Security of your Operations Console configuration
Operations Console security consists of service device authentication, user authentication, data privacy, and data integrity.
An Operations Console local console directly attached to the server has implicit device authentication, data privacy, and data integrity because of its point-to-point connection. User authentication security is required to sign on to the console display.
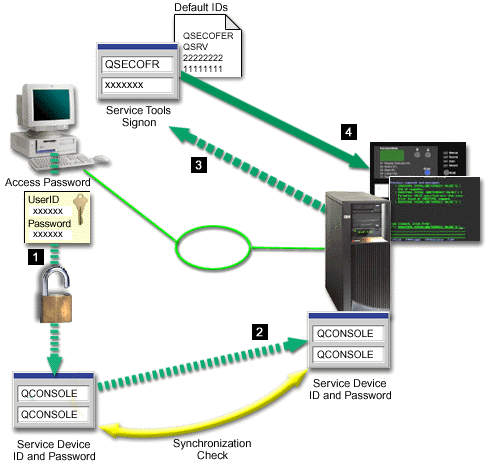
The following list gives you an overview of your Operations Console LAN security as shown in Figure 1.
- A user enters the correct password.
- Operations Console sends the service tools device ID (QCONSOLE) and its encrypted password to the system.
- The system checks the two values. If they match, the system updates both the device and DST with a newly encrypted password.
- The connection process then validates the service tools user ID and password before sending the system console display to the PC.
The System i™ console security consists of:
- Service device authentication
- This security assures one physical device is the console. Operations Console local console directly attached to the server is a physical connection similar to a twinaxial console. The serial cable you use for Operations Console using a direct connection may be physically secured similar to a twinaxial connection to control access to the physical console device. Operations Console local console on a network uses a version of Secured Sockets Layer (SSL) that supports device and user authentication, but without using certificates.
- Device authentication
- The device authentication is based on a service tools device ID. Service tools device IDs are administered in the dedicated service tools (DST) and system service tools (SST). They consist of a service tools device ID and a service tools device ID password. The default service tools device ID is QCONSOLE and the default password is QCONSOLE. An Operations Console local console on a network encrypts and changes the password during each successful connection. You must use the default password to initially set up your system if you use a local console on a network (LAN).
The device authentication requires a unique service tools device ID for each PC that is configured with a local console on a network (LAN) connection.
When using an Operations Console local console on a network, the configuration wizard adds the necessary information to the PC. The configuration wizard asks for the service tools device ID and an access password. The access password protects the service tools device ID password on the PC.
When establishing a network connection, the Operations Console configuration wizard prompts you for the access password to access the encrypted service tools device ID and password. The user will also be prompted for a valid service tools user ID and password.
When you use the graphical control panel on systems with a keystick on a logical partition, setting the mode to Secure might require you to use the LPAR menu on the primary partition to select another mode.
- User authentication
- This security provides assurance as to who is using the service device. All problems related to user authentication are the same regardless of console type. For more information, see the Service tools topic.
- Data privacy
- This security provides confidence that the console data can only be read by the intended recipient. Operations Console local console directly attached to the server uses a physical connection similar to a twinaxial console or secure network connection for LAN connectivity to protect console data. Operations Console using a direct connection has the same data privacy of a twinaxial connection. If the physical connection is secure as discussed under service device authentication, the console data remains protected. To protect the data, ensure only authorized people enter the computer room.
Operations Console local console on a network uses a secure network connection if the appropriate cryptographic products are installed. The console session uses the strongest encryption possible, depending on the cryptographic products installed on the system and the PC running Operations Console. If no cryptographic products are installed, there can be no data encryption.
- Data integrity
- This security provides confidence that the console data has not changed en route to the recipient. An Operations Console local console directly attached to the system has the same data integrity as a twinaxial connection. If the physical connection is secure, the console data remains protected. An Operations Console local console on a network uses a secure network connection if the appropriate cryptographic products are installed. The console session uses the strongest encryption possible, depending on the cryptographic products installed on the system and the PC running Operations Console. If no cryptographic products are installed, there can be no data encryption.
- Data encryption
- Enhanced authentication and data encryption provide network security for console procedures. Operations Console local console on a network uses a version of SSL which supports device and user authentication but without using certificates.
Administration
Operations Console administration allows system administrators to control access to console functions, including the remote control panel and virtual control panel. When using Operations Console local console on a network, device and user authentication are controlled through the service tools device ID.
Consider the following when administering Operations Console local console over a network:
- For more information about service tools user IDs, see the Service tools topic.
- For the remote control panel, mode selections require security authorization for the user that authenticates the connection, such as that provided by QSECOFR. Mode selections include Manual, Normal, Auto, and Secure.
Auto and Secure are only available on systems with a keystick. Also, when connecting the remote control panel using a network, the service tools device ID must have authority to the control panel data on the system or on the partition that the remote control panel connects to.
- When a mismatch occurs in the service tools device password between the system and the Operations Console PC, resynchronize the password on both the PC and the system. A mismatch occurs if your PC fails,
if you decide to exchange the PC for a different one, or if you upgrade it.
- Because QCONSOLE is a default service tools device ID, if you choose not to use this device ID, it is suggested that you temporarily configure a connection using this ID and successfully connect. Then delete the configuration but do not reset the device ID on the system. This prevents unauthorized access from someone using the known default service tools device ID. If use this device ID later, you can reset it then using the control panel or menus.
- If you implement a network security tool that probes ports for intrusion protection, be aware that Operations Console uses ports 449, 2300, 2301, 2323, 3001, and 3002 for normal operations. In addition, port 2301, which is used for the console on a partition running Linux®, is also vulnerable to probes. If your tool were to probe any of these ports, it may cause loss of the console, which might result in an IPL to recover. These ports should be excluded from intrusion protection tests.
Protection tips
When using an Operations Console local console on a network, it is suggested that you complete the following tasks:
- Create an additional service tools device ID for each PC that will be used as a console with console and control panel attributes.
- Add one or two additional backup device IDs for use in an emergency.
- Choose nontrivial access passwords.
- Protect the Operations Console PC in the same manner you would protect a twinaxial console or an Operations Console with direct connectivity.
- Change your password for the following DST user IDs: QSECOFR, 22222222,
and QSRV.
- Add backup service tools user IDs with enough authority to enable or disable user and service tools device IDs.
Parent topic:
Planning considerations for your configuration
Related reference
Resynchronizing the PC and service tools device ID password
Related information
Service tools user IDs and passwords