Overview of the switch user function
The WebSEAL switch user function allows administrators to assume the identity of a user who is a member of the ISAM secure domain. The ability to assume a user's identity can help an administrator in a Help Desk environment to troubleshoot and diagnose problems. Switch user can also be used to test a user's access to resources and to perform application integration testing.
The switch user implementation is similar to the su command in UNIX environments. In the WebSEAL environment, the administrator acquires the user's credentials and interacts with resources and back-end applications with exactly the same abilities as the actual user.
The administrator uses a special HTML form to supply switch user information. WebSEAL processes the form and calls a special authentication mechanism that returns the specified user's credential without the requirement of knowing the user's password.
The following sequence describes the switch user process flow:
- An
administrator authenticates to WebSEAL. WebSEAL establishes a session
for the administrator, and creates an entry for the administrator
in the WebSEAL session cache.
The session cache entry contains a cache data structure. This data structure stores the administrator's credential. During the switch user process flow, the cache data will be manipulated.
For information on WebSEAL session caches, see WebSEAL session cache structure.
- The administrator requests a pre-configured switch user HTML form,
and completes the form. On the form, the administrator specifies:
- The name of the user identity the administrator needs to assume.
- A destination URL.
- An authentication method.
This action results in a POST request being sent to /pkmssu.form.
The contents of the switch user HTML form can be modified before making it available for use by WebSEAL. See Configure the switch user HTML form.
You can also extend the capabilities of the form. See Designing additional input forms. The pkmssu.form management page is a management command to the WebSEAL server. It is not represented in the object space and we cannot attach policies to it.
- WebSEAL determines whether to allow the switch user request by
performing the following checks:
- WebSEAL examines the membership of the ISAM su-admins group
to determine if the administrator has permission to invoke the switch
user function.
Administrators requesting use of switch user authentication must be members of the su-admins group. Membership in this group must be configured before switch user can be used. For information, see Configure user access.
- WebSEAL examines the membership of the ISAM su-admins > securitygroup > su-excluded groups to ensure
the user identity supplied in the switch user form is not a member
of one of these groups.
User identities that belong to any of these groups cannot be accessed by the switch user function. The WebSEAL administrator must configure memberships in these groups before administrators use the switch user function. For configuration instructions and more information on these groups, see Configure user access
- WebSEAL examines the membership of the ISAM su-admins group
to determine if the administrator has permission to invoke the switch
user function.
- When WebSEAL decides to allow the switch user
request, WebSEAL calls the appropriate switch user module to perform
the special switch user authentication.
WebSEAL supports a variety of authentication mechanisms. Each authentication mechanism has a corresponding switch user authentication mechanism. WebSEAL provides built-in modules that contain the special switch user function.
- When authentication of the designated user succeeds, the switch user module returns a valid credential for the user—without requiring the user password for input.
- WebSEAL manipulates the contents of the appropriate entry in the WebSEAL session cache by:
- Remove the administrator's WebSEAL session cache data and storing it in a separate location.
- Inserting the switched-to user's cache data, including the user's credential, in place of the administrator's cache data.
Figure 1. Swapping administrator and user cache data during switch user 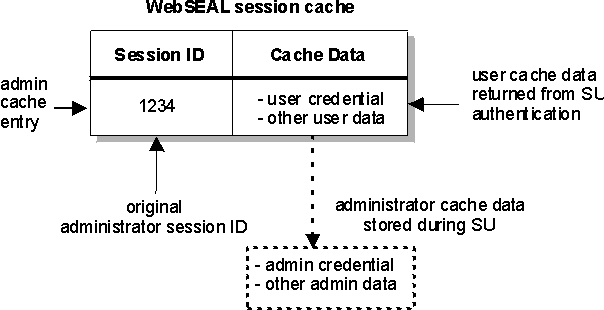
- WebSEAL sends a redirect to the browser for the destination URL
supplied in the switch user form.
The request is processed normally, using the user's credential.
- The administrator can continue to make other requests. All authorization
decisions for these requests are based on the credential of the user.
When using switch user functionality, administrators might need to establish and manage sessions with additional applications. These sessions need to be established using the identity of the new user. To enable this, the new user credential also contains a new User Session ID. This User Session ID is used, for example, when troubleshooting the user's ability to access and use additional Web resources.
For more information on WebSEAL session caches, see WebSEAL session cache configuration and WebSEAL session cache structure.
- The administrator ends the switch user session using the standard Security Verify Access /pkmslogout utility.
Upon successful log out:
- The user's cache data is deleted.
- The administrator's original cache data (and credential) is restored.
- The administrator is returned to the original page from which the switch user form was requested.
The authorization service uses the original credential of the administrator for all subsequent requests.
Parent topic: Switch user authentication