Publish/subscribe security
The components and interactions that are involved in publish/subscribe are described as an introduction to the more detailed explanations and examples that follow.
There are a number of components involved in publishing and subscribing to a topic. Some of the security relationships between them are illustrated in Figure 1 and described in the following example.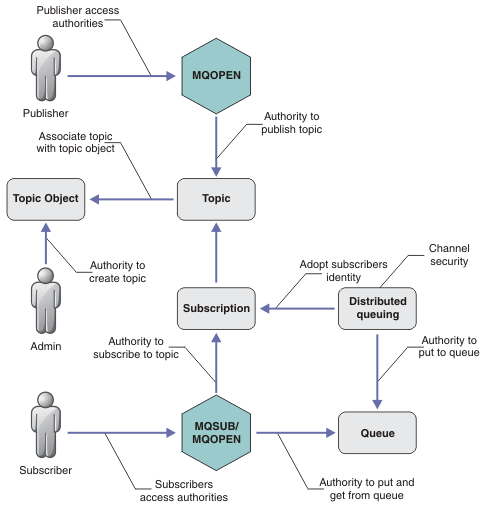
- Topics
- Topics are identified by topic strings, and are typically organized into trees, see Topic trees. We need to associate a topic with a topic object to control access to the topic. Topic security model explains how you secure topics using topic objects.
- Administrative topic objects
- We can control who has access to a topic, and for what purpose, by using the command setmqaut with a list of administrative topic objects. See the examples, Grant access to a user to subscribe to a topic and Grant access to a user to publish to a topic. For controlling access to topic objects on z/OS, see Profiles for topic security.
- Subscriptions
-
Subscribe to one or more topics by creating a subscription supplying a topic string, which can include wildcards, to match against the topic strings of publications. For further details, see:
- Subscribe using a topic object
- Subscribing using the topic object name
- Subscribe using a topic
- Subscribing using a topic string where the topic node does not exist
- Subscribe using a topic with wildcards
- Subscribing using a topic string that contains wildcard characters
A subscription contains information about the identity of the subscriber and the identity of the destination queue on to which the publications are to be placed. It also contains information about how the publication is to be placed on the destination queue.
As well as defining which subscribers have the authority to subscribe to certain topics, we can restrict subscriptions to being used by an individual subscriber. We can also control what information about the subscriber is used by the queue manager when publications are placed on to the destination queue. See Subscription security.
- Queues
-
The destination queue is an important queue to secure. It is local to the subscriber, and publications that matched the subscription are placed onto it. We need to consider access to the destination queue from two perspectives:
- Put a publication on to the destination queue.
- Getting the publication off the destination queue.
The queue manager puts a publication onto the destination queue using an identity provided by the subscriber. The subscriber, or a program that has been delegated the task of getting publications, takes messages off the queue. See Authority to destination queues.
There are no topic object aliases, but we can use an alias queue as the alias for a topic object. If you do so, as well as checking authority to use the topic for publish or subscribe, the queue manager checks authority to use the queue.
- Publish/subscribe security between queue managers
-
Your permission to publish or subscribe to a topic is checked on the local queue manager using local identities and authorizations. Authorization does not depend on whether the topic is defined or not, nor where it is defined. Consequently, we need to perform topic authorization on every queue manager in a cluster when clustered topics are used.
Note: The security model for topics differs from the security model for queues. We can achieve the same result for queues by defining a queue alias locally for every clustered queue.
Queue managers exchange subscriptions in a cluster. In most IBM MQ cluster configurations, channels are configured with PUTAUT=DEF to place messages onto target queues using the authority of the channel process. We can modify the channel configuration to use PUTAUT=CTX to require the subscribing user to have authority to propagate a subscription onto another queue manager in a cluster.
Publish/subscribe security between queue managers describes how to change your channel definitions to control who is allowed to propagate subscriptions onto other servers in the cluster.
- Authorization
- We can apply authorization to topic objects, just like queues and other objects. There are three authorization operations, pub, sub, and resume that we can apply only to topics. The details are described in Specify authorities for different object types.
- Function calls
-
In publish and subscribe programs, like in queued programs, authorization checks are made when objects are opened, created, changed, or deleted. Checks are not made when MQPUT or MQGET MQI calls are made to put and get publications.
To publish a topic, perform an MQOPEN on the topic, which performs the authorization checks. Publish messages to the topic handle using the MQPUT command, which performs no authorization checks.
To subscribe to a topic, typically you perform an MQSUB command to create or resume the subscription, and also to open the destination queue to receive publications. Alternatively, perform a separate MQOPEN to open the destination queue, and then perform the MQSUB to create or resume the subscription.
Whichever calls we use, the queue manager checks that we can subscribe to the topic and get the resulting publications from the destination queue. If the destination queue is unmanaged, authorization checks are also made that the queue manager is able to place publications on the destination queue. It uses the identity it adopted from a matching subscription. It is assumed that the queue manager is always able to place publications onto managed destination queues.
- Roles
-
Users are involved in four roles in running publish/subscribe applications:
- Publisher
- Subscriber
- Topic administrator
- IBM MQ Administrator - member of group mqm
Define groups with appropriate authorizations corresponding to the publish, subscribe, and topic administration roles. We can then assign principals to these groups authorizing them to perform specific publish and subscribe tasks.
In addition, we need to extend the administrative operations authorizations to the administrator of the queues and channels responsible for moving publications and subscriptions.
Topic security model
Only defined topic objects can have associated security attributes. For a description of topic objects, see Administrative topic objects. The security attributes specify whether a specified user ID, or security group, is permitted to perform a subscribe or a publish operation on each topic object.
The security attributes are associated with the appropriate administration node in the topic tree. When an authority check is made for a particular user ID during a subscribe or publish operation, the authority granted is based on the security attributes of the associated topic tree node.
The security attributes are an access control list, indicating what authority a particular operating system user ID or security group has to the topic object.
Consider the following example where the topic objects have been defined with the security attributes, or authorities shown:| Topic name | Topic string | Authorities - not z/OS | z/OS authorities |
|---|---|---|---|
| SECROOT | SEC | None | None |
| SECGOOD | SEC/GOOD | usr1+subscribe | ALTER
HLQ.SUBSCRIBE.SECGOOD |
| SECBAD | SEC/BAD | None | None
HLQ.SUBSCRIBE.SECBAD |
| SECCOMB | SEC/COMB | None | None
HLQ.SUBSCRIBE.SECCOMB |
| SECCOMBB | SEC/COMB/GOOD/BAD | None | None
HLQ.SUBSCRIBE.SECCOMBB |
| SECCOMBG | SEC/COMB/GOOD | usr2+subscribe | ALTER
HLQ.SUBSCRIBE.SECCOMBG |
| SECCOMBN | SEC/COMB/BAD | None | None
HLQ.SUBSCRIBE.SECCOMBN |
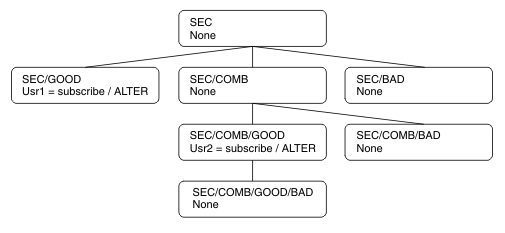 The examples listed give the following authorizations:
The examples listed give the following authorizations:
- At the root node of the tree /SEC, no user has authority at that node.
- usr1 has been granted subscribe authority to the object /SEC/GOOD
- usr2 has been granted subscribe authority to the object /SEC/COMB/GOOD
Subscribing using the topic object name
When subscribing to a topic object by specifying the MQCHAR48 name, the corresponding node in the topic tree is located. If the security attributes associated with the node indicate that the user has authority to subscribe, then access is granted.
If the user is not granted access, the parent node in the tree determines if the user has authority to subscribe at the parent node level. If so, then access is granted. If not, then the parent of that node is considered. The recursion continues until a node is located that grants subscribe authority to the user. The recursion stops when the root node is considered without authority having been granted. In the latter case, access is denied.
In short, if any node in the path grants authority to subscribe to that user or application, the subscriber is allowed to subscribe at that node, or anywhere below that node in the topic tree.
The root node in the example is SEC.
The user is granted subscribe authority if the access control list indicates that the user ID itself has authority, or that an operating system security group of which the user ID is a member has authority.
So, for example:- If usr1 tries to subscribe, using a topic string of SEC/GOOD, the subscription would be allowed as the user ID has access to the node associated with that topic. However, if usr1 tried to subscribe using topic string SEC/COMB/GOOD the subscription would not be allowed as the user ID does not have access to the node associated with it.
- If usr2 tries to subscribe, using a topic string of SEC/COMB/GOOD the subscription would be allowed to as the user ID has access to the node associated with the topic. However, if usr2 tried to subscribe to SEC/GOOD the subscription would not be allowed as the user ID does not have access to the node associated with it.
- If usr2 tries to subscribe using a topic string of SEC/COMB/GOOD/BAD the subscription would be allowed to because the user ID has access to the parent node SEC/COMB/GOOD.
- If usr1 or usr2 tries to subscribe using a topic string of /SEC/COMB/BAD, neither would be allowed as they do not have access to the topic node associated with it, or the parent nodes of that topic.
A subscribe operation specifying the name of a topic object that does not exist results in an MQRC_UNKNOWN_OBJECT_NAME error.
Subscribing using a topic string where the topic node exists
The behavior is the same as when specifying the topic by the MQCHAR48 object name.
Subscribing using a topic string where the topic node does not exist
Consider the case of an application subscribing, specifying a topic string representing a topic node that does not currently exist in the topic tree. The authority check is performed as outlined in the previous section. The check starts with the parent node of that which is represented by the topic string. If the authority is granted, a new node representing the topic string is created in the topic tree.
For example, usr1 tries to subscribe to a topic SEC/GOOD/NEW. Authority is granted as usr1 has access to the parent node SEC/GOOD. A new topic node is created in the tree as the following diagram shows. The new topic node is not a topic object it does not have any security attributes associated with it directly; the attributes are inherited from its parent.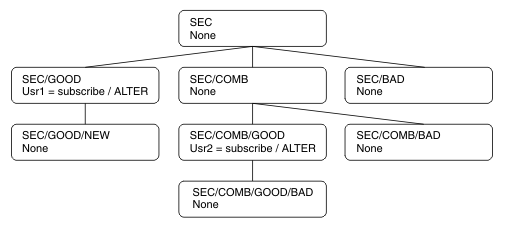
Subscribing using a topic string that contains wildcard characters
Consider the case of subscribing using a topic string that contains a wildcard character. The authority check is made against the node in the topic tree that matches the fully qualified part of the topic string.
So, if an application subscribes to SEC/COMB/GOOD/*, an authority check is carried out as outlined in the previous two sections on the node SEC/COMB/GOOD in the topic tree.
Similarly, if an application needs to subscribe to SEC/COMB/*/GOOD, an authority check is carried out on the node SEC/COMB.
Authority to destination queues
When subscribing to a topic, one of the parameters is the handle hobj of a queue that has been opened for output to receive the publications.
If hobj is not specified, but is blank, a managed queue is created if the following conditions apply:- The MQSO_MANAGED option has been specified.
- The subscription does not exist.
- Create is specified.
If hobj is blank, and we are altering or resuming an existing subscription, the previously provided destination queue could be either managed or unmanaged.
The application or user making the MQSUB request must have the authority to put messages to the destination queue it has provided; in effect authority to have published messages put on that queue. The authority check follows the existing rules for queue security checking.
The security checking includes alternate user ID and context security checks where required. To be able to set any of the Identity context fields we must specify the MQSO_SET_IDENTITY_CONTEXT option as well as the MQSO_CREATE or MQSO_ALTER option. We cannot set any of the Identity context fields on an MQSO_RESUME request.
If the destination is a managed queue, no security checks are performed against the managed destination. If we are allowed to subscribe to a topic it is assumed that we can use managed destinations.
Publishing using the topic name or topic string where the topic node exists
The security model for publishing is the same as that for subscribing, with the exception of wildcards. Publications do not contain wildcards; so there is no case of a topic string containing wildcards to consider.
The authorities to publish and subscribe are distinct. A user or group can have the authority to do one without necessarily being able to do the other.
When publishing to a topic object by specifying either the MQCHAR48 name or the topic string, the corresponding node in the topic tree is located. If the security attributes associated with the topic node indicates that the user has authority to publish, then access is granted.
If access is not granted, the parent node in the tree determines if the user has authority to publish at that level. If so, then access is granted. If not, the recursion continues until a node is located which grants publish authority to the user. The recursion stops when the root node is considered without authority having been granted. In the latter case, access is denied.
In short, if any node in the path grants authority to publish to that user or application, the publisher is allowed to publish at that node or anywhere below that node in the topic tree.
Publishing using the topic name or topic string where the topic node does not exist
As with the subscribe operation, when an application publishes, specifying a topic string representing a topic node that does not currently exist in the topic tree, the authority check is performed starting with the parent of the node represented by the topic string. If the authority is granted, a new node representing the topic string is created in the topic tree.
Publishing using an alias queue that resolves to a topic object
If you publish using an alias queue that resolves to a topic object then security checking occurs on both the alias queue and the underlying topic to which it resolves.
The security check on the alias queue verifies that the user has authority to put messages on that alias queue and the security check on the topic verifies that the user can publish to that topic. When an alias queue resolves to another queue, checks are not made on the underlying queue. Authority checking is performed differently for topics and queues.
Closing a subscription
There is additional security checking if you close a subscription using the MQCO_REMOVE_SUB option if you did not create the subscription under this handle.
A security check is performed to ensure that we have the correct authority to do this as the action results in the removal of the subscription. If the security attributes associated with the topic node indicate that the user has authority, then access is granted. If not, then the parent node in the tree is considered to determine if the user has authority to close the subscription. The recursion continues until either authority is granted or the root node is reached.
Defining, altering, and deleting a subscription
No subscribe security checks are performed when a subscription is created administratively, rather than using an MQSUB API request. The administrator has already been given this authority through the command.
Security checks are performed to ensure that publications can be put on the destination queue associated with the subscription. The checks are performed in the same way as for an MQSUB request.
The user ID that is used for these security checks depends upon the command being issued. If the SUBUSER parameter is specified it affects the way the check is performed, as shown in Table 2:| Command | SUBUSER specified and blank | SUBUSER specified and completed | SUBUSER not specified |
|---|---|---|---|
| DEFINE LIKE | Use the administrator ID | Use the user ID specified in SUBUSER | Use the user ID from the LIKE subscription |
| DEFINE with no LIKE | Use the administrator ID | Use the user ID specified in SUBUSER | Use the user ID from the SYSTEM.DEFAULT.SUB subscription - if blank, use the administrator ID |
| ALTER | Use the administrator ID | Use the user ID specified in SUBUSER | Use the user ID from the existing subscription |
The only security check performed when deleting subscriptions using the DELETE SUB command is the command security check.
- Example publish/subscribe security setup
This section describes a scenario that has access control set up on topics in a way that allows the security control to be applied as required. - Subscription security
- Publish/subscribe security between queue managers
Publish/subscribe internal messages, such as proxy subscriptions and publications, are put to publish/subscribe system queues using normal channel security rules. The information and diagrams in this topic highlight the various processes and user IDs involved in the delivery of these messages.
Parent topic: Securing IBM MQ