Configure WebSEAL in a highly available environment
For environments with multiple Security Verify Access with Advanced Access Control servers, we can configure WebSEAL for failover and high availability. We can configure the WebSEAL junction and Runtime Security Services External Authorization Service (RTSS EAS) to take advantage of high availability.
The image below depicts an environment where WebSEAL is configured to use two ISAM servers, AAC01 and AAC02, where AAC01 and AAC02 are appliances with Advanced Access Control activated. For high availability, we can configure a stateful junction to each available appliance. We can also include each server in the RTSS EAS configuration.
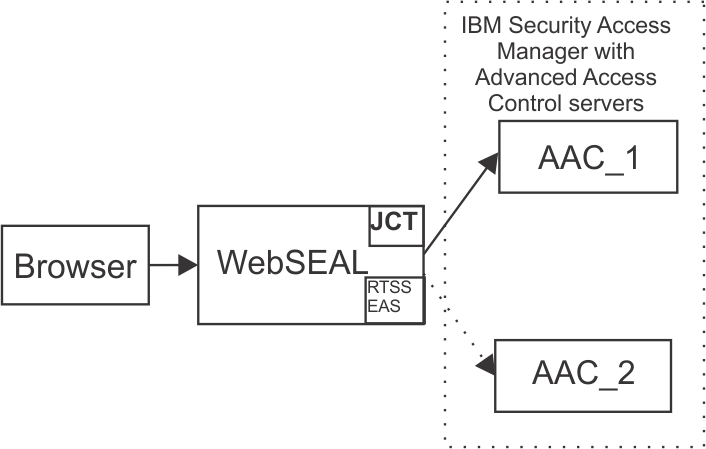
Advanced Access Control provides the isamcfg tool which configures each WebSEAL instance. This tool sets up a single junction server and configures the RTSS EAS to point to a single appliance. If we have more than one appliance with Advanced Access Control activated, we need to manually configure the additional servers.
- For each Advanced Access Control
appliance, include a server entry in the [rtss-cluster:<cluster>] stanza in the WebSEAL
configuration file (for example, webseald-default.conf).
-
[rtss-cluster:cluster1]
server = 9,https://192.0.2.0:443/rtss/authz/services/AuthzService
server = 9,https://192.0.2.5:443/rtss/authz/services/AuthzService- The first parameter in each entry is the priority of the server in the cluster. Use a priority of 9 for all servers to evenly distributes the load and switches between the available appliances.
- The second parameter is a well-formed Uniform Resource Locator (URL) for the runtime security services on the appliance. Use the IP address of the application interface on the Advanced Access Control-activated appliance.
- Use the pdadmin utility to add extra
servers to the junction.
- pdadmin sec_master> server task default-webseald-test.example.com add -h 192.0.2.0 -p 443 /mga
pdadmin sec_master> server task default-webseald-test.example.com add -h 192.0.2.5 -p 443 /mga- We must replace all example values in these commands with values that are appropriate to the environment.
- The first parameter in this server task command is the fully qualified name of the WebSEAL
server. For example, default-webseald-test.example.com.
- The -h option specifies the appliance to add to the junction. Use
the IP address of the application interface on the target appliance.
- The isamcfg tool creates an SSL junction by
default. Therefore, when we are adding servers to this junction,
use the SSL port number 443.
- By default, the isamcfg tool creates a junction called /mga. This default value is used in the example commands.
- We must replace all example values in these commands with values that are appropriate to the environment.
- For secure communication between WebSEAL and the appliance, use trusted certificates.
WebSEAL must trust the certificates presented by the appliance. To establish this trust,
we can use a common certificate authority (CA) that is trusted in the environment or we can
configure WebSEAL to trust each individual certificate.
Similarly, for client certificate authentication, the Advanced Access Control appliance must trust the certificates presented by WebSEAL.
- To configure failover between junctioned servers, set the use-new-stateful-on-error stanza entry to yes for the stateful junction to the appliance. That is, update the use-new-stateful-on-error entry in the [junction:/mga] stanza in the WebSEAL configuration file. Where /mga is the name of the junction. The isamcfg tool creates a junction called /mga by default, but this name is configurable.
If a stateful junction becomes unavailable when this value is set to yes, WebSEAL fails over to a different server. For example, if the stateful junction to AAC01 becomes unavailable, WebSEAL fails over to AAC02.