Scenario 2: Virtual host junctions with interfaces
Learn how to set up virtual host junctions on separate WebSEAL interfaces and two junctions configured to share a common protected object space.
The following scenario sets up:
- Virtual host junctions are created on separate WebSEAL interfaces.
- Two junctions are configured to share a common protected object space.
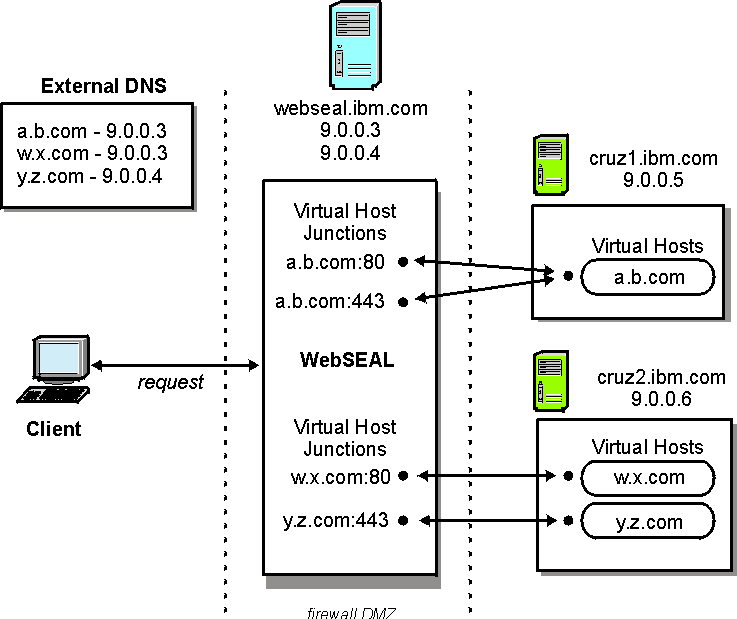
Refer to the accompanying diagram as you proceed through the steps.
Required architecture:
- WebSEAL protects three virtual hosts over the following protocols:
- a.b.com (on host cruz1.ibm.com) over HTTP and HTTPS
- w.x.com (on host cruz2.ibm.com) over HTTP
- y.z.com (on host cruz2.ibm.com) over HTTPS
- Direct access to the protected junctioned servers (cruz1.ibm.com > cruz2.ibm.com) is prevented by appropriate firewall protection. The user is not aware of this blocked access. The external DNS entries used by the browser to look up the virtual host names are configured to point to WebSEAL at IP address 9.0.0.3 or 9.0.0.4.
- The virtual hosts are configured in the external DNS to point
to the WebSEAL server:
External DNS a.b.com 9.0.0.3 x.y.com 9.0.0.3 y.z.com 9.0.0.4 - The WebSEAL server is known to browsers by the following host
names:
- webseal.ibm.com (WebSEAL's true host name)
- a.b.com
- w.x.com
- y.z.com
- WebSEAL is configured for two interfaces (to allow serving unique
server-side certificates over HTTPS for a.b.com > y.z.com):
- 9.0.0.3
- 9.0.0.4
Procedure - general setup:
- Install and configure a default WebSEAL with the first of the two required interfaces (to support SSL communication with a.b.com:443):
[server] network-interface = 9.0.0.3 http = yes http-port = 80 https = yes https-port = 443
- To support SSL communication between browsers and the a.b.com virtual
host (over port 443), install a server-side certificate (named ab in this
example) in WebSEAL's pdsrv.kdb key file database. This certificate must be
generated and signed by a Certificate Authority (CA). WebSEAL presents this certificate, on behalf
of the interface, to authenticate to client browsers.
[ssl] webseal-cert-keyfile-label = ab
WebSEAL provides an option to configure a separate certificate key database for junction SSL operations. We can use a separate certificate key database rather than sharing the one used for client certificates specified in the [ssl] stanza. For information, see Configuration of the WebSEAL key database file and the description of the jct-cert-keyfile option in jct-cert-keyfile.
- Configure a second interface to support SSL communication with y.z.com:443: sssssssssssssssss ssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssssss ss>
- To support SSL communication between browsers and the y.z.com virtual host (over port 443), install a server-side certificate (named yz in this example) in WebSEAL's pdsrv.kdb key file database. This certificate must be generated and signed by a Certificate Authority (CA). WebSEAL presents this certificate, on behalf of the interface, to authenticate to client browsers. WebSEAL provides an option to configure a separate certificate key database for junction SSL operations. We can use a separate certificate key database rather than sharing the one used for client certificates specified in the [ssl] stanza. For information, see Configuration of the WebSEAL key database file and the description of the jct-cert-keyfile option in the jct-cert-keyfile.
- Assign the appropriate name as a value to the web-host-name stanza entry in
the WebSEAL configuration file. We must assign the appropriate name value to ensure that the primary WebSEAL host name is used when required.
[server] server-name = webseal.ibm.com-default web-host-name = webseal.ibm.com
Procedure - create virtual host junctions:
- Create two virtual host junctionsto support HTTP and HTTPS communication to a.b.com. Use the -g option to allow the two junctions to share the object space:
- pdadmin> server task default-webseald-webseal.ibm.com virtualhost create -t tcp -h cruz1.ibm.com -v a.b.com vhost-ab-tcp pdadmin> server task default-webseald-webseal.ibm.com virtualhost create -t ssl -h cruz1.ibm.com -v a.b.com -g vhost-ab-tcp vhost-ab-ssl
- Create a virtual host junctionto support
communication with w.x.com:80:
- pdadmin> server task default-webseald-webseal.ibm.com virtualhost create -t tcp -h cruz2.ibm.com -v w.x.com vhost-wx-tcp
- Create a virtual host junction to support communication with y.z.com:443:
- pdadmin> server task default-webseald-webseal.ibm.com virtualhost create -t ssl -h cruz2.ibm.com -v y.z.com vhost-yz-ssl
Parent topic: Virtual Hosting