Deployment pattern
Read this section to understand the components of a typical cluster environment and how to set up such environments. In this typical deployment scenario, the cluster incorporates both an ISAM base appliance and an appliance with Advanced Access Control activated.
The following diagram illustrates a sample cluster
environment.
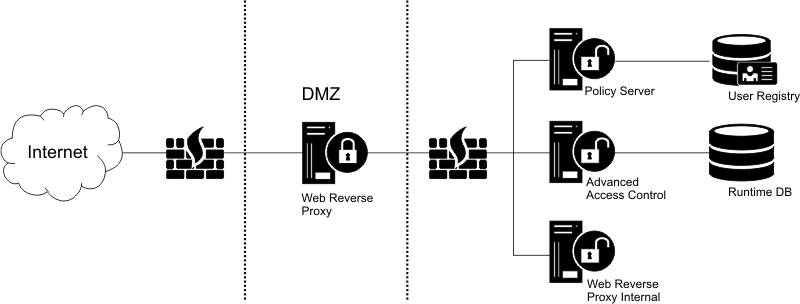
This environment consists of the following components:
- An external user registry, which can be a federated registry.
- Numerous appliances, namely:
- A policy server
- One or more appliances that provide the Advanced Access Control runtime service
- Potentially an internal web reverse proxy to handle corporate traffic
- One or more web reverse proxies in the DMZ to handle public traffic
In this scenario, all of the appliances reside in the same appliance cluster, with the policy server running on the primary master. Any of the other appliances that are running in the trusted zone can be enrolled as the secondary master, or we can have a dedicated secondary master appliance. The tertiary and quaternary masters are only required if we are using the distributed session cache across multiple data centers.
It is advisable to enroll the appliances that reside in the DMZ as restricted nodes. A restricted node imposes extra security constraints on the appliance, namely we cannot modify the security policy on these appliances or promote any of these appliances to a master.
In this environment, it is preferable to enable the replication of the ISAM runtime environment and SSL certificate key files. For instructions on how to enable such settings, see Manage cluster configuration. The replication of the ISAM runtime environment has the following advantages:
- You no longer need to configure the runtime environment manually on any node in the environment. The configuration information is automatically obtained from the primary master.
- If the primary master becomes unavailable (for example, due to hardware failure), we can promote one of the other unrestricted nodes to become a primary master and we do not lose the policy database. Nodes within the cluster are also automatically notified of the new policy server.
The following steps describe the recommended way in which to set up the environment:
- Install each of the appliances. You should also:
- Configure the networking.
- Activate the required offerings. The primary master must be activated with each offering that you will be using in the environment (for example, in this environment the primary master would be activated with both Security Verify Access base and Advanced Access Control).
- Change the cluster configuration on the policy server to make it the primary master of a multi-node cluster.
- On the primary master, configure the ISAM runtime environment, including the policy server.
- Enable the cluster replication of the runtime environment and certificate database.
- Join each appliance to the cluster, one at a time. Join any appliances that reside in the DMZ as a restricted node.
- Change the cluster configuration on the primary master to promote one of the unrestricted nodes to the role of secondary master. The node being promoted to secondary master must also be activated with each of the offerings used in the environment.
- Configure the ISAM base and Advanced Access Control security policies.
- Configure the web reverse proxy instances on each of your Security Verify Access nodes.
Parent topic: Cluster support