Client identity and generic password
As an administrator, we must know how client identity and passwords are handled so that we understand how WebSEAL manages authentication in some scenarios.
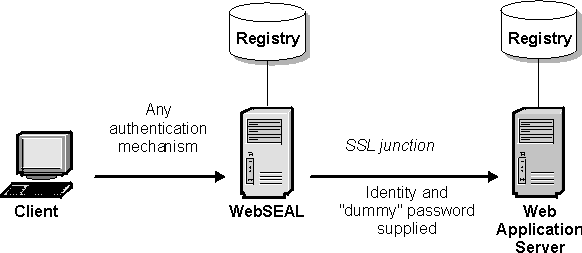
The -b supply option instructs WebSEAL to supply the authenticated Security Verify Access user name (client's original identity) with a static, generic (dummy) password. The original client password is not used in this scenario. A generic password eliminates password administration and supports the application on a per-user basis. The dummy password is set in the basicauth-dummy-passwd stanza entry of the WebSEAL configuration file:
[junction] basicauth-dummy-passwd = password
This scenario assumes the back-end server requires authentication from an ISAM identity. By mapping a client user to a known Security Verify Access user, WebSEAL manages authentication for the back-end server and provides a simple domain-wide single signon solution.
The following conditions exist for this solution:
- WebSEAL is configured to supply the back-end server with the user name contained in the original client request plus a generic dummy password.
- The dummy password is configured in the WebSEAL configuration file.
- The back-end server registry must recognize the ISAM identity that is supplied in the HTTP BA header.
- Because sensitive authentication information (user name and password) is passed across the junction, the security of the junction is important. Therefore, an SSL junction is appropriate.
Parent topic: Single Sign-on Solutions