Configuration of container authentication
The configuration of EJB container authentication can be done through the WebSphere Administrative Console:
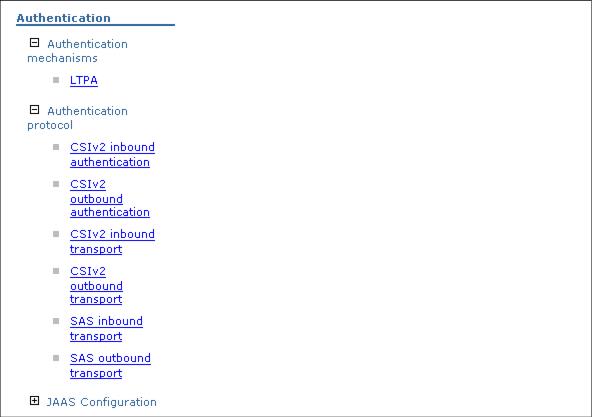
In the Global Security administration page, go to the Authentication section.
Click Authentication protocol to display all the avialable options as shown in Figure 7-19.
Container authentication can be set for inbound and outbound requests independently. Inbound means all the incoming communication that comes from a client to the server, outbound means all the outgoing communication that goes from the server toward other servers.
Figure 7-19 The Authentication section of Global Security administration page
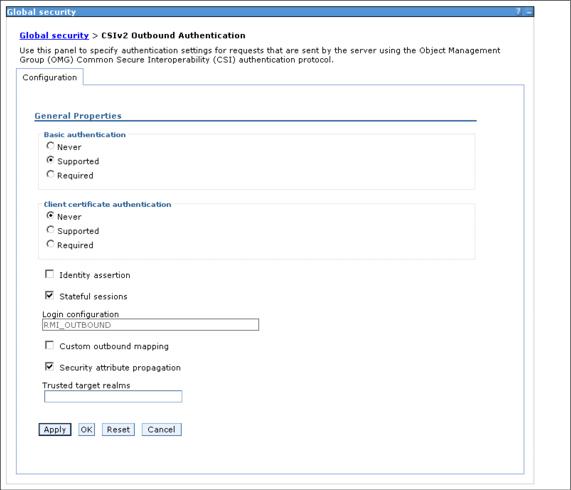
After selecting the CSIV2 inbound or the outbound authentication page link, you will get a page as displayed in Figure 7-20.
Figure 7-20 Setting CSIV2 Outbound authentication properties
Set Basic Authentication with one the following options:
Never
Select Never to indicate that the server is not configured to accept message layer authentication from any client.
Supported
Selecting Supported indicates that this server accepts basic authentication. However, other methods of authentication can occur if configured and anonymous requests are accepted.
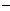
Required
Selecting Required indicates that only clients configured to authenticate to this server through the message layer can invoke requests on the server.
Set Client certificate authentication with one of the following options:
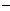
Never
Selecting Never indicates that the server is not configured to accept client certificate authentication from any client.
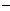
Supported
Selecting Supported indicates that the server accepts SSL client certificate authentication; however, other methods of authentication can occur (if configured) and anonymous requests are accepted.
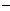
Required
Selecting Required indicates that only clients that are configured to authenticate to the server through SSL client certificates can invoke requests on the server.
To enable client certificate authentication for the IIOP transport layer, set the SSL to be required or supported. The prerequisite on the client side is that the client must have set a key database with a client certificate. As always, the certificate can be signed by a known Certificate Authority. Using an imported self-signed public key from the client is also an option, although is not recommended.