Single sign-on using Kerberos constrained delegation
We can set up constrained delegation by allowing WebSEAL to request a Windows Kerberos ticket on behalf of the client from the key distribution centre (KDC). The ticket can then be used by WebSEAL to impersonate the client to authenticate with the junctioned Web server.
Two extensions are involved in this process: Service-for-User-to-Self (S4U2Self)
and Service-for-User-to-Proxy (S4U2Proxy). S4U2Self allows
a service to acquire a ticket from the KDC on behalf of a client. S4U2Proxy allows
a service to use the ticket obtained through S4U2Self to acquire another ticket to an external service.
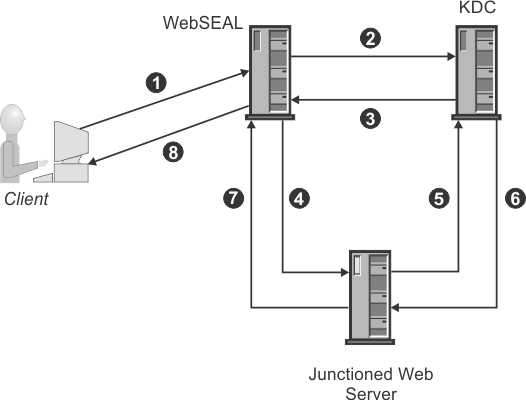
The diagram above shows a sample deployment of single sign-on using Kerberos constrained delegation.
- Client uses the standard Security Verify Access authentication process to authenticate to WebSEAL over HTTPS or HTTP and requests an object on the junctioned server. WebSEAL authorizes the request from the client, and determines that a Kerberos ticket is needed to access the junctioned application.
- WebSEAL requests a Windows Kerberos ticket on behalf of the client from the key distribution centre (KDC).
- KDC issues the Kerberos ticket to WebSEAL.
- The WebSEAL server forwards the Kerberos ticket along with the client request to the junctioned Web server over either HTTP or HTTPS.
- The junctioned Web server requests validation of the Kerberos ticket from the KDC.
- The KDC verifies the Kerberos ticket is valid.
- The junctioned Web server returns an HTTP response to WebSEAL.
- WebSEAL returns the HTTP response to the client.
To allow WebSEAL to perform Kerberos single sign-on for a junction, ensure that:
- Service users are created in Active Directory.
- The Kerberos Configuration and WebSEAL configuration file are updated on the appliance.
- The WebSEAL junction is created.
Kerberos tickets rely on embedded time stamps to decide the expiration of old tickets. For this reason, it is important to ensure the clocks on all machines in the environment are synchronized.
- Create the WebSEAL user in Active Directory
In order for constrained delegation to operate correctly, WebSEAL and the target service must be running as Active Directory (AD) users that have an assigned Service Principal Name (SPN). - WebSEAL Kerberos configuration
Complete the Kerberos configuration on the appliance so that single sign-on with Kerberos constrained delegation can work. - Configure WebSEAL to enable Kerberos single sign-on
To enable Kerberos single sign-on for a junction, set the value of the kerberos-sso-enable entry in the [junction] stanza to yes.
Parent topic: Single Sign-on Solutions