IBM Maximo Asset Monitor
The IBM IIoT platform provides a way to model the device hierarchy integrated as part of a solution and to acquire information from those devices by using industry standard protocols. The platform is based on IBM Maximo Asset Monitor and related IBM Cloud services. After the information is acquired, it can be transformed as needed and stored in an IoT data lake to support dashboards and analytics to meet industry-specific needs by using predefined applications and tailored industry solutions.
Monitor a wide range of "things"
- Logistics and supply-chain management to track physical objects, such as packages and containers
- Smart buildings that are monitored and have control systems to manage their operations
- Smart homes where heating and the operation of appliances is remotely controlled
- Connected vehicles that provide information about road conditions and vehicle status to drivers
- Medical applications that allow patients to be remotely monitored
- Retail applications that use information about a customer to tailor marketing and purchase suggestions
- Devices such as thermometers and accelerometers measure real-world characteristics and generate numerical measurement information.
- Cameras and microphones create streams of video and audio information that contain more complex information about the world.
- Beacons and load sensors, Actuators such as relays that switch equipment on or off or indicate when a device reports something abnormal.
- Occupancy sensors, or wifi detection of personnel entry or exit, can be used to monitor location metrics.
- Production equipment, such as robots and stamps, providing operational and performance metrica.
- Vehicles, such as aircraft and automobiles, that include sensors that provide operational and performance metrics.
Opportunities
- Connect and manage devices, networks, and gateways
- Integrate structured and unstructured information from devices, people, the weather, and the world
- Gain insights from information by using near real-time streaming, predictive, edge, and cognitive analytics
- Manage the IoT landscape, manage risk, and gain trusted sources of IoT data with technology such as blockchain
- Automate smart processes using cognitive, analytics, security, and cloud.
Architecture
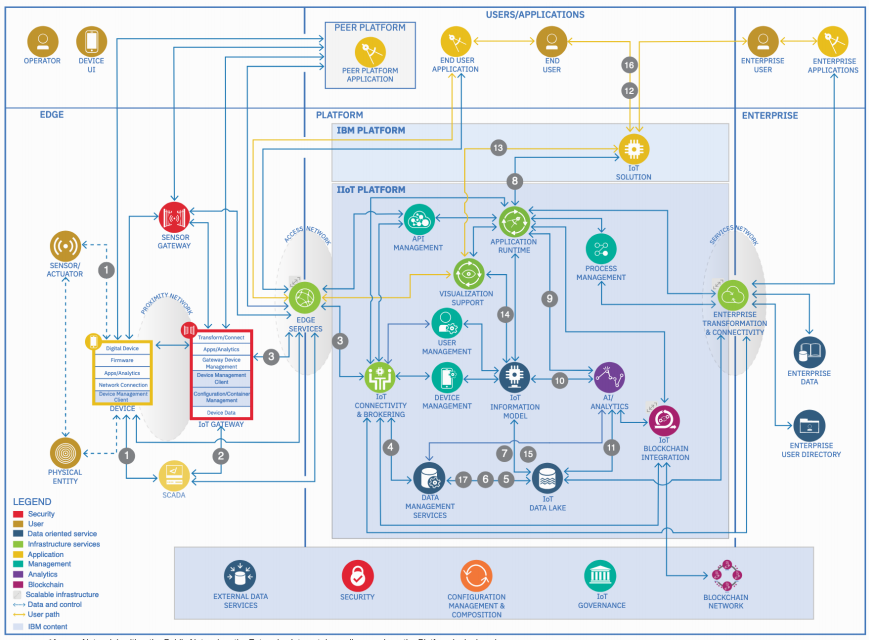
- Sensor data flows from a sensor in or around a building to the supervisory control and data acquisition (SCADA) system that controls process equipment. The sensor is connected to the SCADA system by using either a wireless or wired device protocol, such as RS 485.
- The SCADA system exposes data to the outside world by using an Operational Technology (OT) protocol, such as Modbus TCP. If needed, sensor data can be converted to another format before transmission. Energy data is transferred to the IoT gateway by reading mapped data and OT protocol.
- If needed, the IoT gateway filters sensor data, such as time interval, aggregating, and averaging, and converts it to the format that the IoT solution needs. The IoT gateway makes a secure connection to the IoT platform by using TLS and transmits the energy data to the platform by using MQ Telemetry Transport (MQTT).
- Raw inbound sensor data is picked up by the data management services for disposition.
- Raw data is stored in the data lake in the format in which it is received.
- Based on configuration, data is periodically reorganized in the data lake to support analytics.
- The information model is used to provide context for the location of the devices within the enterprise. That context is used to establish tables within IBM Db2 to organize the data.
- The execution of the analytics model is periodically triggered to evaluate updated device data. Results are stored in the data lake. The execution model can also be automatically triggered based on events received in Internet Open Trading Protocol (IOTP).
- The execution of the analytics model is periodically triggered to evaluate updated device data. Results are stored in the data lake.
- The analytics model uses the information model to provide context for the asset predictions; for example, expected time to failure.
- Asset predictive results are stored in the data lake.
- A user of the IoT solution accesses the user interface to view asset data and related analytics results.
- A user of the IoT solution accesses the user interface to view asset data and related analytics results
- The information model is used to provide context for the location of the assets and devices within the enterprise and the corresponding data.
- The information model context is used to access information in the data lake that will be displayed for the devices in context.
- The IoT solution user sees that an asset was or will be out of tolerance and dispatches a maintenance technician to investigate the problem. The maintenance technician finds that a piece of equipment is failing and addresses the issue.
- Based on configuration, data is periodically moved from Db2 to an object store as part of the long-term data archival process.
Nonfunctional requirements
Performance
| Function offload to the edge | The system must have a centralized configuration with offload to the edge for rules-based decision-making and streaming analytics. |
| Hybrid cloud | It must be possible to deploy the platform layer on premises, in the cloud, or part on premises and part in the cloud. |
| Modular design | The microservices orientation allows for the modular design of IoT solutions. |
| Unstructured and structured data | The system must handle structured data, both real-time messages and bulk transfer, and unstructured data, including acoustic files, image files, recordings, and text documents. |
| User response time | The system must provide acceptable response times to users regardless of the volume of data that is stored and the analytics that occurs in background. |
| Real-time communications (request/response) | Bidirectional, near real-time communications must be supported. This requirement is related to the requirement to support industrial and device protocols at the edge. Responses might need to happen in 1 second or less depending on the use case. This requirement also drives a need for edge-level analytics and decision-making for that class of use cases. |
| Time-series capture granularity | A timestamp to at least the millisecond is required so that even if the data is too late for real-time control, the catch-up analytics can see the sequence of events. |
Scalability
| Horizontal scalability | The system must handle expanding load and data retention needs that are based on the upscaling of the solution scope, such as extra manufacturing facilities and extra buildings. |
Security
| Data security | All persisted data requires secure access. |
| Device security | Devices must register and communicate securely, such as by using transport layer security (TLS). Unauthorized devices are prohibited. |
| User security | User logon to any device must be secure and validated for each role. This security must be attached to the LDAP or user registry that customers use. |
| Application security | Authorized users of the system who exchange information must be able to do so with appropriate security controls. |
Usability
| Mobile support | Users must be able to interact in the same roles and on the same tasks on computers and mobile devices where practical, given mobile capabilities. |
Manageability
| Incident management | The system must include support for alerting, notification, and incident management. |
| Solution management | The system must support centralized solution management so that system's support personnel can determine the root cause of a problem and fix it to avoid downtime. |
Availability
| High availability (HA) | Some IoT solutions and domains demand highly available systems for 24x7 operations. That said, this type of system isn't a critical production application, which means that operations or production don't go down if the IoT solution is down. |
Maintainability
| Adaptable and flexible | It must be possible, and relatively easy, to rapidly adapt the system to a change in processes, participants, or information that is exchanged. |
| Maintainability and uptime | It must be possible to perform maintenance on the system without violating service level agreements (SLAs) for uptime. In a 24x7 environment, we can't take down the system completely to perform maintenance. |
Volumetrics
| Big data | The system must store and analyze volumes of data, both historical and current, on scales that are commonly known as big data. |
| Platform speed, capacity, and accessibility | The platform must support high volumes of near real-time data transmissions 24x7. This requirement includes support for remote locations and mobile data sources. |
See