Functional overview
Context-based access includes an external authorization service (EAS), runtime authorization service, and attribute collection service.
- IBM Web Gateway Appliance
- IBM Security Verify Access
- Tivoli Verify Access for e-business
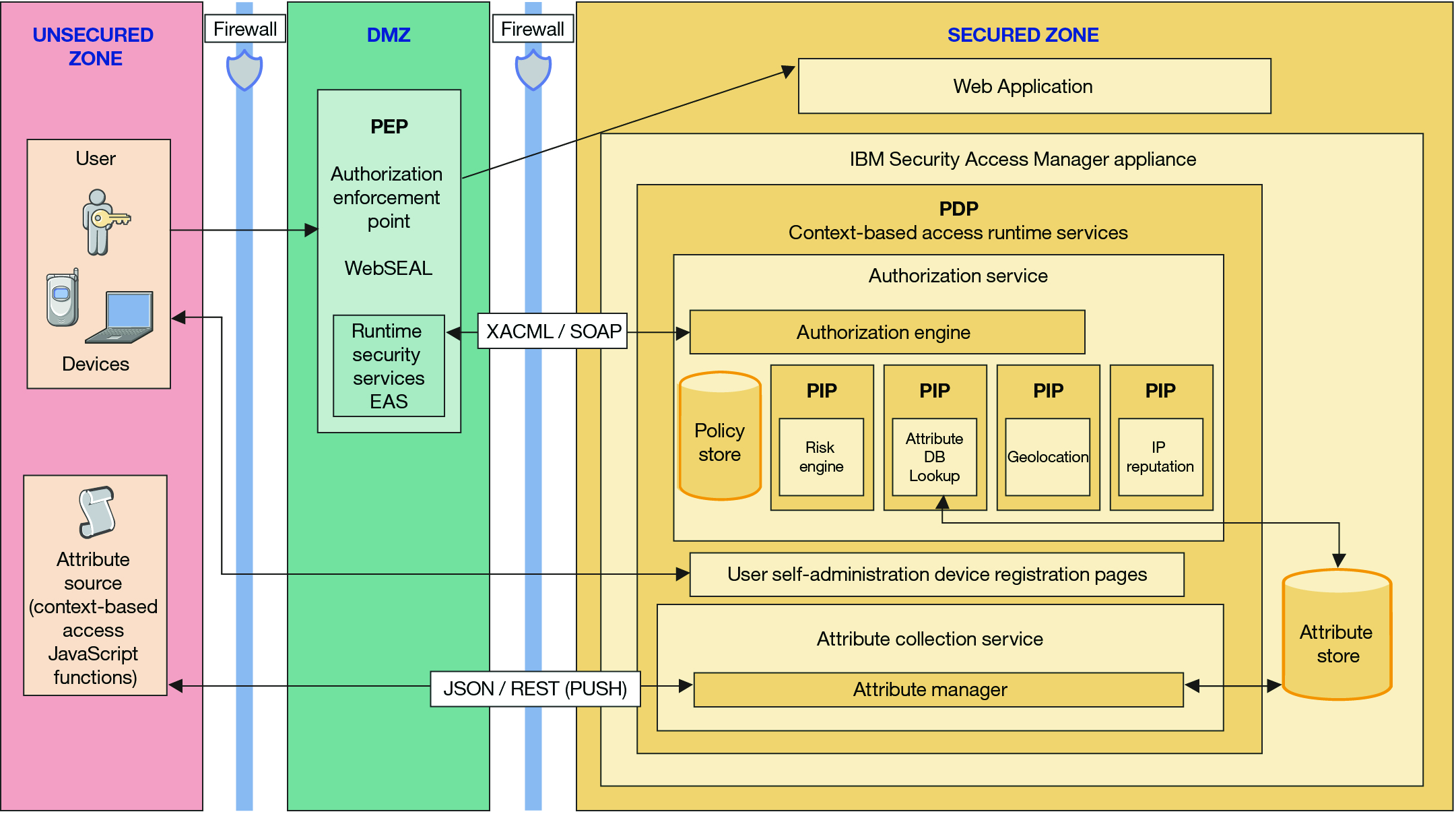
- Context-based access runtime services
- Context-based access provides the following runtime services:
- Authorization service
- The context-based access authorization service is a component of the runtime environment. The runtime authorization service stores the policy, calculates the risk score, and makes the access decision. The authorization service exposes an XACML over SOAP web service that third-party enforcement points can call to get authorization decisions.
- Attribute collection service
- The attribute collection service is a Representational State Transfer (REST) service that collects web browser and location attributes from the user. The attribute collection service is a push service. We can configure the context-based access runtime service to use the collected attributes as the policy attributes for calculating risk. We can also use the Java ADK to plug in the custom implementation for a pull service that retrieves attributes from the user.
- Risk-scoring engine
- The risk-scoring engine calculates the risk or confidence level, providing a single integer representing the risk score for the current transaction in the form of a percentage. The risk score is calculated based on the weights assigned to one or more of the following policy attributes that are part of the active risk profile:
- Device identification or fingerprint, such as details of hardware, IP address, location information, IP address reputation, operating system, web browser type, web browser version, web browser plug-ins, and screen resolution.
- Behavioral patterns, such as frequency of login, time of access, frequency of access, and type of transactions.
- Custom attributes configured through a pluggable interface. The context-based access authorization service is extensible and can also include external sources for attributes.
The risk engine returns the final risk score as a policy attribute, which is the basis of the final authorization decision.
- Policy enforcement point (PEP)
- WebSEAL is the policy enforcement point for context-based access. Context-based access integrates with the existing WebSEAL authentication mechanisms, such as cross domain authentication service (CDAS) and external authentication interface (EAI).
- External authorization service
- The runtime security services EAS plug-in for WebSEAL enforces the policy decision. The EAS takes the request data and sends an authorization decision request to the context-based access authorization service. The authorization service maps the authorization decision response to the appropriate WebSEAL action, such as permit, deny, or step-up authentication. We can manage the EAS with entries in the webseald.conf file with the WebSEAL stanza syntax. The isamcfg tool automates the configuration of the EAS for the predefined scenarios provided with the product.
- Policy information points (PIPs)
- Policy information points are components of the context-based access authorization service. They provide all the policy attributes that are not provided in the initial access request. The risk score and attributes pushed to the attribute collection service are provided to the authorization service through PIPs.
- Context-based access includes ready-to-use PIP implementations that provide the policy attributes required. We can also provide custom policy attributes to the authorization service through a custom PIP.
- Policy decision point (PDP)
- The runtime authorization service is the policy decision point for context-based access. This service is configured to use the PEP context-based access plug-in. The authorization decision is based on an authorization policy that uses policy attributes and PIPs specific to context-based access. The PIPs provide information, such as risk score, user location, and device type.
- The policy administration point (PAP)
- The ISAM appliance is the policy administration point for context-based access. Context-based access provides an administrative console for configuring and managing the policies, risk profiles, attributes, and weights, which are required for calculating risk.
Parent topic: Overview of context-based access