![[Version 5 only]](../../v5app.gif)
![[Version 5 only]](../../v5app.gif)
Important distinction between Version 5.x and Version 6 applications
Note: The information in this article supports version 5.x applications only that are used with WebSphere Application Server Version 6. The information does not apply to version 6 applications.
A sample scenario
This document describes a usage scenario for Web services security.
In scenario 1, Client 1 invokes
Web services 1. Then Web services 1 calls EJB file 2. EJB file 2 calls Web services 3 and Web services 3 calls Web services 4.
Figure 1.
Propagating security tokens 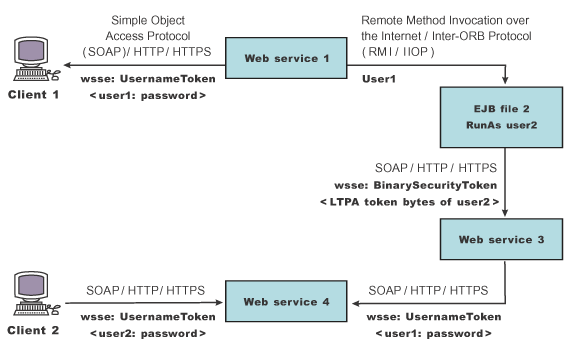 The previous scenario shows how to propagate security tokens using Web services security, the security infrastructure of the WebSphere Application Server, and Java 2 Platform, Enterprise Edition (J2EE) security.
The previous scenario shows how to propagate security tokens using Web services security, the security infrastructure of the WebSphere Application Server, and Java 2 Platform, Enterprise Edition (J2EE) security.
Web services 1 is configured to accept <wsse:UsernameToken> only and use the BasicAuth authentication method. However, Web services 4 is configured to accept either <wsse:UsernameToken> using the BasicAuth authentication method or Lightweight Third Party Authentication (LTPA) as <wsse:BinarySecurityToken>.
The following steps describe the scenario shown in the previous figure:
Web services security complements the WebSphere Application Server security run time and the J2EE role-based security. This scenario demonstrates how to propagate security tokens across multiple resources such as Web services
and EJB files.
Related concepts
Web services security specification-a chronology
Web services security and Java 2 Platform, Enterprise Edition security relationship
Web services security model in WebSphere Application Server
Security token
Configurations
Related tasks
Configuring the client for LTPA token authentication: specifying LTPA
token authentication
Configuring the client for LTPA token authentication: collecting the authentication method information
Configuring the server to handle LTPA token authentication information
Configuring the server to validate LTPA token authentication information
Configuring the client security bindings using an assembly tool
Configuring the security bindings on a server acting as a client using the administrative console
Configuring pluggable tokens using an assembly tool
Configuring pluggable tokens using the administrative console
Related reference
Web services security support