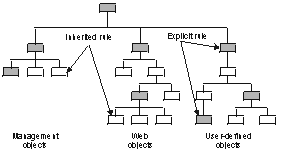
Explicit and inherited policies
A security policy can be explicitly applied or inherited. The administrator can apply explicit policies only at points in the hierarchy where the rules must change. The Security Verify Access protected object space supports inheritance of ACLs, POPs, and authorization rules. This factor is an important consideration for the security administrator who manages the object space. The administrator needs to apply explicit policies only at points in the hierarchy where the rules must change.
- Hardcoded rules
- External authorization capability
- Special secure labeling
- Access control lists (ACLs), protected object policies (POPs), and authorization rules
Parent topic: Define and apply security policy