WebSphere eXtreme Scale Programming Guide >
|
| |
Security API
WebSphere eXtreme Scale adopts an open security architecture. It provides a basic security framework for authentication, authorization, and transport security, and requires users to implement plug-ins to complete the security infrastructure.
The following image shows the basic flow of client authentication and authorization for an eXtreme Scale server.
Figure 1. Flow of client authentication and authorization
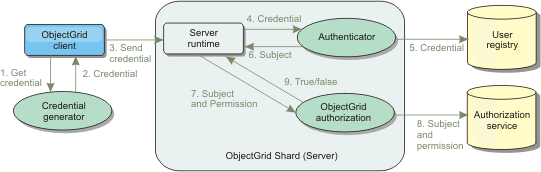
The authentication flow and authorization flow are as follows.
Authentication flow
- The authentication flow starts with an eXtreme Scale client getting a credential. This is done by the com.ibm.websphere.objectgrid.security.plugins.CredentialGenerator plug-in.
- A CredentialGenerator object knows how to generate a valid client credential, for example, a user ID and password pair, Kerberos ticket, and so on. This generated credential is sent back to the client.
- After the client retrieves the Credential object using the CredentialGenerator object, this Credential object is sent along with the eXtreme Scale request to the eXtreme Scale server.
- The eXtreme Scale server authenticates the Credential object before processing the eXtreme Scale request. Then the server uses the Authenticator plug-in to authenticate the Credential object.
- The Authenticator plug-in represents an interface to the user registry, for example, a Lightweight Directory Access Protocol (LDAP) server or an operating system user registry. The Authenticator consults the user registry and makes authentication decisions.
- If the authentication is successful, a Subject object is returned to represent this client.
Authorization flowWebSphere eXtreme Scale adopts a permission-based authorization mechanism, and has different permission categories represented by different permission classes. For example, a com.ibm.websphere.objectgrid.security.MapPermission object represents permissions to read, write, insert, invalidate, and remove the data entries in an ObjectMap. Because WebSphere eXtreme Scale supports Java™ Authentication and Authorization Service (JAAS) authorization out-of-box, you can use JAAS to handle authorization by providing authorization policies.
Also, eXtreme Scale supports custom authorizations. Custom authorizations are plugged in by the plug-in com.ibm.websphere.objectgrid.security.plugins.ObjectGridAuthorization. The flow of the customer authorization is as follows.
- The server runtime sends the Subject object and the required permission to the authorization plug-in.
- The authorization plug-in consults the Authorization service and makes an authorization decision. If permission is granted for this Subject object, a value of true is returned, otherwise falseis returned.
- This authorization decision, true or false, is returned to the server runtime.
Security implementation
The topics in this section discuss how to program a secure WebSphere eXtreme Scale deployment and how to program the plug-in implementations. The section is organized based on the various security features. In each subtopic, we will learn about relevant plug-ins and how to implement the plug-ins. In the authentication section, we will see how to connect to a secure WebSphere eXtreme Scale deployment environment.
Client Authentication: The client authentication topic describes how a WebSphere eXtreme Scale client gets a credential and how a server authenticates the client. It will also discuss how a WebSphere eXtreme Scale client connects to a secure WebSphere eXtreme Scale server.
Authorization: The authorization topic explains how to use the ObjectGridAuthorization to do customer authorization besides JAAS authorization.
Grid Authentication: The grid authentication topic discusses how you can use SecureTokenManager to securely transport server secrets.
Java Management Extensions (JMX) programming: When the WebSphere eXtreme Scale server is secured, the JMX client might need to send a JMX credential to the server.
- Client authentication programming
For authentication, WebSphere eXtreme Scale provides a runtime to send the credential from the client to the server side, and then calls the authenticator plug-in to authenticate the users. - Client authorization programming
WebSphere eXtreme Scale supports Java Authentication and Authorization Service (JAAS) authorization out-of-the-box and also supports custom Authorization using the ObjectGridAuthorization interface. - Grid authentication
You can use the secure token manager plug-in to enable server-to-server authentication, which requires you to implement the SecureTokenManager interface. - Local security
WebSphere eXtreme Scale provides several security endpoints to allow you to integrate custom mechanisms. In the local programming model, the main security function is authorization, and has no authentication support . You must authenticate outside of WebSphere Application Server. However, there are provided plug-ins to obtain and validate Subject objects.