Demilitarized zone sample topology
In a demilitarized zone (DMZ) configuration, multiple firewalls add layers of security between the Internet and a company's critical data and business logic. This topology requires WebSphere Application Server or WebSphere Application Server Network Deployment.
This figure shows an example of a DMZ topology:
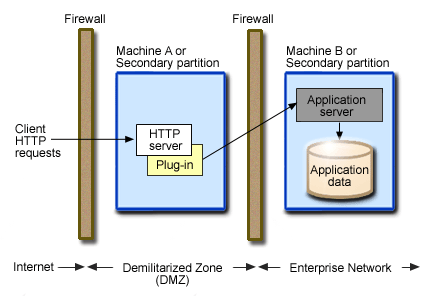
In this example topology, machine A hosts the Web server, which is separated from the Internet by the outer firewall. The inner firewall separates the Web server from the application servers and data. These two firewalls are required to create the demilitarized zone. You can also create additional firewalls to provide additional security for the application databases.
You do not need multiple machines to implement a DMZ configuration. Use logical partitioning (LPAR) to configure two or more secondary partitions on a single machine. Configure firewalls to isolate the partition that hosts the Web server, and create one or more additional partitions to host the application server and database.
The primary disadvantage of DMZ topologies is that they are complex to administer and maintain.