CipherSpec mappings for the managed .NET client
The IBM MQ .NET interface maintains an IBM MQ to Microsoft.NET mapping table that is used to determine the version of the TLS protocol that the managed client needs to use to establish a secure connection with a queue manager.
If a CipherSpec is specified on the SVRCONN channel, then after the TLS handshake is complete, the queue manager tries to match that CipherSpec with the negotiated CipherSpec that the client application is using. If the queue manager cannot find a matching CipherSpec, the communication fails with error AMQ9631.
The IBM MQ.NET interface maintains an IBM MQ to Microsoft.NET CipherSpec mapping table. This table is used to determine the TLS protocol version that client wants to use to establish a secured socket connection with the queue manager. Based on the SSLCipherSpec value, the SSLProtocol version can be TLS 1.0, or TLS 1.2, depending on which version of the Microsoft.NET Framework we are using.
Make sure that you provide the correct the SSLCipherSpec value as specifying an incorrect value might result in SSL 3.0 or TLS 1.0 protocols being used.
| IBM MQ CipherSpec | Microsoft.NET CipherSpec | TLS version |
|---|---|---|
| TLS_RSA_WITH_AES_128_CBC_SHA | TLS_RSA_WITH_AES_128_CBC_SHA | TLS 1.0 |
| TLS_RSA_WITH_AES_256_CBC_SHA | TLS_RSA_WITH_AES_256_CBC_SHA | TLS 1.0 |
| TLS_RSA_WITH_3DES_EDE_CBC_SHA 1 | TLS_RSA_WITH_3DES_EDE_CBC_SHA 1 | TLS 1.0 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 | TLS_RSA_WITH_AES_128_CBC_SHA256 | TLS 1.2 |
| TLS_RSA_WITH_AES_256_CBC_SHA256 | TLS_RSA_WITH_AES_256_CBC_SHA256 | TLS 1.2 |
| ECDHE_RSA_AES_128_CBC_SHA256 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 | TLS 1.2 |
| ECDHE_RSA_AES_128_CBC_SHA256 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384 | TLS 1.2 |
| ECDHE_RSA_AES_128_CBC_SHA256 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_CBC_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_CBC_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_CBC_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521 | TLS 1.2 |
| ECDHE_ECDSA_AES_256_CBC_SHA384 | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384 | TLS 1.2 |
| ECDHE_ECDSA_AES_256_CBC_SHA384 | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521 | TLS 1.2 |
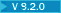 ECDHE_RSA_AES_128_GCM_SHA256 ECDHE_RSA_AES_128_GCM_SHA256 |
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 | TLS 1.2 |
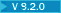 ECDHE_RSA_AES_256_GCM_SHA384 ECDHE_RSA_AES_256_GCM_SHA384 |
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_GCM_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_GCM_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 | TLS 1.2 |
| ECDHE_ECDSA_AES_128_GCM_SHA256 | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 | TLS 1.2 |
| ECDHE_ECDSA_AES_256_GCM_SHA384 | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 | TLS 1.2 |
| ECDHE_ECDSA_AES_256_GCM_SHA384 | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 | TLS 1.2 |
- This CipherSpec TLS_RSA_WITH_3DES_EDE_CBC_SHA is deprecated. However, it can still be used to transfer up to 32 GB of data before the connection is terminated with error AMQ9288. To avoid this error, we need to either avoid using triple DES, or enable secret key reset when using this CipherSpec.
Parent topic: TLS support for the managed .NET client