ACL policy inheritance example
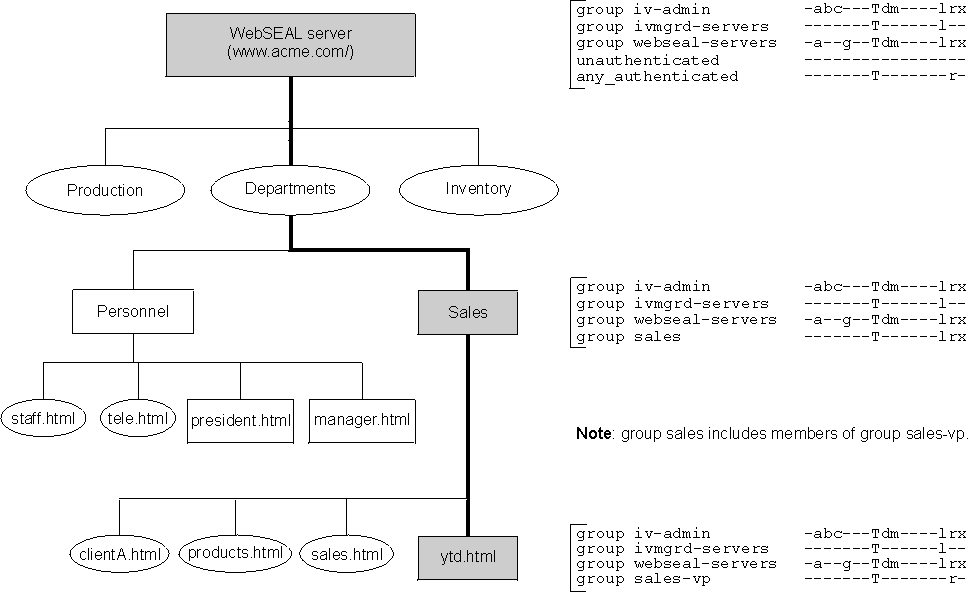
This example illustrates the impact of a mixture of inherited and explicit ACL policies in the fictional ACME corporate object space.
A corporate object space has a general security policy set at the root object. Root is followed by the /WebSEAL container object and individually controlled departmental subtrees.
In this example, the sales group is given ownership of its departmental subtree. The ACL policy on this subtree no longer acknowledges the unauthenticated or any-other entry types. The ytd.html file has an attached ACL policy that grants read permission to members of the sales-vp group (who are also members of the sales group). This ACL policy scheme does not need to be changed when users are added to or removed from the domain. Users can be added to or removed from the existing groups.
Parent topic: Sparse security policy model