Set up LDAP over SSL with Novell eDirectory
Overview
By default, user passwords are sent cleartext over the network between LDAP user registry and portal when...
- Portal user management tools are used to create users and change passwords
- WAS authenticates user name and password pairs through an LDAP bind operation.
We can configure WAS and portal to access to a Novell eDirectory LDAP user registry over SSL, and stymie anyone watching packets on the network.
Configuring LDAP over SSL for WAS and portal encrypts data between WAS and eDirectory servers. Other procedures are available for encrypting network packets between an HTTP server and Novell eDirectory servers.
First get LDAP (non-SSL) successfully working before setting up LDAP over SSL.
Procedure
- Install portal and WAS
Refer to Installing on Windows and UNIX for more information.
- Install and setup the LDAP
- Generate or import certificates as necessary and activate SSL on the directory
Cert can be either self-signed or CA certificate chain.
Refer to the Novell eDirectory documentation for more information.
- Import certificates to portal to enable SSL connection
Use ikeyman to import the certificate exported from the Novell certificate management process into the required Java Key Store (.jks)
- Run ikeyman...
cd was_profile_root/bin
./ikeyman.sh
- Open the Java Key Store file which will be used by WAS for LDAP over SSL.
We can create a new key file...
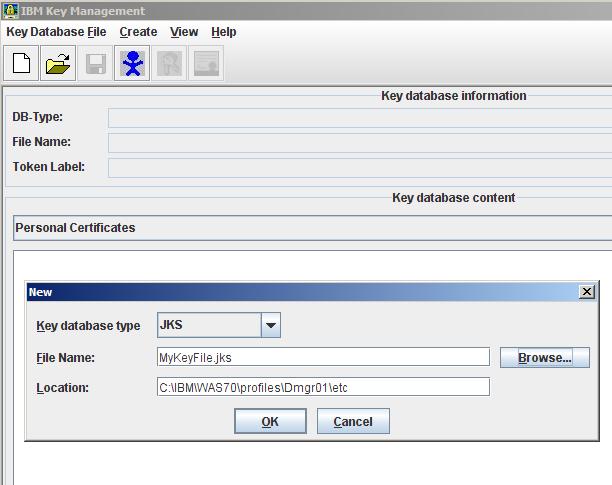
...or we can use the default *.jks file...
The password to the dummy server trust file is "WebAS".
- If you created a new key file, then define a new SSL repertoire.
If not, we can use the default repertoire, DefaultSSLSetting, which contains the default WAS server trust file.
- Select Signer Certificates from the top pull-down, then click Add.
- Select Base64-encoded ASCII data as the data type, and browse to the certificate file of that type that you exported from the Novell certificate management process.
- You will be asked for a label for the new certificate. Enter the same value that you specified for the label when you created the certificate.
- Save the updated key store file.
- Specify a key Java Key Store
Portal can be configured to use to a specifically named Java Key Store so that portal and WAS can share the same configured truststore in the SSL configuration of the CSIv2 Outbound Transport.
- Stop portal.
- Logon to the WAS Administration Console and navigate to the LDAP User Registry panel.
- Check the sslEnabled box and set the LDAP Port to port.
- Save changes.
- Cycle server1
- Edit...
- Navigate to the stanza that begins...
ldapRepository name="wmmLDAP"
- Verify that ldapPort="port" and sslEnabled="true".
- At the end of this stanza, set...
sslTrustStore="was_profile_root/etc/DummyServerTrustFile.jks"
If you do not specify an sslTrustStore parameter here, Member Manager will use
app_server_root/java/jre/lib/security/cacerts.jks
Import the Novell eDirectory root CA certificate into the specified cacerts key store.
- Save the file.
- Stop and restart the WebSphere Application Server (server1).
- Restart portal.
- Close down the non-SSL port of the LDAP user registry server (optional)
This is an optional step. Closing the non-SSL port of the directory will ensure that traffic exchanged with the directory by WebSphere Application Server, portal, or any other application, is confidential.
i5/OS notes
For i5/OS, If your application uses commercial certificate authority certificates (signer or CA certificates), you might be able to use the cacerts keystore (the default trust keystore) with the application. The integrated file system path for cacerts is /QIBM /ProdData/Java400/jdk14/lib/security/cacerts.
However, in no case should you attempt to modify the original cacerts keystore.
Create a private copy of the cacerts file, and then add or remove certificates to the private copy. The password for cacerts is changeit. Be sure to change the password that protects the private copy of the cacerts file. Also, note that initially, all keystores created using iKeyman contain a number of commercial CA certificates.
We can create the Java keystores in any iSeries integrated file system directory. However, it might be convenient to place them in the same directory as those that are used by the WebSphere profile. This might make it easier to include them in the backup and restore procedure. WAS provides an initial set of Java keystores that are used to secure connections between WebSphere components. These keystores are found in the etc directory of your WebSphere profile. For example, the keystores for the default profile are found in the app_server_root/etc directory.
For an example of how to create a Java keystore, see Using Java keystore files in the WAS for iSeries documentation.
You must also import the certificates to a keystore that can be used by the portal. In this case, portal has no configuration setting to point to a specifically named Java Key Store file.
Instead, import the certificates into the default keystore file of the JVM, cacerts. However, in no case should you attempt to modify thecacerts keystore. Rather, you should create a private copy of the cacerts file, and then add or remove certificates. The configured truststore in the SSL configuration of the CSIv2 Outbound Transport must also be updated.
Parent topic:
Setting up LDAP over SSL