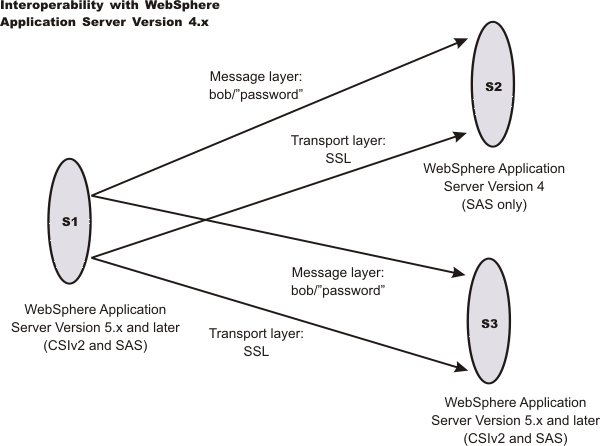

The purpose of this scenario is to show how secure interoperability can occur between different releases simultaneously while using multiple authentication protocols (Security Authentication Service (SAS) and Common Secure Interoperability Version 2 (CSIv2)). For WebSphere Application Server Version 5.x or later to communicate with a WebSphere Application Server Version 4, Version 5.x or later server must support either SAS or SAS and CSIv2 as the protocol choice. By choosing SAS and CSIv2, the Version 5.x or later server also can communicate with other Version 5.x or later servers that support CSI. If the only servers in your security domain are version 5.x or later, it is recommended that you choose CSI as the protocol because this prevents the SAS interceptors from loading. However, if a chance exists that any server has to communicate with a previous release of WebSphere Application Server, select the protocol choice of SAS and CSIv2.
Configuring the S1 server
The S1 server requires message layer authentication with an SSL transport. The protocol for the S1 server must be SAS and CSIv2. Configuration for incoming requests for the S1 server is not relevant for this scenario. To configure the S1 server for outgoing connections:
Configuring the S2 server
All previous releases of WebSphere Application Server support the SAS authentication protocol only. No special configuration steps are needed other than enabling global security on the server (S2).
Configuring the S3 server
In the administrative console, the S3 server is configured for incoming requests to support message layer authentication and to accept SSL connections. Configuration for outgoing requests and connections are not relevant for this scenario.
Related reference
Scenario 1: Basic authentication and identity assertion
Scenario 2: Basic authentication, identity assertion, and client certificates
Scenario 3: Client certificate authentication and RunAs system
Scenario 4: TCP/IP transport using a virtual private network
Example: Common Secure Interoperability Version 2 scenarios