Retrieving CRLs by using an LDAP server
We can configure MQIPT to use an LDAP server to retrieve certificate revocation lists (CRLs).
Before starting
- Before you start to use this scenario, make sure that we have completed the prerequisite tasks listed in Getting started with IBM MQ Internet Pass-Thru.
- Ensure that MQIPT 2 has a personal certificate, issued by the trusted Certificate Authority (CA), stored in a key ring file called myCert.pfx.
- Ensure that MQIPT 1 has a copy of the trusted CA certificate that will be used to authenticate the certificate sent by MQIPT 2. This certificate is stored in a key ring file called caCerts.pfx.
- The passwords to access the key rings have been encrypted using the mqiptPW command.
In this scenario, we can connect the IBM MQ client to a queue manager (QM) and place an IBM MQ message on the target queue. Running an MQIPT trace on MQIPT 1 will show the LDAP server being used.
To demonstrate how CRLs work, make sure that the personal certificate used by MQIPT 2 is revoked by the trusted CA. Then the IBM MQ client is not allowed to connect to the QM, as the connection from MQIPT 1 to MQIPT 2 is rejected.
It is not the intention of this scenario to explain how to install and set up an LDAP server nor how to create a key ring file containing personal or trusted certificates. It assumes that the LDAP server is available from a known and trusted CA. A backup LDAP server is not used, but could be implemented by adding the appropriate Route properties.
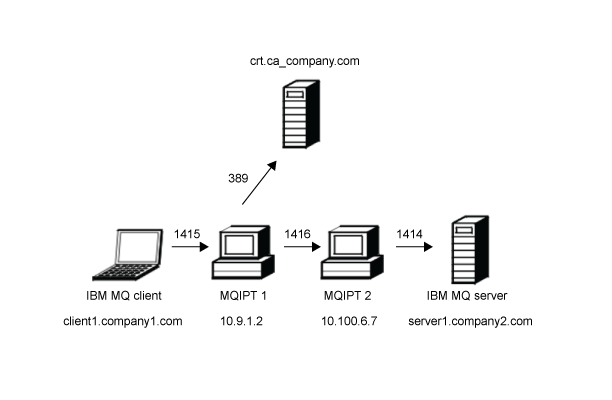
This diagram shows the connection from the IBM MQ client (client1.company1.com on port 1415) through two instances of MQIPT to the IBM MQ server (server1.company2.com on port 1414). The first MQIPT has a connection to an LDAP server (crl.ca_company.com on port 389).
Procedure
To retrieve CRLs by using an LDAP server, complete the following steps:
- On the MQIPT 1 system:
- Edit mqipt.conf and add the following route
definition:
[route] ListenerPort=1415 Destination=10.100.6.7 DestinationPort=1416 SSLClient=true SSLClientCAKeyRing=C:\mqiptHome\ssl\caCerts.pfx SSLClientCAKeyRingPW=encrypted_key_ring_password LDAP=true LDAPServer1=crl.ca_company.com LDAPServer1Timeout=4
where encrypted_key_ring_password is the password for the caCerts.pfx key ring, encrypted using the mqiptPW command. - Open a command prompt and start MQIPT:
C:\mqipt\bin\mqipt C:\mqiptHome -n ipt1
where C:\mqiptHome indicates the location of the MQIPT configuration file, mqipt.conf, and ipt1 is the name to be given to the instance of MQIPT. The following messages indicate that MQIPT has started successfully:5724-H72 (C) Copyright IBM Corp. 2000, 2020 All Rights Reserved MQCPI001 IBM MQ Internet Pass-Thru V9.2.0.0 starting MQCPI004 Reading configuration information from mqipt.conf MQCPI152 MQIPT name is ipt1 MQCPI021 Password checking has been enabled on the command port MQCPI011 The path C:\mqiptHome\logs will be used to store the log files MQCPI006 Route 1415 has started and will forward messages to : MQCPI034 ....10.100.6.7(1416) MQCPI035 ....using MQ protocol MQCPI036 ....SSL Client side enabled with properties : MQCPI031 ......CipherSuites <NULL> MQCPI032 ......key ring file <NULL> MQCPI047 ......CA key ring file C:\mqiptHome\ssl\caCerts.pfx MQCPI071 ......site certificate uses UID=*,CN=*,T=*,OU=*,DC=*,O=*, STREET=*,L=*,ST=*,PC=*,C=*,DNQ=* MQCPI038 ......peer certificate uses UID=*,CN=*,T=*,OU=*,DC=*,O=*, STREET=*,L=*,ST=*,PC=*,C=*,DNQ=* MQCPI075 ....LDAP main server at crl.ca_company.com(389) MQCPI086 ......timeout of 4 second(s) MQCPI084 ....CRL cache expiry timeout is 1 hour(s) MQCPI085 ....CRLs will be saved in the key-ring file(s) MQCPI078 Route 1415 ready for connection requests
- Edit mqipt.conf and add the following route
definition:
- On the MQIPT 2 system:
- Edit mqipt.conf and add the following route
definition:
[route] ListenerPort=1416 Destination=server1.company2.com DestinationPort=1414 SSLServer=true SSLServerKeyRing=C:\mqipt\ssl\myCert.pfx SSLServerKeyRingPW=encrypted_key_ring_password
where encrypted_key_ring_password is the password for the myCert.pfx key ring, encrypted using the mqiptPW command. - Open a command prompt and start MQIPT:
C: cd \mqipt\bin mqipt .. -n ipt2
where .. indicates that the MQIPT configuration file, mqipt.conf, is in the parent directory, and ipt2 is the name to be given to the instance of MQIPT. The following message indicates successful completion:5724-H72 (C) Copyright IBM Corp. 2000, 2020 All Rights Reserved MQCPI001 IBM MQ Internet Pass-Thru V9.2.0.0 starting MQCPI004 Reading configuration information from mqipt.conf MQCPI152 MQIPT name is ipt2 MQCPI021 Password checking has been enabled on the command port MQCPI011 The path C:\mqipt\logs will be used to store the log files MQCPI006 Route 1416 is starting and will forward messages to : MQCPI034 ....server1.company2.com(1414) MQCPI035 ....using MQ protocol MQCPI037 ....SSL Server side enabled with properties : MQCPI031 ......CipherSuites <NULL> MQCPI032 ......key ring file C:\mqipt\ssl\myCert.pfx MQCPI047 ......CA key ring file <NULL> MQCPI071 ......site certificate uses UID=*,CN=*,T=*,OU=*,DC=*,O=*, STREET=*,L=*,ST=*,PC=*,C=*,DNQ=* MQCPI038 ......peer certificate uses UID=*,CN=*,T=*,OU=*,DC=*,O=*, STREET=*,L=*,ST=*,PC=*,C=*,DNQ=* MQCPI033 ......client authentication set to false MQCPI078 Route 1416 ready for connection requests
- Edit mqipt.conf and add the following route
definition:
- At a command prompt on the IBM MQ client
system, enter the following commands:
- Set the MQSERVER environment variable:
SET MQSERVER=MQIPT.CONN.CHANNEL/tcp/10.9.1.2(1415)
- Put a message:
amqsputc MQIPT.LOCAL.QUEUE MQIPT.QM1 Hello world
Press Enter twice after typing the message string. - Get the message:
amqsgetc MQIPT.LOCAL.QUEUE MQIPT.QM1
The message, "Hello world" is returned.
- Set the MQSERVER environment variable:
Parent topic: Getting started with IBM MQ Internet Pass-Thru