Delegation is a process security identity propagation from a caller to a called object. As per the Java 2 Platform, Enterprise Edition (J2EE) specification, a servlet and enterprise beans can propagate either the client or remote user identity when invoking enterprise beans or they can use another specified identity as indicated in the corresponding deployment descriptor. The extension supports enterprise bean propagation to the ID server when invoking other entity beans. Three types of delegations are possible:
The EJB specification only supports delegation (RunAs) at the EJB level. But an extension allows EJB method-level RunAs specification. With an EJB method level, the RunAs specification you can specify a different RunAs role for different methods within the same enterprise beans.
The RunAs specification is detailed in the deployment descriptor, the ejb-jar.xml file in the EJB module and the web.xml file in the Web module. The extension to the RunAs specification is included in the ibm-ejb-jar-ext.xmi file.
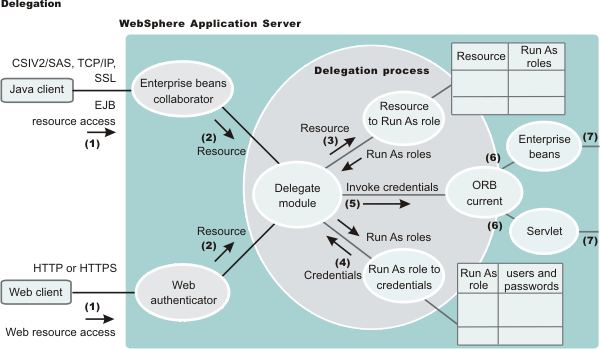
An IBM-specific binding file is available for each application that contains a mapping from the RunAs role to the user. This file is specified in the ibm-application-bnd.xmi file. These specifications are read by the run time during application startup. The following figure illustrates the delegation mechanism, as implemented in the WebSphere Application Server security model.

Delegation Process Two tables help in the delegation process:
Use the Resource to RunAs role mapping table to get the role that is used by a servlet or by enterprise beans to propagate to the next enterprise beans call.
Use the RunAsRole to user ID and password mapping table to get the user ID that belongs to the RunAs role and its password.
Delegation is performed after successful authentication and authorization. During this process, the delegation module consults the Resource to RunAs role mapping table to get the RunAs role (3). The delegation module consults the RunAs role to user ID and password mapping table to get the user that belongs to the RunAs role (4). The user ID and password is used to create a new credential using the authentication module, which is not shown in the figure. The resulting credential is stored in the ORB Current as an invocation credential (5). Servlet and enterprise beans when invoking other enterprise beans pick up the invocation credential from the ORB Current (6) and call the next enterprise beans (7).
Related concepts
Authorization technology