Reverse proxy (IP forwarding) sample topology
Reverse proxy and IP-forwarding topologies use a reverse proxy server, such as the one in WebSphere Application Server Edge Components, to receive incoming HTTP requests and forward them to a Web server. The reverse proxy server is hosted on a separate machine or logical partition. This topology requires WebSphere Application Server or WebSphere Application Server Network Deployment.
This figure shows an example of a reverse proxy topology:
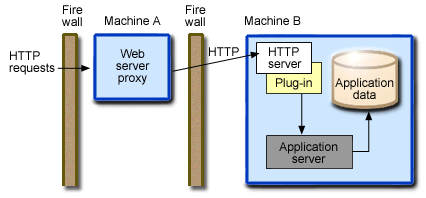
In this sample topology, a reverse proxy resides in a demilitarized zone (DMZ) between the outer and inner firewalls. The reverse proxy then forwards client HTTP requests to an HTTP server that resides on the application server machine. The Web server forwards the requests to the application servers. When the reverse proxy server returns completed requests to the client, it conceals the originating Web server.
Reverse proxy servers are typically used in DMZ configurations to provide additional security between the Internet and the Web servers and application servers that process requests.
Reverse proxy configurations support high-performance DMZ solutions that require as few open ports in the firewall as possible. The reverse proxy capabilities of the Web server inside the DMZ require as few as one open port in the outer firewall. If you use HTTP and HTTPS, you need two open ports.
Advantages and disadvantages of reverse proxy topology
These are some of the advantages of using a reverse proxy server in a DMZ configuration:
- Does not require database access through the firewall.
- Supports WebSphere Application Server security and NAT firewalls.
- Supports Secure Sockets Layer (SSL) encryption for communications between the Web server and the application server.
- Eliminates protocol switching because it uses the HTTP protocol for all forwarded requests.
- Is reliable and performance is relatively fast.
- Does not affect the configuration and maintenance of a WebSphere Application Server application.
- Can recieve and respond to all client requests through a single firewall port.
- Is usually less confusing than other DMZ configurations because the basic reverse proxy configuration is well-known and tested in the industry.
Some of the disadvantages of using a reverse proxy server in a DMZ configuration are listed below:
- May not be suitable for some environments.
- Requires more hardware and software than similar topologies that do not include a reverse proxy server. As a result, this topology can be more costly and more complicated to configure and maintain.
- Does not participate in WebSphere Application Server workload management.
- Uses only one firewall port, which is a disadvantage in environments where security policies require that separate ports be used for inbound and outbound traffic across a firewall.
Configure a reverse proxy topology
Configuration of the reverse proxy server varies depending on the reverse proxy product you choose. Refer to the documentation for the product. A reverse proxy server requires no additional WebSphere Application Server administration, although you may need to administer other elements of the reverse proxy topology.
Note: To use a reverse proxy configuration with WebSphere Application Server, use a reverse proxy product that supports Network Address Translation (NAT) and WebSphere Application Server security.