Users, authorization, and resources
An administrator uses the entities that IBM Security Identity Manager provides for users, authorization, and resources to provide both initial and ongoing access in a changing organization.
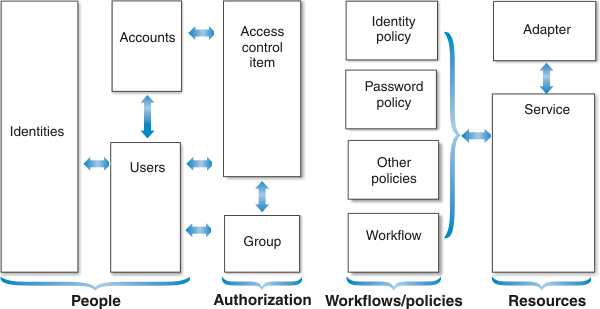
- Identities
- An identity is the subset of profile data that uniquely represents a person in one or more repositories, and includes additional information related to the person.
- Accounts
- An account is the set of parameters for a managed resource that defines your identity, user profile, and credentials.
- Users
- A user is an individual who uses IBM Security Identity Manager to manage their accounts.
- Access control items
- An access control item is data that identifies the permissions users have for a specific type of resource. We create an access control item to specify a set of operations and permissions. You then identify which groups use the access control item.
- Groups
- A group is used to control user access to functions and data in ISIM. Membership in a IBM Security Identity Manager group provides a set of default permissions and operations, as well as views, that group members need.
- Policies
- A policy is a set of considerations that influence the behavior of a managed resource (called a service in ISIM) or a user. A policy represents a set of organizational rules and the logic that IBM Security Identity Manager uses to manage other entities, such as user IDs, and applies to a specific managed resource as a service-specific policy.
- Adapters
- An adapter is a software component that provides an interface between a managed resource and ISIM Server.
- Services
- A service represents a managed resource, such as an operating system, a database application, a J2EE application server application, or a user repository. Users access these services by using an account on the service.
Parent topic: Technical overview