Scenario 4: TCP/IP transport using VPN
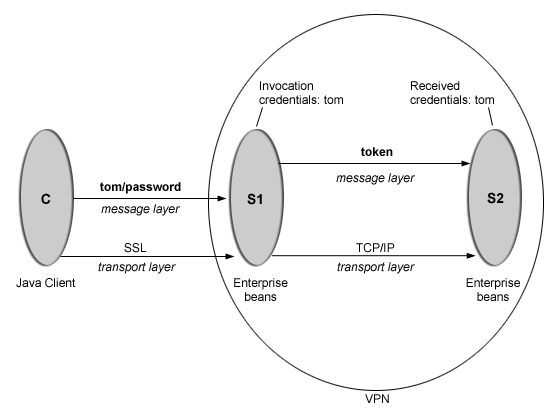
This scenario illustrates the ability to choose TCP/IP as the transport when it is appropriate. In some cases, when two servers are on the same VPN, it can be appropriate to select TCP/IP as the transport for performance reasons bacause the VPN already encrypts the message.
Step 1: Configure C
C1 requires message layer authentication with an SSL transport:
-
Identify the sas.client.props file to the client by specifying the property com.ibm.CORBA.ConfigURL=file:/QIBM/UserData/WebAS5/product/instance/properties/sas.client.props where product is Base or ND and instance is the name of your instance. All further configuration involves setting properties within this file.
-
Enable SSL. In this case, SSL is supported but not required:
com.ibm.CSI.performTransportAssocSSLTLSSupported=true
com.ibm.CSI.performTransportAssocSSLTLSRequired=false -
Enable client authentication at the message layer. In this case, client authentication is supported but not required:
com.ibm.CSI.performClientAuthenticationRequired=false
com.ibm.CSI.performClientAuthenticationSupported=true - Use the remaining defaults in the sas.client.props file.
Step 2: Configure S1
In the administrative console, S1 is configured for incoming requests to support message layer client authentication and incoming connections to support SSL without client certificate authentication. S1 is configured for outgoing requests to support identity assertion.
- Configure S1 for incoming connections:
- Disable identity assertion.
- Enable user ID and password authentication.
- Enable SSL.
- Disable SSL client certificate authentication.
- Configure S1 for outgoing connections:
- Disable identity assertion.
- Enable user ID and password authentication.
- Disable SSL.
Note: It is possible to enable SSL for inbound connections and disable SSL for outbound connections. The same is true in reverse.
Step 3: Configure S2
In the administrative console, S2 is configured for incoming requests to support identity assertion and to accept SSL connections. Configuration for outgoing requests and connections are not relevant for this scenario.
- Disable identity assertion.
- Enable user ID and password authentication.
- Disable SSL.