Web services security specification—a chronology
This chronology describes the process that has been used to develop the Web services security specifications. The chronology includes both the Organization for the Advancement of Structured Information Standards (OASIS) and non-OASIS activities.
Non-OASIS activities
There is an important distinction between V5.x and V6.0.x applications. The information in this article supports V5.x applications only that are used with WAS V6.0.x and later. The information does not apply to V6.0.x applications. In April 2002, IBM, Microsoft, and VeriSign proposed the Web Services Security (WS-Security) specification on their Web sites. This specification included the basic ideas of security token, XML signature, and XML encryption. The specification also defined the format for user name tokens and encoded binary security tokens. After some discussion and an interoperability test that was based on the specification, the following issues were noted:
- The specification requires that the Web services security processors understand the schema correctly so that the processor distinguishes between the ID attribute for XML signature and XML encryption.
- The freshness of the message, which indicates whether the message complies with predefined time constraints, cannot be determined.
- Digested password strings do not strengthen security.
In August 2002, IBM, Microsoft, and VeriSign published the Web Services Security Addendum, which attempted to address the previously listed issues. The following solutions were put in the addendum:
- Require a global ID attribute for XML signature and XML encryption.
- Use time stamp header elements that indicate the time of the creation, receipt, or expiration of the message.
- Use password strings that are digested with a timestamp and nonce (randomly generated token).
OASIS activities
In June 2002, OASIS received a proposed Web services security specification from IBM, Microsoft, and Verisign. The Web Services Security Technical Committee (WSS TC) was organized at OASIS soon after the submission. The technical committee included many companies including IBM, Microsoft, VeriSign, Sun Microsystems, and BEA Systems.
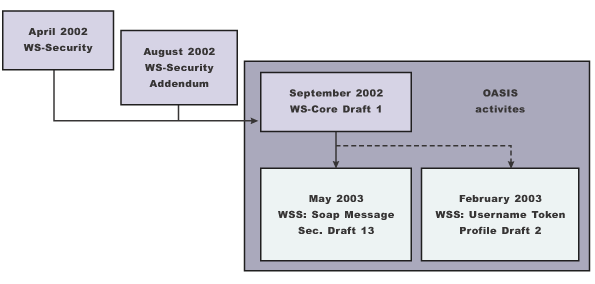
In September 2002, WSS TC published its first specification, Web Services Security Core Specification, Working Draft 01. This specification included the contents of both the original Web services security specification and its addendum.
The coverage of the technical committee became larger as the discussion proceeded. Since the Web Services Security Core Specification allows arbitrary types of security tokens, proposals were published as profiles. The profiles described the method for embedding tokens, including Security Assertion Markup Language (SAML) tokens and Kerberos tokens imbedded into the Web services security messages. Subsequently, the definitions of the usage for user name tokens and X.509 binary security tokens, which were defined in the original Web Services Security Specification, were divided into the profiles. WAS supports the following specifications:
- Web Services Security: SOAP Message Security Draft 13 (formerly Web Services
Security Core Specification)
- Web Services Security: Username Token Profile Draft 2
The following figure shows the various Web services security-related specifications. As indicated in the figure, the current support level for Web services security: SOAP message security is based on Draft 13 from May 2003. The current support level for Web services security user name token profiles, is based on Draft 2 from February 2003. Figure 1. Web services security specification support
Related concepts
Web services security and Java 2 Platform, Enterprise Edition security relationship
Web services security model in WAS
Related Reference
Web services security support
Related information
Securing Web services for V5.x applications based on WS-Security