Set up LDAP
Overview
Before we can configure IBM WebSphere Portal to work with the LDAP server, the LDAP user registry must have some minimal user and group information already populated.
- Name Length
- Required groups and users
- Portal administrator users
- Example of a customized directory structure
Name Length
Active Directory has a limitation of 20 characters for the user account name; for example, uid or cn. If you create a user with more than 20 characters, you will receive the following error:
EJPSG0015E: Data Backend Problem com.ibm.websphere.wmm.exception.WMMSystemException:
The following Naming Exception occurred during processing:
"javax.naming.NamingException:
[LDAP: error code 80 - 00000523:
SysErr: DSID-031A0B4C, problem 22 (Invalid argument), data 0];
remaining name 'cn=yournamefirstname_lastname,dc=yourco';
resolved object com.sun.jndi.ldap.LdapCtx@6b9c4ac9".
Required groups
- wpsadmins or an equivalent.
See PortalAdminGroupId in wpconfig.properties. Members of this group have administrative authority within WebSphere Portal.
- wpsContentAdministrators and wpsDocReviewer
Create if content management functions are configured. These groups should be created in the LDAP with the same authority as granted to the wpsadmins group.
Required user accounts:
- WebSphere Portal administrative user (wpsadmin)
This is the first administrator account for WebSphere Portal. This account is also a member of the wpsadmins group.
- Security Server ID account name for IBM WAS security (wasadmin)
This account is configured into WAS. It becomes the ID that is used to administer WebSphere Application Server. If this account is different from the following LDAP access accounts, then this account needs no special privileges in the LDAP user registry.
- An LDAP access account for WAS (wpsbind).
This identity is used by WAS to access the LDAP user registry. If you keep the default values for the Bind Distinguished Name of WAS in the wpconfig.properties file, wpsbind will be used as the Bind Distinguished Name. The required privileges for this account in the user registry are as follows:
- Write:
To allow users or portal administrators to create and modify directory attributes through self-registration and self-care screens or the Manage Users and Groups portlet, the Bind DN (LDAPBindID) user must have permission to write and search the LDAP user registry that WebSphere Portal uses or the subtree of that directory rooted at the LDAP suffix.
- Read:
If you will not use any WebSphere Portal facilities to write to the user registry, but the user registry security policies do not allow anonymous searches of the directory, the Bind DN (LDAPBindID) user must have permission to read and search the LDAP user registry that WebSphere Portal uses or the subtree of that directory rooted at the LDAP suffix.
Use the same user ID for more than one purpose.
- An LDAP access account that Member Manager uses to access the LDAP directory.
This ID is not required when using LDAP with realm support. This does not have to be the root administrative ID for the directory, simply an ID that has sufficient privileges to the directory to allow the operations that WebSphere Portal will perform.
If WebSphere Portal only reads from the directory and does not make updates, an ID with read privileges to the directory is sufficient. If WebSphere Portal updates the directory (creates users or makes user profile updates to the directory) then an ID with write privileges is required.
If you use IBM Lotus Domino Directory as the LDAP server, see Set up Domino Directory for details on adding users with special permissions to the Lotus Domino Domain.
Portal administrator users
We can select an existing LDAP user to act as the portal administrator. If you want to create a new user to administer the portal, you should create the user before continuing. To create a new user as the portal administrator, use your directory administration tools.
LDAP Relative Distinguished Name (RDN) prefixes, such as cn=, uid=, or ou=, should be entered in lowercase. Uppercase or mixed case can cause problems with subsequent case-sensitive queries of the database user registry and WebSphere Portal databases.
Example of a customized directory structure
The following is an example of one possible custom LDAP structure. This varies from the defaults listed in the other LDAP setup topics in several ways. It is more complex than the other default example LDAP trees; that is, there are more layers of names between the root and the leaves. It is also wider, with users and groups scattered in different places throughout the tree. Also, users and groups are sibling objects under a common parent in the layout. However, WebSphere Portal can be configured to accept this LDAP user registry layout. The example below helps you determine the appropriate values when configuring WebSphere Portal to work with the specific directory layout.
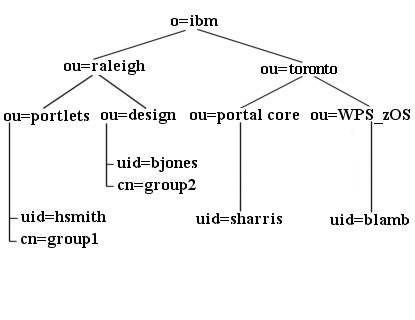
- LDAP suffix="o=ibm" or for a US-only portal, this value could be "ou=raleigh,o=ibm"
- user prefix="uid"
- user suffix="o=ibm" or for a US-only portal, this value could be "ou=raleigh,o=ibm"
- group prefix="cn"
- group suffix="o=ibm" or for a US-only portal,"ou=raleigh,o=ibm"
- Portal administrator DN="uid=hsmith,ou=portlets,ou=raleigh,o=ibm"
- Portal administrator group="cn=group1,ou=portlets,ou=raleigh,o=ibm"
Next steps
Select the LDAP server you want to set up from the following list:
- Set up Tivoli Directory Server
- Set up Domino Directory
- Set up Active Directory
- Set up Active Directory Application Mode
- Set up Sun Java System Directory Server
- Set up Novell eDirectory
Parent topic:
LDAP user registry