Secure downstream JAX-RS resources
We can secure downstream Java API for RESTful Web Services (JAX-RS) resources by configuring the BasicAuth method for authentication and using the LTPA JAX-RS security handler to take advantage of single sign-on for user authentication.
This task assumes that we have completed the following steps:
- We have defined to the application server a cell profile that is federated into the deployment manager cell.
- We have installed the JAX-RS application onto the application server.
- We have enabled security for our JAX-RS application.
- We have secured the JAX-RS applications within the web container by configuring downstream JAX-RS applications to use the basic authentication (BasicAuth) method for user authentication.
When composing JAX-RS resources, a new LTPA JAX-RS security handler can be used to authenticate on downstream resource invocations.
When invoking downstream secure JAX-RS resources, the calling application is required to authenticate to the target resource. If the target resource on a downstream server uses the BasicAuth method for security, the calling application can take advantage of single sign-on (SSO) for JAX-RS resources. Using single sign-on, an authenticated context is propagated along downstream calls. We can use the LTPA-based security client handler to authenticate to downstream resources that are distributed across servers of a cell environment.
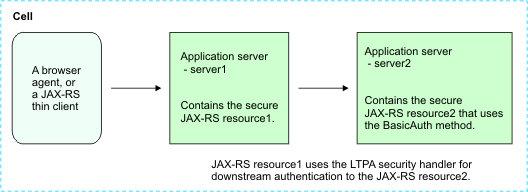
To illustrate this scenario, assume that we have two servers in your cell and that we have deployed JAX-RS resources on both of these servers. Suppose from one resource on server1 we need to invoke another resource that is deployed on server2. When server2 resources are secured using the BasicAuth method for authentication, use the LTPA JAX-RS security handler to take advantage of single sign-on and seamlessly propagate user authentication on downstream calls without having to provide or manage user identities and passwords in the application.
Figure 1. Securing JAX-RS downstream resources
Use the following steps to configure user authentication to a downstream server using the JAX-RS security handler at application build time.
Tasks
- At application build time, use the LTPA-based security client handler, LtpaAuthSecurityHandler, to authenticate to downstream resources that are distributed across servers of a cell environment.
-
For JAX-RS 1.1, when using the LtpaAuthSecurityHandler class, ensure that you target resources using the https scheme for our URLs, and that the target application is SSL-enabled. It is highly recommended to use SSL connections when sending user credentials, including LTPA cookies. You may explicitly turn off the requirement for SSL in the LtpaAuthSecurityHandler class by invoking the setSSLRequired method on the security handler with the false value. Default is true.
- yourLtpaAuthSecHandler.setSSLRequired(false);
- For JAX-RS 2.0, we can use the com.ibm.ws.jaxrs.client.ltpa.handler client
property to set SSO cookie and set the value to true:
ClientBuilder cb = ClientBuilder.newBuilder(); Client c = cb.build(); c.property("com.ibm.ws.jaxrs.client.ltpa.handler", "true"); WebTarget t = c.target("http://" + serverIP + ":" + serverPort + "/" + moduleName + "/ComplexClientTest/ComplexResource"); String res = t.path("echo1").path("test1").request().get(String.class); c.close(); ret.append(res);
-
- Add the security handler to the handlers chain.
- Create the REST client instance.
- Create the resource instance to interact with.
- Substitute a value representing your resource address.
We have defined secure JAX-RS resources within the cell environment such that when downstream resources are invoked, we can use single sign-on and seamlessly propagate user authentication on downstream calls without having to provide or manage user identities and passwords in the application.
Example
For JAX-RS 1.1, the following code snippet demonstrates how to use this security handler that is packaged as part of the JAX-RS client.
import org.apache.wink.client.Resource;
import org.apache.wink.client.RestClient;
import org.apache.wink.client.ClientConfig;
import org.apache.wink.client.handlers.LtpaAuthSecurityHandler;
ClientConfig config = new ClientConfig();
LtpaAuthSecurityHandler secHandler = new LtpaAuthSecurityHandler();
// Add this security handler to the handlers chain.
config.handlers(secHandler);
// Create the REST client instance.
RestClient client = new RestClient(config);
// Create the resource instance to interact with.
// Substitute a value representing your resource address
resource =
client.resource("http://localhost:8080/path/to/resource");
// Now we are ready to begin calling your resource.
For JAX-RS 2.0, the following code snippet demonstrates how to use this security handler that is packaged as part of the JAX-RS client.
ClientBuilder cb = ClientBuilder.newBuilder();
Client c = cb.build();
c.property("com.ibm.ws.jaxrs.client.ltpa.handler", "true");
String res = "";
res = c.target("http://" + serverIP + ":" + serverPort + "/" + moduleName + "/rest/ltpa")
.request()
c.close();
return res;