Traverse permission
The traverse permission (T) specifies that a user or group that is identified in the ACL entry has permission to pass through this container object to gain access to a protected resource. Security Verify Access access control depends on the following conditions:
- The permission that controls the requested object must contain appropriate access permissions for the requesting user.
- The requested object must be accessible to the requesting user. Accessibility to protected objects is controlled by the traverse (T) permission.
The traverse permission is applied only to container objects in the protected object space.
If there are no permissions defined for a user, that user cannot even traverse the root container object. This user cannot gain access at all to the protected object space, regardless of any permissions that might be granted lower in the tree.
A protected object is accessible if the requester possesses the traverse permission on each ACL attached to container objects above the requested resource on the path towards root and including root. Figure 1 illustrates how the traverse permission works. Within the fictional ACME Corporation, there is an Engineering container object (directory), which contains a TechPubs directory. Kate (user kate) is a member of the Sales department and requires traversing to the Engineering/TechPubs/ directory tree to review a release note file (release_note). The administrator provides traverse for any-authenticated at the root. The administrator provides traverse permission for group sales on the Engineering directory. The TechPubs directory inherits the ACL from the Engineering directory. Although Kate has no other permissions in these two directories, she can pass (traverse) through these directories to access the required file. Because this file has read permission for Kate, she can view the file.
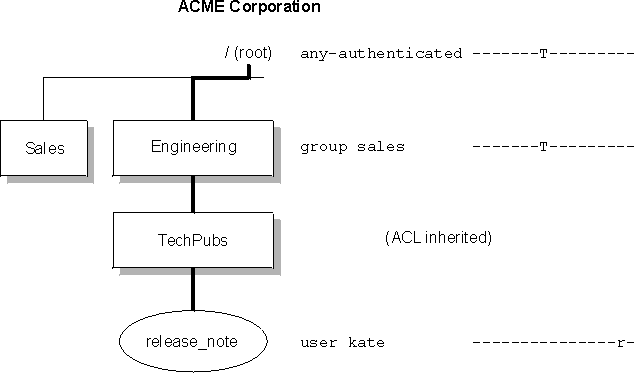
We can easily restrict access to the hierarchy below a specified container object without resetting individual permissions on these objects. Delete the traverse permission from the appropriate ACL policy. Deleting traverse permission on a directory object protects all objects lower in the hierarchy, even if those objects have other less restrictive ACL policies.
For example, sales group does not have the traverse permission on the Engineering directory. User kate cannot access the release_note file even though the user has read permission for that file.
Parent topic: Sparse security policy model