Administration guide > Secure the deployment environment > Tutorial: Security in a mixed environment
|
| |
|
|
Secure the deployment environment > Tutorial: Integrate WebSphere eXtreme Scale security in a mixed environment with an external authenticator >
Module 2: Configure WebSphere eXtreme Scale authentication in a mixed environment
By configuring authentication, you can reliably determine the identity of the requester. WebSphere eXtreme Scale supports both client-to-server and server-to-server authentication.
Authentication flow
Figure 1. Authentication flow
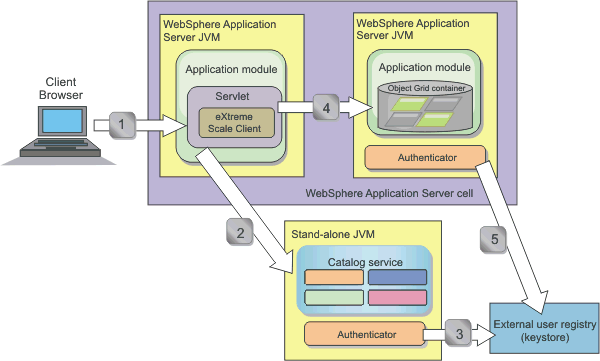
The previous diagram shows two application servers. The first application server hosts the web application, which is also a WebSphere eXtreme Scale client. The second application server hosts a container server. The catalog server is running in a stand-alone JVM (JVM) instead of WAS.
The arrows marked with numbers in the diagram indicate the authentication flow:
- An enterprise application user accesses the web browser, and logs in to the first application server with a user name and password.
The first application server sends the client user name and password to the security infrastructure to authenticate to the user registry.
This user registry is a keystore. As a result, the security information is stored on the WAS thread.
- The JSPs file acts as a WebSphere eXtreme Scale client to retrieve the security information from the client property file. The JSP application that is acting as the WebSphere eXtreme Scale client sends the WebSphere eXtreme Scale client security credential along with the request to the catalog server.
Sending the security credential with the request is considered a runAs model.
In a runAs model, the web browser client runs as a WebSphere eXtreme Scale client to access the data stored in the container server. The client uses a JVM (JVM)-wide client credential to connect to the WebSphere eXtreme Scale servers. Using the runAs model is like connecting to a database with a data source level user ID and password.
- The catalog server receives the WebSphere eXtreme Scale client credential, which includes the WAS security tokens. Then, the catalog server calls the authenticator plug-in to authenticate the client credential. The authenticator connects to the external user registry and sends the client credential to the user registry for authentication.
- The client sends the user ID and password to the container server that is hosted in the application server.
- The container service, hosted in the application server, receives the WebSphere eXtreme Scale client credential, which is the user id and password pair. Then, the container server calls the authenticator plug-in to authenticate the client credential. The authenticator connects to the keystore user registry and sends the client credential to the user registry for authentication
Learning objectives
With the lessons in this module, you learn how to:
- Configure WebSphere eXtreme Scale client security.
- Configure WebSphere eXtreme Scale catalog server security.
- Configure WebSphere eXtreme Scale container server security.
- Install and run the sample application.
Time required
This module takes approximately 60 minutes.
Lessons in this module
- Lesson 2.1: Configure WebSphere eXtreme Scale client security
You configure the client properties with a properties file. The client properties file indicates the CredentialGenerator implementation class to use. - Lesson 2.2: Configure catalog server security
A catalog server contains two different levels of security information: The first level contains the security properties that are common to all the WebSphere eXtreme Scale servers, including the catalog service and container servers. The second level contains the security properties that are specific to the catalog server. - Lesson 2.3: Configure container server security
When a container server connects to the catalog service, the container server gets all the security configurations that are configured in the Object Grid Security XML file. The ObjectGrid Security XML file defines authenticator configuration, the login session timeout value, and other configuration information. A container server also has its own server-specific security properties in the server property file. - Lesson 2.4: Install and run the sample
After authentication is configured, you can install and run the sample application.