Configure LDAP ACL management with JNDI (WebSphere Application Server V7)
Use LDAP to define the users and groups who can install mobile applications with the Application Center using the JNDI environment.
Since IBM Worklight v6.0, two configuration approaches are available: the JNDI API or the Virtual Member Manager (VMM) API. This procedure shows you how to use the JNDI API to configure LDAP based on the federated repository configuration or with the stand-alone LDAP registry. Only the simple type of LDAP authentication is supported.
- Log in to the WebSphere Application Server console.
- Select Applications > Application Types > WebSphere enterprise applications.
- Click IBM_Application_Center_Services.
- In the Web Module Properties section, select "Environment entries for Web modules".
- For the ibm.appcenter.ldap.vmm.active entry, assign the value "false".
- For the ibm.appcenter.ldap.active entry, assign the value "true".
- For the ibm.appcenter.ldap.vmm.active entry, assign the value "false".
- Continue to configure the remaining entries:
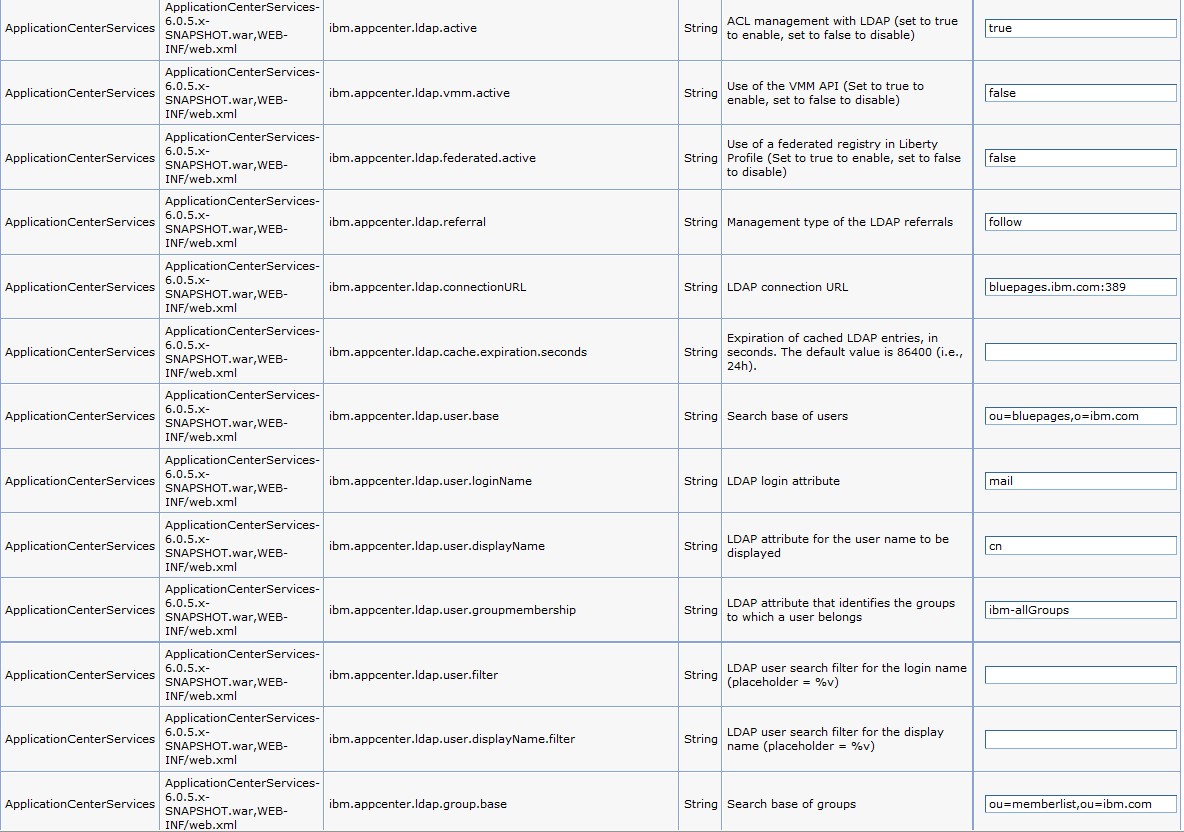
- ibm.appcenter.ldap.connectionURL: LDAP connection URL.
- ibm.appcenter.ldap.user.base: search base
for users.
- ibm.appcenter.ldap.user.loginName: LDAP login attribute.
- ibm.appcenter.ldap.user.displayName: LDAP attribute for the user name to be displayed, for example, a person's
full name.
- ibm.appcenter.ldap.group.base: search base
for groups.
- ibm.appcenter.ldap.group.name: LDAP attribute for the group name.
- ibm.appcenter.ldap.group.uniquemember: LDAP attribute that identifies the members of a group.
- ibm.appcenter.ldap.user.groupmembership:
LDAP attribute that identifies the groups that a user belongs to.
- ibm.appcenter.ldap.group.nesting: management of nested groups. If nested groups are not managed, set the value to false.
- ibm.appcenter.ldap.cache.expiration.seconds:
delay in seconds before the LDAP cache expires. If no value is entered, the default value is 86400, which is equal to 24 hours.
Changes to users and groups on the LDAP server become visible to the Application Center after a delay, which is specified by ibm.appcenter.ldap.cache.expiration.seconds. The Application Center maintains a cache of LDAP data and the changes only become visible after the cache expires. By default, the delay is 24 hours. If we do not want to wait for this delay to expire after changes to users or groups, we can call this command to clear the cache of LDAP data:
- acdeploytool.sh -clearLdapCache -s serverurl -c context -u user -p password
See Using the stand-alone tool to clear the LDAP cache for details.
- Enter the value of each property.
- Click OK and save the configuration.
- ibm.appcenter.ldap.connectionURL: LDAP connection URL.
- Option: If the LDAP external SASL authentication mechanism is required to bind to the LDAP server, configure the ibm.appcenter.ldap.active.sasl property, which defines the value of the security authentication mechanism. The value depends on the LDAP server; usually, it is set to "EXTERNAL".
- Option: If security binding is required, follow
this step. Configure the following entries:
- ibm.appcenter.ldap.security.binddn: the distinguished name of the user permitted to search the LDAP directory.
- ibm.appcenter.ldap.security.bindpwd: the password of the user permitted to search the LDAP directory. The password can be encoded with the "WebSphere PropFilePasswordEncoder" utility. Run the utility before we configure the ibm.appcenter.ldap.security.bindpwd custom property.
- Enter the value of each optional property and click OK. Set the value of the ibm.appcenter.ldap.security.bindpwd property to the encoded password generated by the "WebSphere PropFilePasswordEncoder" utility.
- Save the configuration.
- ibm.appcenter.ldap.security.binddn: the distinguished name of the user permitted to search the LDAP directory.
- Option: If LDAP referrals must be handled, follow
this step. Configure ibm.appcenter.ldap.referral:
support of referrals by the JNDI API. • If no value is given, the JNDI API will not handle LDAP referrals. Possible values
are:
- ignore: ignore referrals found in the LDAP server.
- follow: automatically follow referrals
found in the LDAP server.
- throw: cause an exception to occur for each referral found in the LDAP server.
- Enter the value of the property and click OK.
- Save the configuration.
- ignore: ignore referrals found in the LDAP server.
- Option: If users and groups are defined in the same subtree (the properties ibm.appcenter.ldap.user.base and ibm.appcenter.ldap.group.base have the same value), follow this step. Configure the following entries:
- ibm.appcenter.ldap.user.filter: LDAP user search filter for the attribute of user login name. Use %v as the placeholder for the login name attribute.
- ibm.appcenter.ldap.group.filter: LDAP group
search filter. Use %v as the placeholder for the group attribute.
- ibm.appcenter.ldap.user.displayName.filter: LDAP user search filter for the attribute of user display name. Use %v as the placeholder for the user display name attribute.
- Enter the value of each optional property and click OK.
- Save the configuration.
- ibm.appcenter.ldap.user.filter: LDAP user search filter for the attribute of user login name. Use %v as the placeholder for the login name attribute.
Results
The following figure shows the values to assign to each property.
See List of JNDI properties for the Application Center for a complete list of properties we can set.
Figure 1. Environment entries and their values (LDAP and WebSphere Application Server V7)
Parent topic: LDAP with WebSphere Application Server V7