Configure a single, LDAP repository in a new configuration under Federated repositories
To configure an LDAP repository in a new configuration under Federated repositories, have a user name (ID), the user password, the server host and port and, if necessary, the bind distinguished name (DN) and the bind password. We can choose any valid user in the repository that is searchable. In some LDAP servers, administrative users are not searchable and cannot be used (for example, cn=root in SecureWay). This user is referred to as the WebSphere Application Server administrative user name or administrative ID in the documentation. Being an administrative ID means a user has special privileges when calling some protected internal methods. Normally, this ID and password are used to log in to the administrative console after turning on security. Use other users to log in, if those users are part of the administrative roles.
Tasks
- In the administrative console, click...
-
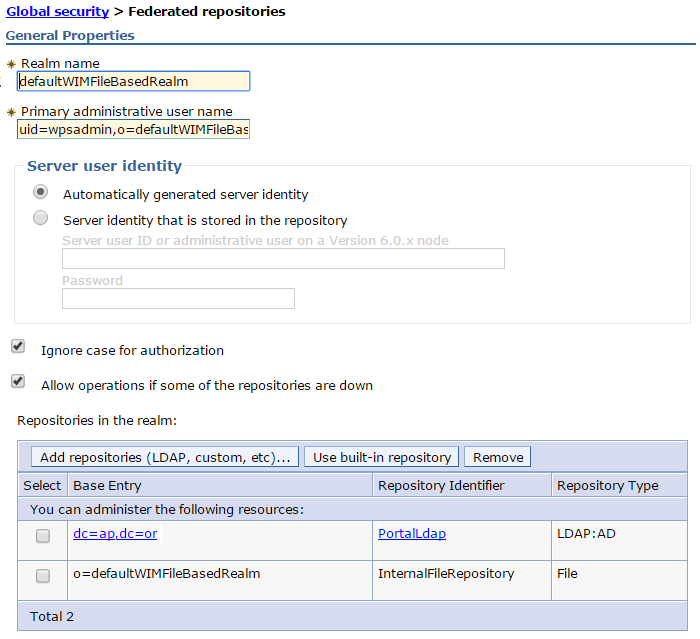
Security > Global security > User account repository > Available realm definitions > Federated repositories > Configure
To configure for a specific domain in a multiple security domain environment, click...
-
Security domains > domain_name > Security Attributes > User Realm > Customize for this domain > Realm type > Federated repositories > Configure
- On the Federated repositories panel:
- Enter the name of the realm in the Realm name field. We can change the existing realm name.
- Enter the name of the primary administrative user in the Primary administrative user name field, for example, adminUser.
- Optional: Select the Ignore case for authorization option. When we enable this option, the authorization check is case-insensitive. Normally, an authorization check involves checking the complete DN of a user, which is unique in the realm and is case-insensitive. Clear this option when all of the member repositories in the realm are case-sensitive.
Restriction: Some repositories contain data that is case-sensitive only, and some repositories contain data that is case-insensitive only. Do not include both case-sensitive and case-insensitive repositories in the realm. For example, do not include case-sensitive repositories in the realm with a built-in, file-based repository.
- Leave the Allow operations if some of the repositories are down option cleared.
- Optional: In a multiple security domain environment, select Use global schema for model option to indicate that the global schema option is enabled for the data model. Global schema refers to the schema of the admin domain.
- Click Add base entry to realm to add a base entry that uniquely identifies the external repository in the realm. Then complete the steps in Add an external repository in a federated repository configuration.
- On the Federated repositories panel:
- Select the built-in, file-based repository in the collection,
and click Remove.
Restriction: Before you remove the built-in, file-based repository from the administrative realm, verify that at least one user in another member repository is a console user with administrative rights. Otherwise, disable security to regain access to the administrative console.
- Click OK.
- Select the built-in, file-based repository in the collection,
and click Remove.
After completing these steps, the new configuration under Federated repositories includes a single, LDAP repository only.
What to do next
- Before we can manage this account with Users and Groups, configure supported entity types as described in Configure supported entity types in a federated repository configuration.
- After configuring the federated repositories, click Security > Global secuity to return to the Global security panel. Verify that Federated repositories is identified in the Current realm definition field. If Federated repositories is not identified, select Federated repositories from the Available realm definitions field and click Set as current. To verify the federated repositories configuration, click Apply on the Global security panel. If Federated repositories is not identified in the Current realm definition field, the federated repositories configuration is not used by WebSphere Application Server.
- If we are enabling security, complete the remaining steps as specified in Enable WebSphere Application Server security. As the final step, validate this setup by clicking Apply in the Global security panel.
- Save, stop, and restart all the product servers (deployment managers, nodes and Application Servers) for changes in this panel to take effect. If the server comes up without any problems, the setup is correct.
Related tasks: