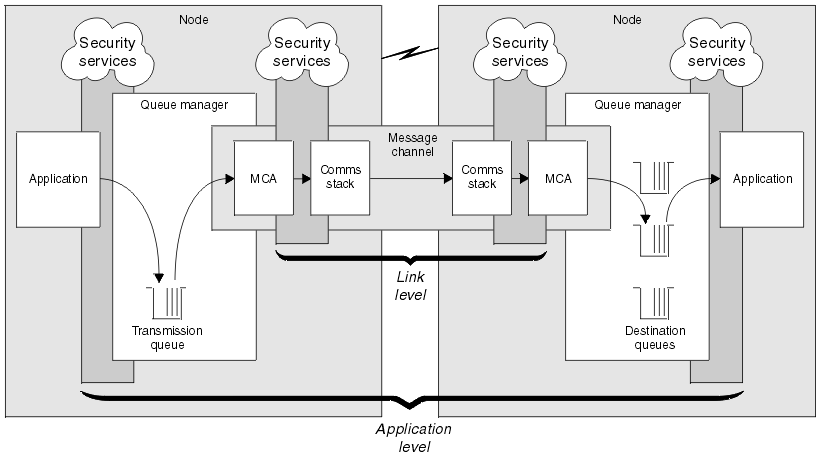
Protecting messages in queues
Link level security can protect messages while they are transferred from one queue manager to another. It is particularly important when messages are transmitted over an insecure network. It cannot, however, protect messages while they are stored in queues at either a source queue manager, a destination queue manager, or an intermediate queue manager.
z/OS data set encryption can provide some protection of messages stored on queues, but only for data at rest on a local queue manager. See the section, confidentiality for data at rest on IBM MQ for z/OS with data set encryption. for more information.
Application level security, by comparison, can protect messages while they are stored in queues and applies even when distributed queuing is not used. This is the major difference between link level security and application level security and is illustrated in Figure 1.
Queue managers not running in controlled and trusted environments
If a queue manager is running in a controlled and trusted environment, the access control mechanisms provided by IBM MQ might be considered sufficient to protect the messages stored on its queues. This is particularly true if only local queuing is involved and messages never leave the queue manager. Application level security in this case might be considered unnecessary.
Application level security might also be considered unnecessary if messages are transferred to another queue manager that is also running in a controlled and trusted environment, or are received from such a queue manager. The need for application level security becomes greater when messages are transferred to, or received from, a queue manager that is not running in a controlled and trusted environment.
Differences in cost
Application level security might cost more than link level security in terms of administration and performance.
The cost of administration is likely to be greater because there are potentially more constraints to configure and maintain. For example, you might need to ensure that a particular user sends only certain types of message and sends messages only to certain destinations. Conversely, you might need to ensure that a particular user receives only certain types of message and receives messages only from certain sources. Instead of managing the link level security services on a single message channel, you might need to be configuring and maintaining rules for every pair of users who exchange messages across that channel.
There might be an effect on performance if security services are invoked every time an application puts or gets a message.
Organizations tend to consider link level security first because it might be easier to implement. They consider application level security if they discover that link level security does not satisfy all their requirements.
Availability of components
Generally, in a distributed environment, a security service requires a component on at least two systems. For example, a message might be encrypted on one system and decrypted on another. This applies to both link level security and application level security.
In a heterogeneous environment, with different platforms in use, each with different levels of security function, the required components of a security service might not be available for every platform on which they are needed and in a form that is easy to use. This is probably more of an issue for application level security than for link level security, particularly if you intend to provide your own application level security by buying in components from various sources.
Messages in a dead letter queue
If a message is protected by application level security, there might be a problem if, for any reason, the message does not reach its destination and is put on a dead letter queue. If we cannot work out how to process the message from the information in the message descriptor and the dead letter header, you might need to inspect the contents of the application data. We cannot do this if the application data is encrypted and only the intended recipient can decrypt it.
What application level security cannot do
Application level security is not a complete solution. Even if you implement application level security, you might still require some link level security services. For example:- When a channel starts, the mutual authentication of the two MCAs might still be a requirement. This can be done only by a link level security service.
- Application level security cannot protect the transmission queue header, MQXQH, which includes the embedded message descriptor. Nor can it protect the data in IBM MQ channel protocol flows other than message data. Only link level security can provide this protection.
- If application level security services are invoked at the server end of an MQI channel, the services cannot protect the parameters of MQI calls that are sent over the channel. In particular, the application data in an MQPUT, MQPUT1, or MQGET call is unprotected. Only link level security can provide the protection in this case.
- Link level security
Link level security refers to those security services that are invoked, directly or indirectly, by an MCA, the communications subsystem, or a combination of the two working together. - Application level security
Application level security refers to those security services that are invoked at the interface between an application and a queue manager to which it is connected.
Parent topic: Plan confidentiality