SSL session ID
During establishment of an SSL encrypted session, a handshake protocol is used to negotiate a session ID. This handshaking phase consumes a good deal of CPU power, so directing HTTPS requests to the same server, using the already established SSL session, saves processing time and increases the overall performance of the HTTP server.
Load Balancer watches the packets during the handshake phase and holds information about the session ID if SSL session negotiation is detected.
The forwarding method used to configure SSL session ID affinity is the kernel-based content-based routing function called cbr forwarding.
The steps for configuring this are as follows:
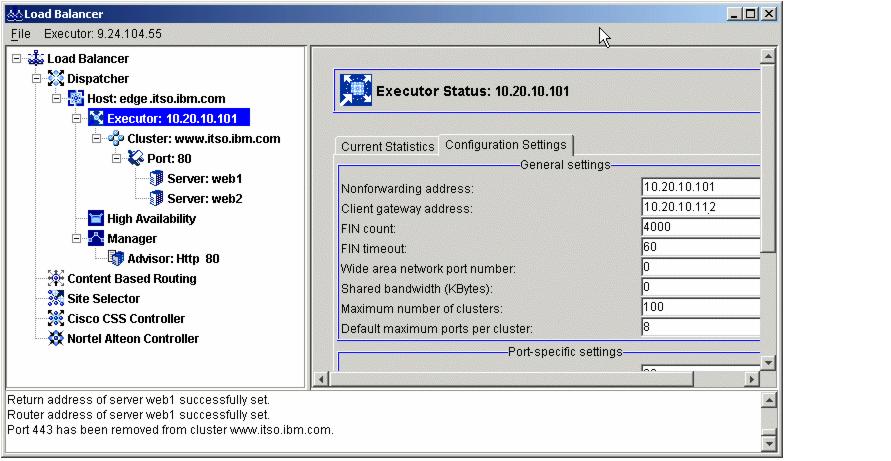
Figure 4-12 Client gateway address configuration
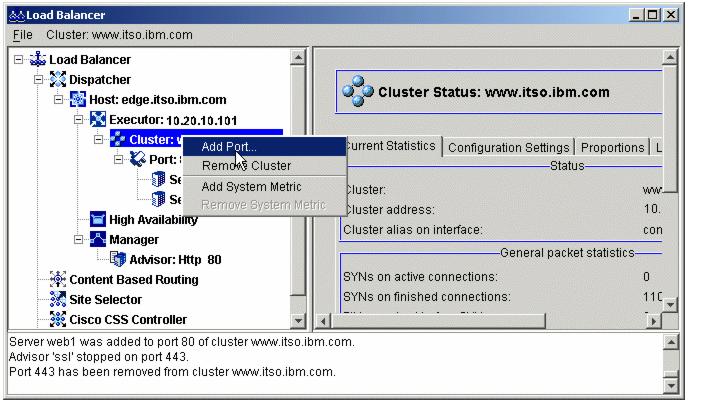
Figure 4-13 Adding a port
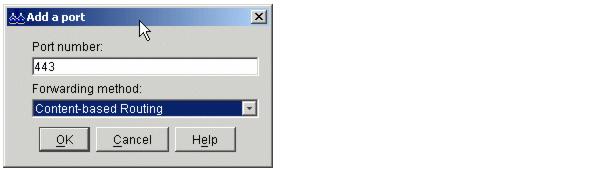
Figure 4-14 Setting the port number and forwarding method
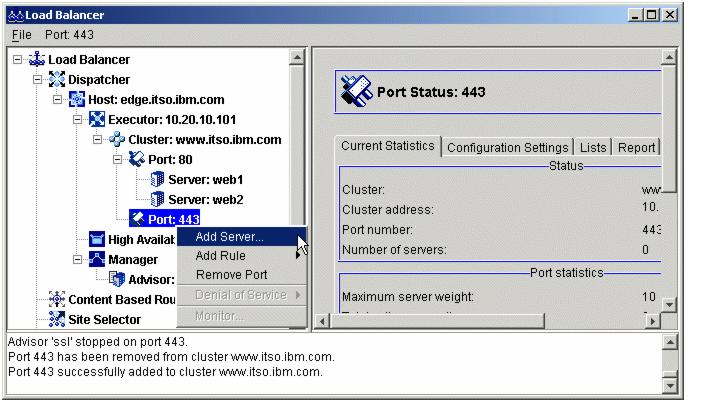
Figure 4-15 Adding a server to the port
The return address is a unique address or host name that is configured on the Dispatcher machine. Dispatcher uses the return address as its source address when load balancing the client's request to the server. This ensures that the server will return the packet to the Dispatcher machine rather than sending the packet directly to the client. The return address cannot be the same as the cluster address, server address, or non-forwarding address (NFA). We added a new alias to the network interface (10.20.10.110) to be configured as the return address.
AIX: ifconfig en0 alias 10.20.10.110 netmask 255.255.0.0
Windows: dsconfig en0 alias 10.20.10.110 netmask 255.255.0.0
The network router address is the address for the router to access the remote server. If this is a locally attached server, enter the server address. We set the router address to our default gateway address 10.20.10.111, as shown in Figure 4-16.
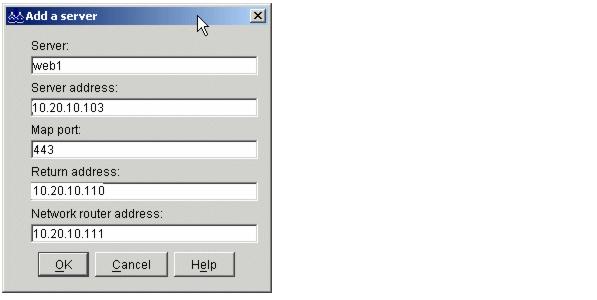
Figure 4-16 Configuration and addresses for cbr forwarding
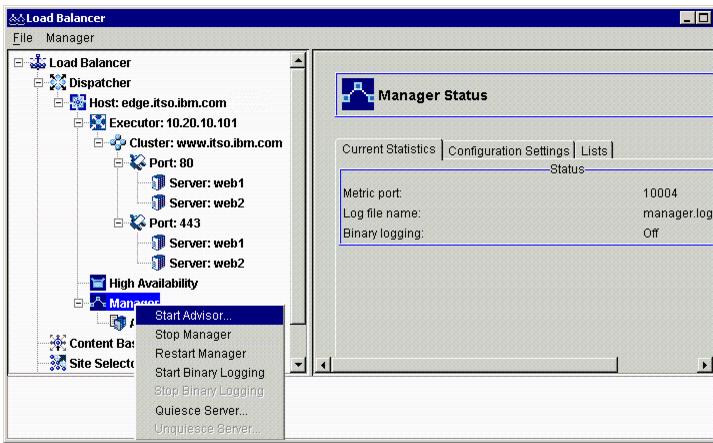
Figure 4-17 Starting an advisor
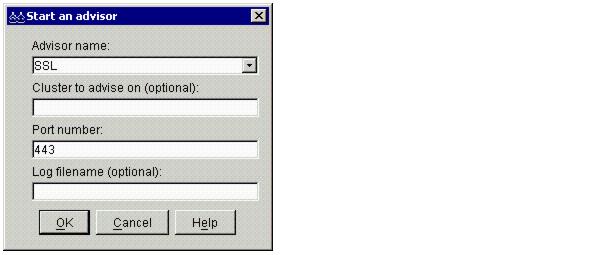
Figure 4-18 Configuring SSL advisor
To set up SSL session ID affinity, you need to configure a sticky time value, such as 60 seconds, to port 443, as illustrated in Figure 4-19.
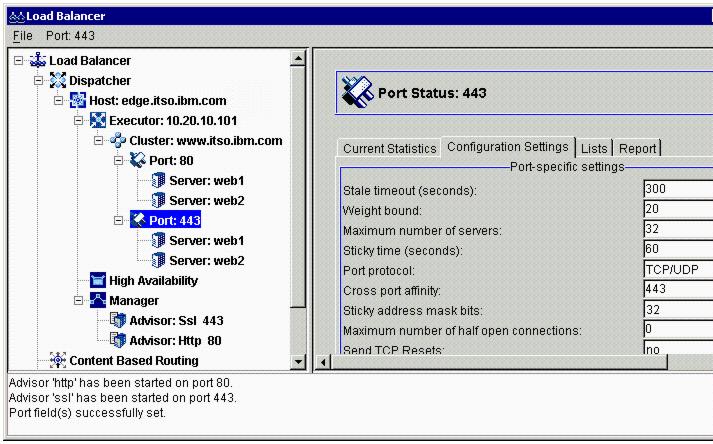
Figure 4-19 Configuring sticky time
The graph in Figure 4-20 shows the traffic directed to the cluster when SSL session ID affinity for port 443 is configured. All connections are dispatched to the same server.
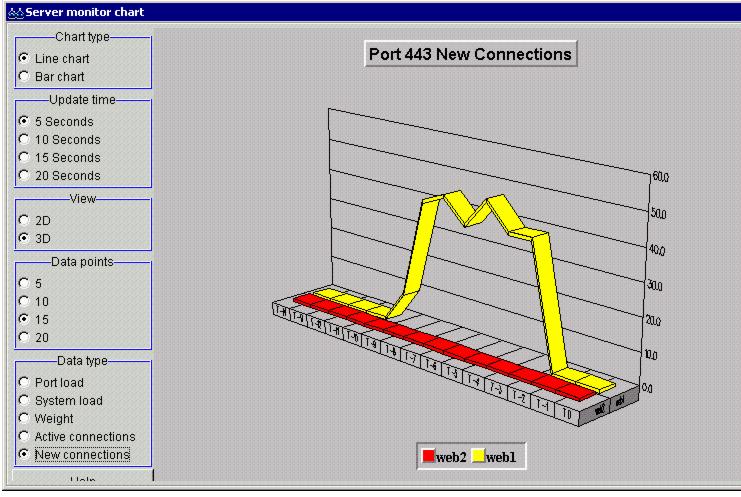
Figure 4-20 Request distribution using SSL session ID affinity
WebSphere is a trademark of the IBM Corporation in the United States, other countries, or both.
IBM is a trademark of the IBM Corporation in the United States, other countries, or both.