Firewalls and demilitarized zone (DMZ) configurations
Firewalls are often used in multi-tiered configuations to protect back-end resources, such as databases. Using firewalls can also protect application servers and Web servers from unauthorized outside access.
A demilitarized zone (DMZ) configuration involves multiple firewalls that add layers of security between the Internet and a company's critical data and business logic. A wide variety of topologies are appropriate for a DMZ environment.
A typical DMZ configuration includes the following components:
-
An outer firewall that is configured between the public Internet and the Web server that hosts the company Web site.
-
An inner firewall that is configured between the Web server and one or more application servers that reside with the corporate intranet. Company data resides behind the inner firewall.
This figure illustrates a typical DMZ configuration:
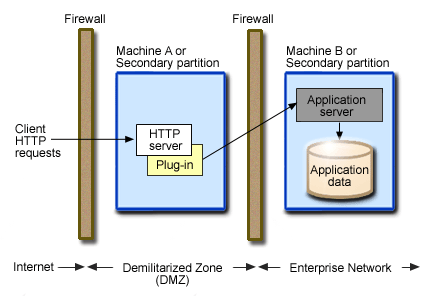
The area between the two firewalls (where the Web server resides) gives the DMZ configuration its name.
HTTP server separation topologies differ in the advantages they provide in a DMZ configuration.
- HTTP server transport topology (Remote HTTP)
- Supports WebSphere Application Server security and Network Address Translation (NAT).
- Does not require database access through the firewall.
- Supports encrypted communication between the HTTP server and the application server.
- Avoids single point of failure.
- Remote proxy topology
- Supports WebSphere Application Server security and NAT.
- Does not require database access through the firewall.
- Avoids DMZ protocol switching.
- Some reverse proxy products support encrypted communication between the HTTP server and the application server.
- Requires only 1 open port in the firewall.
WebSphere Application Server port usage provides a list of the ports that WebSphere Application Server uses. Use this information to help you configure your firewalls.