Protected object space
Security Verify Access conceptualizes resources in a domain by showing a virtual representation called the protected object space. The protected object space is the logical and hierarchical portrayal of resources that belong to a domain. The structure of the protected object space consists of the following types of objects:
- Resource objects
- The logical representation of actual physical resources in a domain, such as files, services, web pages, and message queues.
- Container objects
- Structural components that group resource objects hierarchically into distinct functional regions.
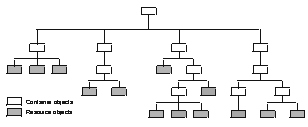
Security policy can be applied to both types of objects. Figure 1 shows a logical representation
of a protected object space with multiple container and resource objects.
This illustration shows container objects as white boxes and resource
objects as gray boxes.
 protected object space.">
protected object space.">
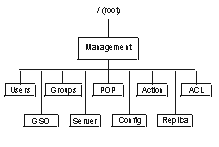
The structural top of the protected object space is the root container object. Below the root container object are one or more container objects. Each container object represents an object space that consists of a related set of resources. These resources can be resource objects or container objects. The installation of ISAM creates the /Management object space. This object space consists of the objects used to manage Security Verify Access itself. Under the /Management object space, the installation creates the following container objects:
- /Users
- /Groups
- /POP
- /Action
- /ACL
- /GSO
- /Server
- /Config
- /Replica
Figure 2 shows the complete /Management object
space that is created during the installation of ISAM.
 protected object space.">
protected object space.">
Each resource manager that protects a related set of resources creates its own object space. For example, the installation of the WebSEAL component creates the /WebSEAL object space.
Parent topic: Security Verify Access administration