Use message level security to secure web services applications
Web Services Security standards and profiles describe how to provide security and protection for SOAP messages that are exchanged in a web services environment.
Security requirements include authentication, authorization, privacy, trust, integrity, confidentiality, secure communications channels, delegation, and auditing across a spectrum of application and business topologies. See Security in a Web Services World: A Proposed Architecture and Roadmap.
Web Services Security standards
The Organization for the OASIS WS-Security specification defines the core facilities for protecting the integrity and confidentiality of a message and provides mechanisms for associating security-related claims with the message. Web Services Security is a message-level standard based on securing SOAP messages through XML digital signature, confidentiality through XML encryption, and credential propagation through security tokens. WebSphere Application Server supports v1.1 of the Web Services Security specification, including features such as encrypted header, thumbprint and signature configuration, username token profile and X.509 token profile. In addition, limited security scenario support is provided for the Kerberos v1.1 token profile, WS-SecureConversation v1.3, WS-Trust v1.3, and WS-SecurityPolicy v1.2.
The Web Services Security SOAP Message Security 1.1 specification outlines a standard set of SOAP 1.1 extensions used to build secure web services. These standards provide integrity and confidentiality protection, which are generally implemented with digital signature and encryption technologies. In addition, Web Services Security provides a general purpose mechanism for associating security tokens with messages. A typical example of the security token is a username token, in which a user name and password are included as text. Web Services Security defines how to encode binary security tokens using methods such as X.509 certificates. However, the required security tokens are not defined in the SOAP Message Security 1.1 specification. Instead, the tokens are defined in separate profiles such as the Username token profile, the X.509 token profile, and so on.
It is important to note that while Web Services Security can be used to provide message level integrity and confidentiality protection for normal SOAP message requests from a client to a service, and normal SOAP message responses from a service to a client, Web Services Security cannot be used to protect SOAP fault messages.
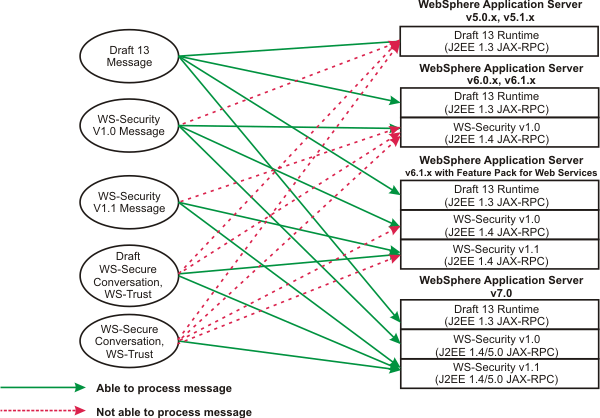
Compatibility between WS-Security Draft 13 and WS-Security standard Versions 1.0 and 1.1
The WS-Security standard has evolved over the years, from a draft to an OASIS standard. WAS v5.02 introduced support for the WS-Security Draft 13, and support for WS-Security 1.0 was introduced beginning with WAS v6.0. WS-Security v1.1 is supported by WAS v6.1 Feature Pack for Web Services, using the JAX-WS runtime only. The topic Web Services Security specification - a chronology provides more details about the evolution of this support.
A WS-Security Draft 13 client is not compatible with providers that use WS-Security v1.0 or v1.1. We must use Draft 13 client to communicate with a Draft 13 web services provider. We cannot use a Draft 13 client to communicate with a WS-Security v1.0 provider, or a v1.1 provider. This issue arises because the SOAP message format for the WS-Security header and namespace is different between a WS-Security Draft 13–enabled application and a WS-Security v1.0 or v1.1–enabled application.
The version of the WS-Security standard used also has implications for the required version of the Java EE application:
- Java EE v1.3 is used only with WS-Security Draft 13.
- Java EE v1.4 and later is used with WS-Security v1.0 (JAX-RPC and JAX-WS), and also WS-Security v1.1 (JAX-WS).
The following diagram illustrates these compatibility considerations:
To secure web services with WAS, specify several different configurations. Although there is not a specific sequence in which specify these different configurations, some configurations reference other configurations. See Web Services Security configuration considerations.
Because of the relationship between the different Web Services Security configurations, IBM recommends specified the configurations on each level of the configuration in the order described by the following sections. Choose to configure Web Services Security for the application level or the server level as it depends upon the environment and security needs.
Web Services Security programming models
JAX-WS extends JAX-RPC with support for annotations. JAX-WS applications can be secured with Web Services Security in one of two ways. The application can be secured using policy sets, or through the use of the Web Services Security API (WSS API). To secure web services using the JAX-WS programming model, begin with the topic Secure JAX-WS web services using message-level security.
The Java™ API for XML-based RPC (JAX-RPC) specification enables you to develop SOAP-based interoperable and portable web services and web service clients. JAX-RPC 1.1 provides core APIs for developing and deploying web services on a Java platform and is a part of the Web Services for Java EE platform. IBM WebSphere Application Server supports both the JAX-WS programming model and the JAX-RPC programming model. JAX-WS is the next generation web services programming model, extending the foundation provided by the JAX-RPC programming model. To secure web services using JAX-RPC, begin with the topic Secure JAX-RPC web services using message-level security.
Related concepts:
Related
Reference: