|
|
As shown in Figure 15-19, clustering software is used to provide highly available service IP addresses, resource groups, and fault-monitoring mechanisms.
Each node has a complete installation of the firewall software. Configure both nodes in such a way that the equal and interchangeable configurations on both nodes are assured.
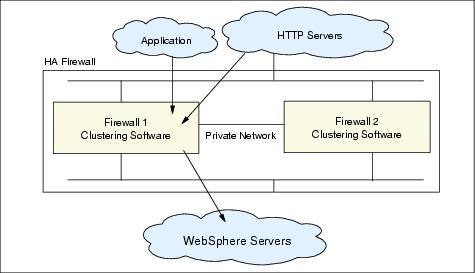
Figure 15-19 Clustered firewall for high availability
When the firewall process, network, or machine itself goes down, the clustering software will detect it and relocate the resource group, including the service IP address, to the backup node, then start the firewall service, as shown in Figure 15-20. The highly available firewall environment is reestablished after a failover. As soon as the primary firewall is up, the firewall service can automatically fall back to the primary node, or you can do this manually (this is determined by the clustering configuration settings).
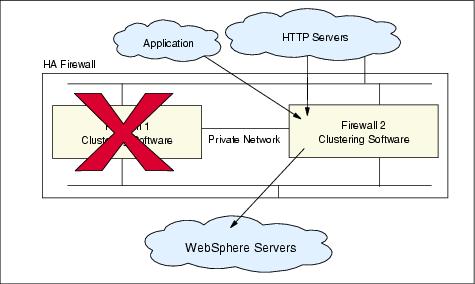
Figure 15-20 Clustered firewall after failover