Secure the external scheduler interface when using default messaging
Secure the external scheduler interface requires securing the JobSchedulerMDI system application and the JMS resources it uses.
The following diagram shows the actions required and the environmental artifacts to which they apply. The steps in the diagram are the steps in the procedure.
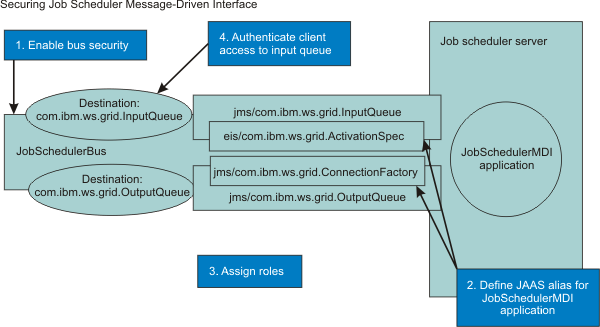
The following steps show you how to secure the external scheduler interface:
- Enable security for the job scheduler bus in the console.
- Select bus_name > Bus security > bus_name.
- Check the Enable bus security check box.
- Click OK, then Save your configuration.
- Select bus_name > Bus security > bus_name.
- Define a JAAS alias.
The JMS activation specification for the JobSchedulerMDI application requires a JAAS alias. The user ID and password defined to this alias represents access to the job scheduler inbound JMS queue, com.ibm.ws.grid.InputQueue. The JobSchedulerMDI application also uses the JAAS alias programmatically for authenticating to the outbound queue that the job scheduler uses to communicate with its clients. The outbound queue is com.ibm.ws.grid.OutputQueue. Define the JAAS alias in the console:
- Select Security > Global security > Java Authentication and Authorization Service > J2C authentication data > New.
- Define the JAAS alias.
Give the JAAS alias a name of the choice. Specify a user ID and password that provides access to the job scheduler inbound JMS queue, com.ibm.ws.grid.InputQueue, and enables authentication to the outbound queue, com.ibm.ws.grid.OutputQueue.
- Click OK and then Save to save the configuration.
- Assign the JAAS alias to the activationSpec, com.ibm.ws.grid.ActivationSpec.
- Select Security > Global security > Java Authentication and Authorization Service > J2C authentication data > New.
- Set an inter-engine authentication alias.
- Select Service integration > Buses > bus_name.
- From the inter-engine authentication alias list, select the JAAS alias definedd in the previous step.
- Click OK, then Save your configuration.
- Select Service integration > Buses > bus_name.
- Set a container-managed authentication alias.
- Select Resources > Resource Adapters > J2C connection factories > com.ibm.ws.grid.ConnectionFactory.
- From the container-managed authentication alias list, select the JAAS alias definedd in a previous step.
- Click OK, then Save your configuration.
- Select Resources > Resource Adapters > J2C connection factories > com.ibm.ws.grid.ConnectionFactory.
- Assign roles.
Roles must be assigned to authorize access to the bus and input and output bus destinations. These role assignments can be performed in the console: Security > Bus security > bus_name > Disabled > Users and groups in the bus connector role.
We can also assign roles using either of the following wsadmin commands:
- $AdminTask addUserToBusConnectorRole {-bus busName -user username}
- $AdminTask addGroupToBusConnectorRole {-bus busName -group groupname}
Make the following role assignments:
- JobSchedulerBus Assign the BusConnector role
to the following user IDs:
- com.ibm.ws.grid.ActivationSpec to permit the job scheduler to access the bus.
- Each identity used by WSGrid to authenticate client access to the input queue (see step 4). The WSGrid invoker then has permission to access the bus.
- com.ibm.ws.grid.ActivationSpec to permit the job scheduler to access the bus.
- Permit access to the com.ibm.ws.grid.InputQueue destination.
Permit access to this destination by assigning sender, receiver, and browser roles to the same user IDs. These IDs are the same IDs that we assigned the BusConnector role in the previous step. We can permit access only through wsadmin commands:
- In Jacl:
- $AdminTask addUserToDestinationRole {-type queue -bus JobSchedulerBus -destination com.ibm.ws.grid.InputQueue -role Sender -user userName}
or
$AdminTask addGroupToDestinationRole {-type queue -bus JobSchedulerBus -destination com.ibm.ws.grid.InputQueue -role Sender -group groupName}
- In Jython:
AdminTask.setInheritDefaultsForDestination('-bus WSS.JobScheduler.Bus -type queue -destination com.ibm.ws.grid.InputQueue -inherit false')
Repeat for receiver and browser roles.
- In Jacl:
- com.ibm.ws.grid.OutputQueue
Permit access to this destination by assigning the same roles to destination com.ibm.ws.grid.OutputQueue as were assigned for com.ibm.ws.grid.InputQueue in the previous step.
- $AdminTask addUserToBusConnectorRole {-bus busName -user username}
- Authenticate client access to the input queue.
- Specify the user ID and password properties in the WSGrid
input control properties file.
submitter-userid=username submitter-password=foo
- Optional: Encode the password using the WebSphere PropFilePasswordEncoder utility.
- Specify the user ID and password properties in the WSGrid
input control properties file.
Related concepts
Related tasks