IBM BPM, V8.0.1, All platforms > Securing IBM BPM and applications > Securing access to timetables in the Business Calendars widget
Roles associated with a timetable
When a timetable is installed, three roles are created for that timetable–Owner, Writer, and Reader. These roles are known as component-specific roles.
How would these roles be used? Consider the case of a holiday timetable used in an organization. You want all employees to have access to the timetable, but you want to limit the number of employees who can update the timetable.
When the Holiday timetable is installed, the following roles are created:
- HolidayOwner
Members assigned to this role can read the Holiday timetable and can also write to it.
For example, if the company decided to add an extra holiday, a member with the HolidayOwner role would be able to make the change.
Members of this role can also assign members to the HolidayWriter and HolidayReader role.
For example, the HolidayOwner might decide to add a senior manager to the HolidayWriter role.
- HolidayWriter
Members assigned to this role can read the Holiday timetable and can also write to it. As in the case of the HolidayOwner, members of the HolidayWriter role could add the extra holiday.
- HolidayReader
Members assigned to this role can read the Holiday timetable but cannot write to it.
You might assign the HolidayOwner role to the Human Resources manager, the HolidayWriter role to the Human Resources Specialists group, and the HolidayReader role to the employee group, as shown in the following figure:
Figure 1. Example of roles assigned to a timetable
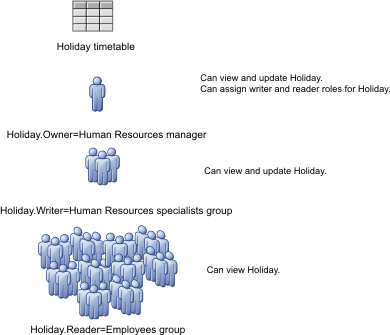
When you deploy a timetable, the three roles–Owner, Writer, and Reader–are created. Permission for all roles is set initially to All Authenticated. Verify that you change this designation to assign the members of the organization to the correct roles.
You can change the membership of a role (for example, you can remove a member from the reader role), but you cannot change the name of a role, add or delete a role, or change the permissions associated with a role. The permissions are set as follows:
- Members of the Owner role can read and write to the timetable and can assign other members to the Writer and Reader roles.
- Members of the Writer role can read and write to the timetable.
- Members of the Reader role can read the timetable.
In the Security Roles widget, these timetable-related roles are also known as module roles.
Securing access to timetables in the Business Calendars widget