Resources
WebSphere Portal resources are organized in a hierarchy. Resources in the hierarchy propagate their access control configuration to all of their child resources. For example, if a user has the Editor role on the Market News Page, then by default that user also has the Editor role on all pages that are children of the Market News Page.
Resource instances are specific resources, such as a single portlet or page. Each resource instance belongs to only one resource type. For example, the resource instance Market News Page would belong to the Pages resource type. Virtual resources are a unique resource type. Virtual resources have two functions:
- They protect sensitive operations that affect the entire portal or specific concepts in the portal. For example, the XML configuration interface virtual resource protects the ability to execute scripts through that XML configuration interface.
- They are parent resources for all resource instances. For example, the Web Modules virtual resource is the root node of all Web modules instances within the portal. Role assignments on the Web Modules virtual resource permit access to all Web modules in the portal.
In the following illustration, blank squares indicate resource instances and labeled rectangles indicate virtual resources.
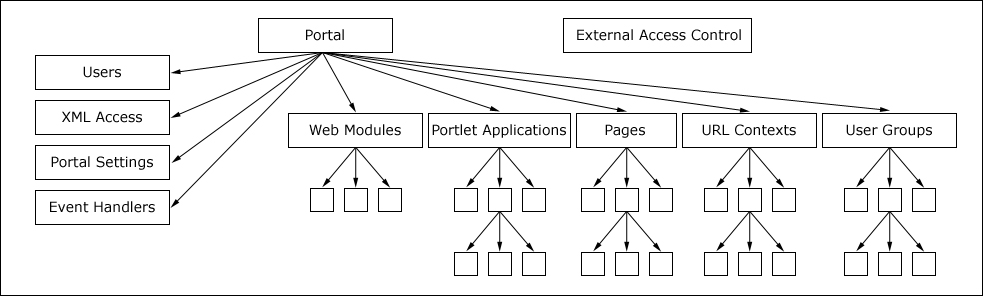
You can assign roles on virtual resources and on resource instances. Assigning roles on virtual resources reduces the time needed to administer access control because all child resources inherit roles that are assigned to the parent resource by default. Assigning roles to specific resource instances offers more granular access control. You might need to assign roles to specific resource instances to override role blocks that block inheritance. For more information about role blocks, see the Roles topic.
The following table describes virtual resources.
| Virtual Resource | Description |
|---|---|
| Portal | This is the root node of all resources. Roles on this resource affect all other resources by default. Role blocks can be inserted to prevent this inheritance. The administrative user identified during portal installation is initially assigned the role Administrator@Portal. Role blocks do not affect the Administrator@Portal and Security Administrator@Portal roles. |
| Web Modules | The root node of all Web modules. Web modules are portlet WAR files that are installed on WAS. Web modules can contain multiple portlet applications. If a new Web module is installed, it is automatically a child of the Web Modules virtual resource. Roles on this resource affect all child resources (all installed Web modules) unless role blocks are used. |
| Portlet Applications | The root node of all installed portlet applications. Portlet applications are the parent containers for portlets. If a new Web module is installed, the portlet applications that are contained within that Web module are automatically child resources of the Portlet Applications virtual resource. Portlets that are contained within a portlet application appear as child nodes of that portlet application. A two-layer hierarchy consisting of portlet applications and the corresponding portlets exists beneath the Portlet Applications virtual resource. Portlets inherit access control configuration from their parent portlet applications unless role blocks are used. |
| Pages | The root node of all pages, labels, and external URLs. Pages contain the content that determines the portal navigation hierarchy. If a new top-level page is created, it is automatically a child resource of the Pages virtual resource. If a new page is created beneath an existing page, the new page is automatically child of the existing page. Pages inherit access control configuration from their parent page unless role blocks are used. |
| URL Mapping Contexts | The root node of all URL mapping contexts. URL mapping contexts are user-defined definitions of URL spaces that map to portal content. If a new top-level URL mapping context is created, it is automatically a child resource of the URL Mapping Contexts virtual resource. If a new URL mapping context is created beneath an existing context, the new context is automatically a child of the existing context. URL mapping contexts inherit access control configuration from their parent context unless role blocks are used. |
| User Groups | The root node of all user groups. Role blocks cannot be created for user groups. Each user group in the portal inherits its access control configuration from the User Groups virtual resource. |
| Users | This virtual resource has no child resources. The Users virtual resource protects sensitive operations that deal with user management. For example, in order to add a user to a user group, have the Security Administrator@Users role. Users are implicitly protected resources. Users cannot be protected individually, but only through their group membership. As a result, it is not possible to have a role assignment on a specific user. Roles must be on user groups instead. So, you can edit Mary's user profile if you have a role assignment on some user group to which Mary belongs. |
| Virtual Users and User Groups | Predefined virtual users and groups permit access control
configuration that applies to abstract sets of users. These virtual users and groups
are not stored in the user registry. You cannot change group membership or other attributes of these virtual users and groups.
|
| XML configuration interface | Protects the ability to execute XML configuration interface scripts. This virtual resource has no child resources. |
| Portal Settings | Protects portal settings that can be modified through the Portal Settings Portlet or the XML configuration interface. This virtual resource has no child resources. |
| Event Handlers | Protects management of Event Handlers. This virtual resource has no child resources. |
| External Access Control | Protects access control configuration for resources that are controlled externally by a security manager such as Tivoli Access Manager. Also protects the ability to externalize a resource. |
| Markups | Protects the ability to control all markups for the portal. Assigning on an individual markup, such as HTML, is not possible. This virtual resource has no child resources. |
See also